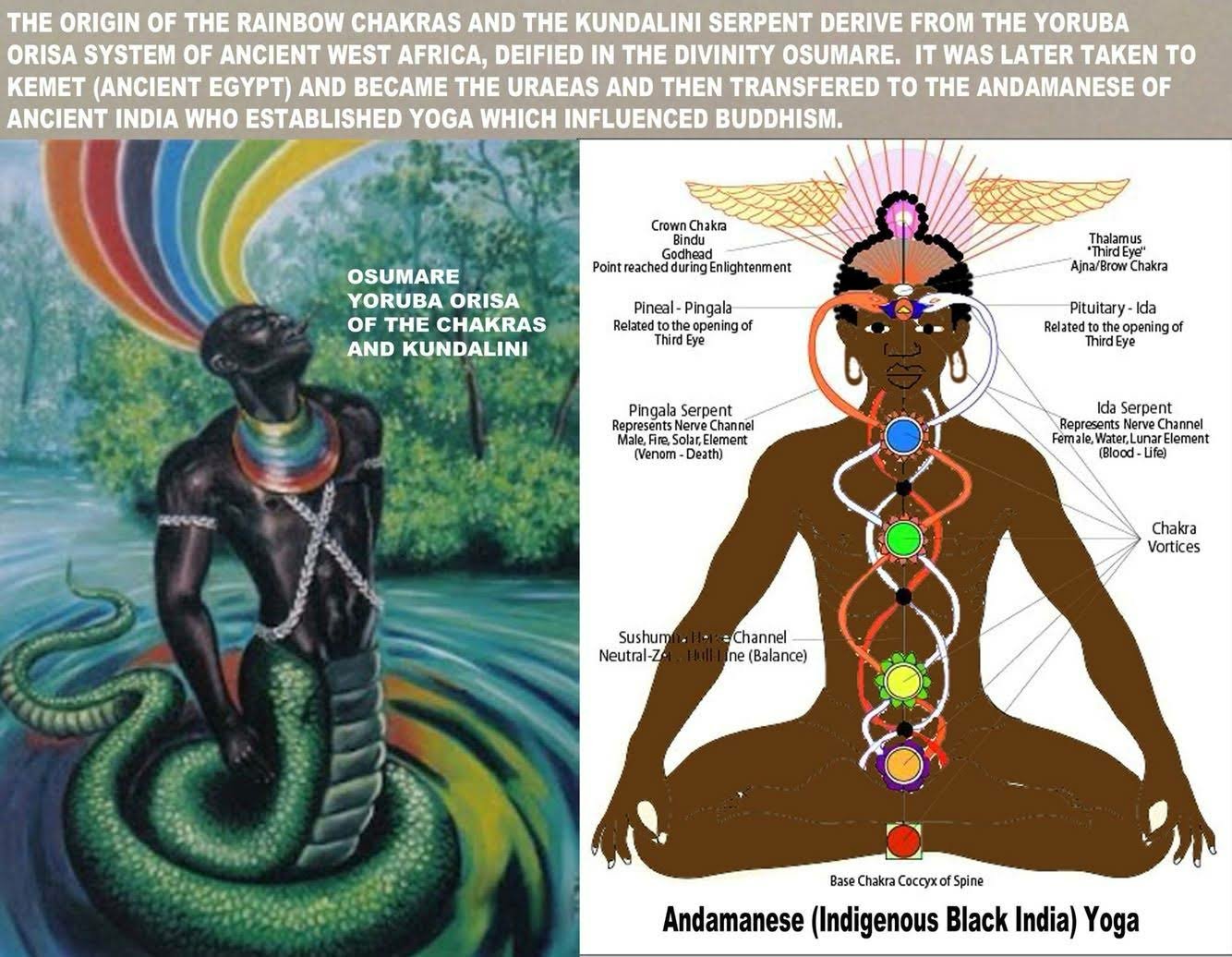
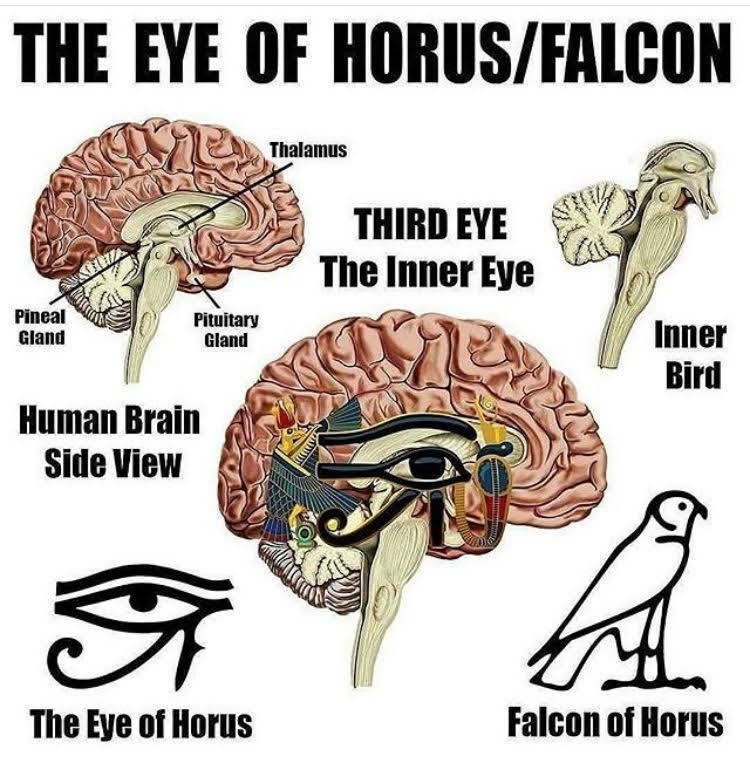
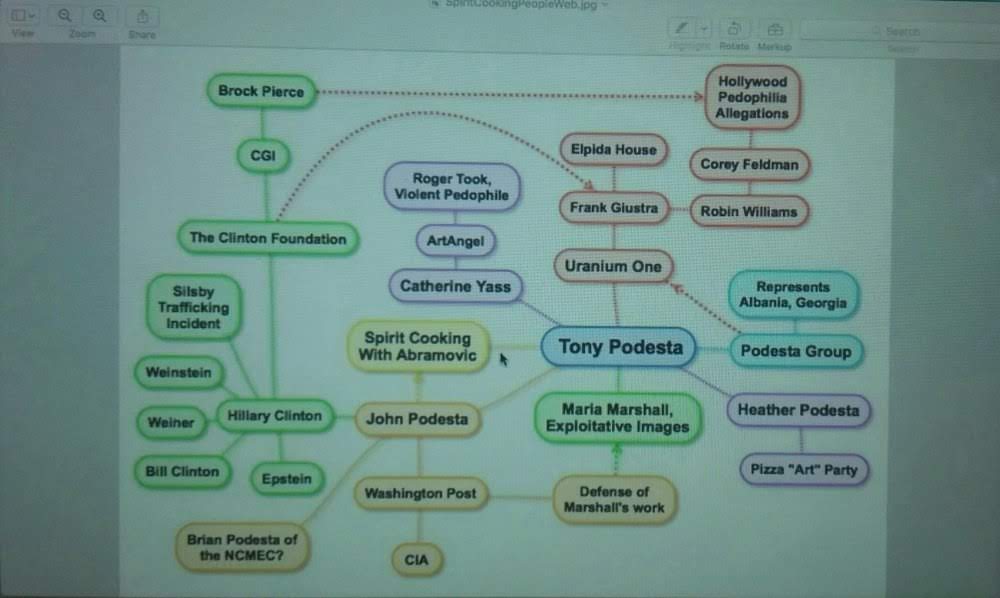
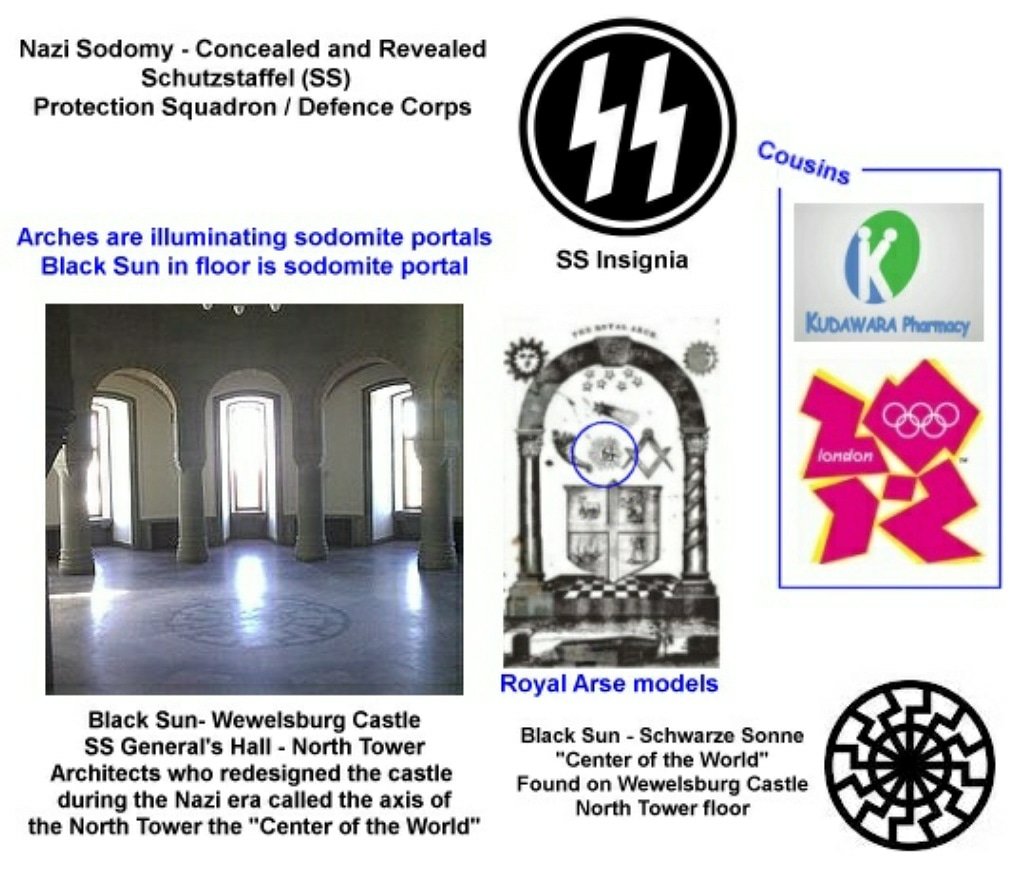
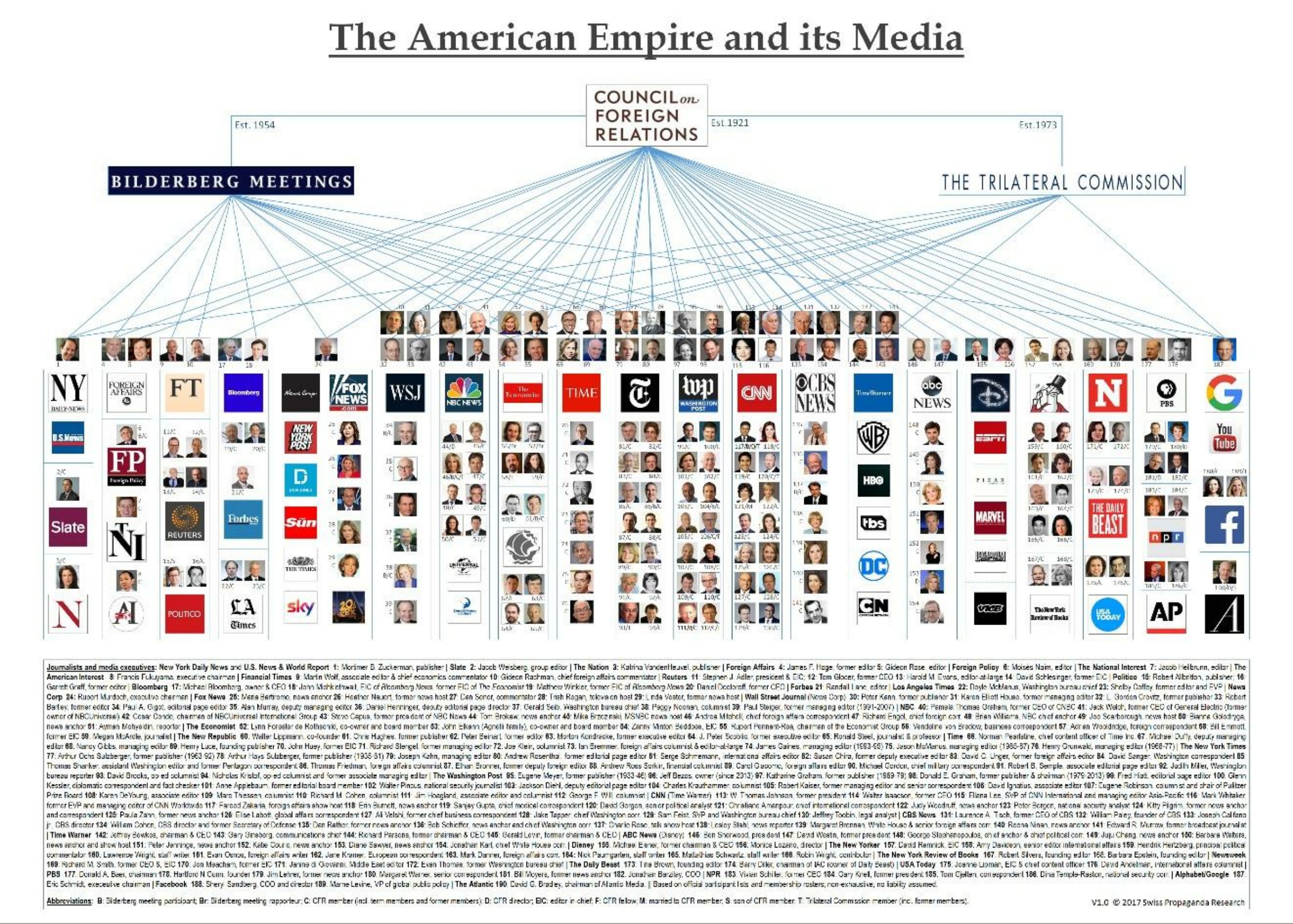
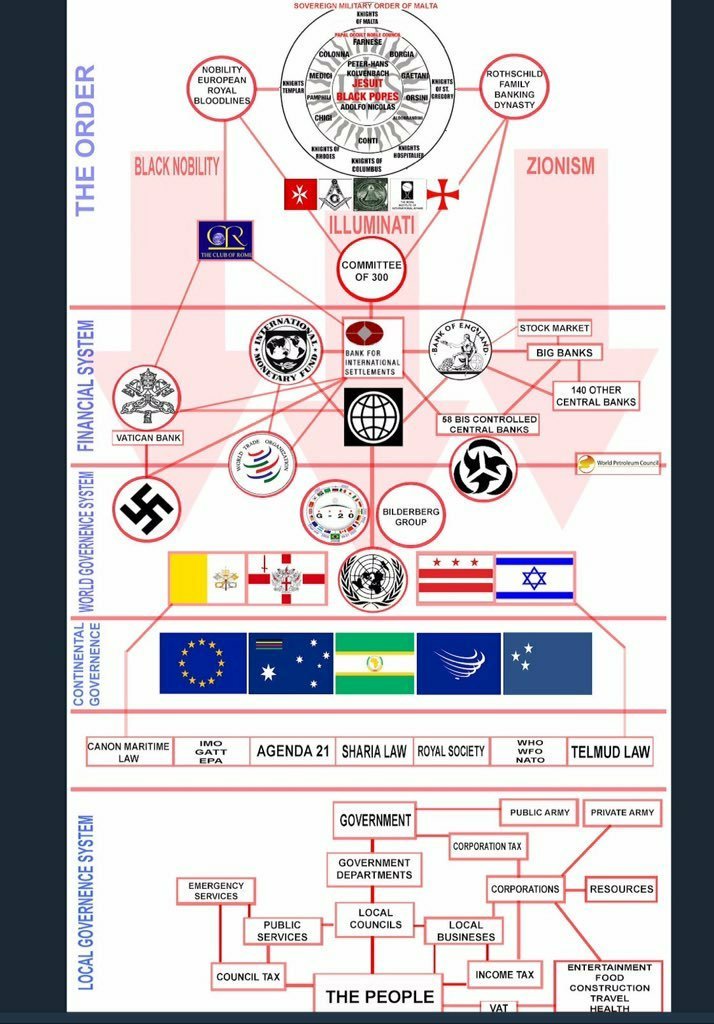
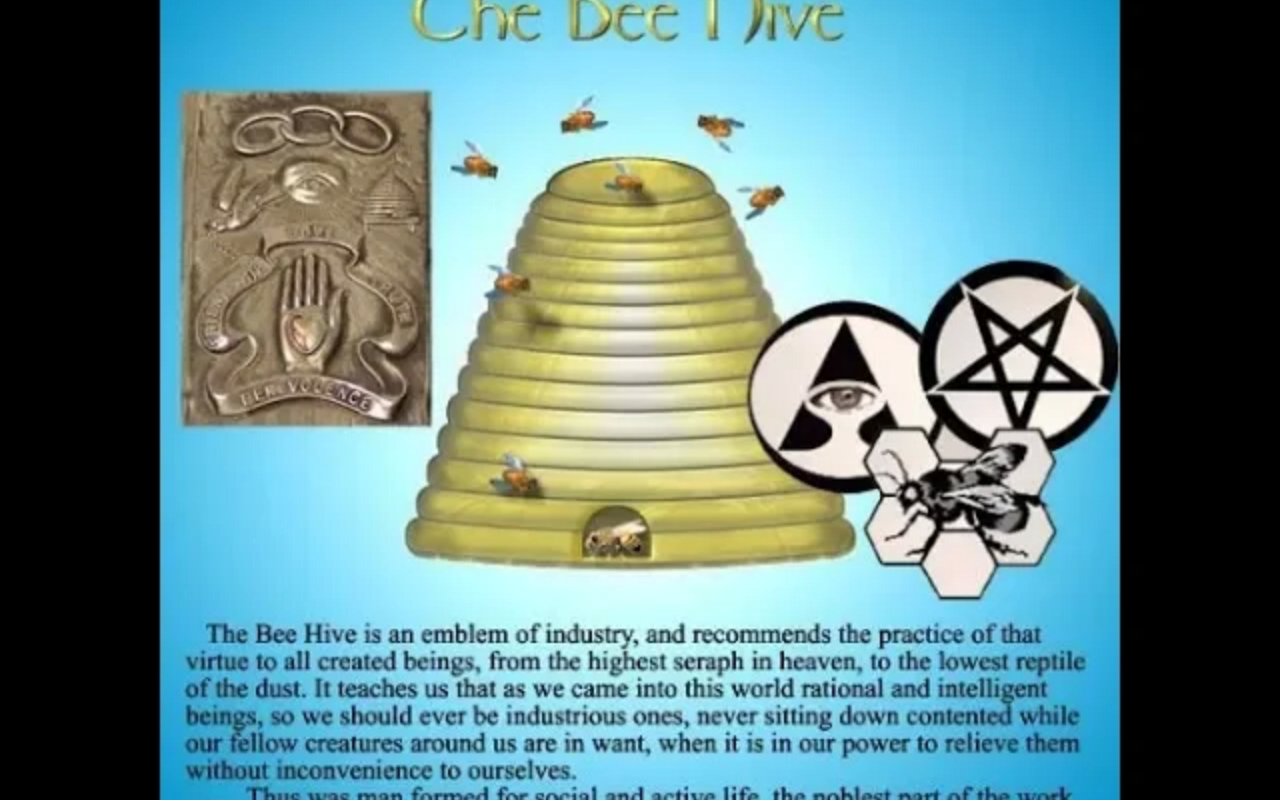
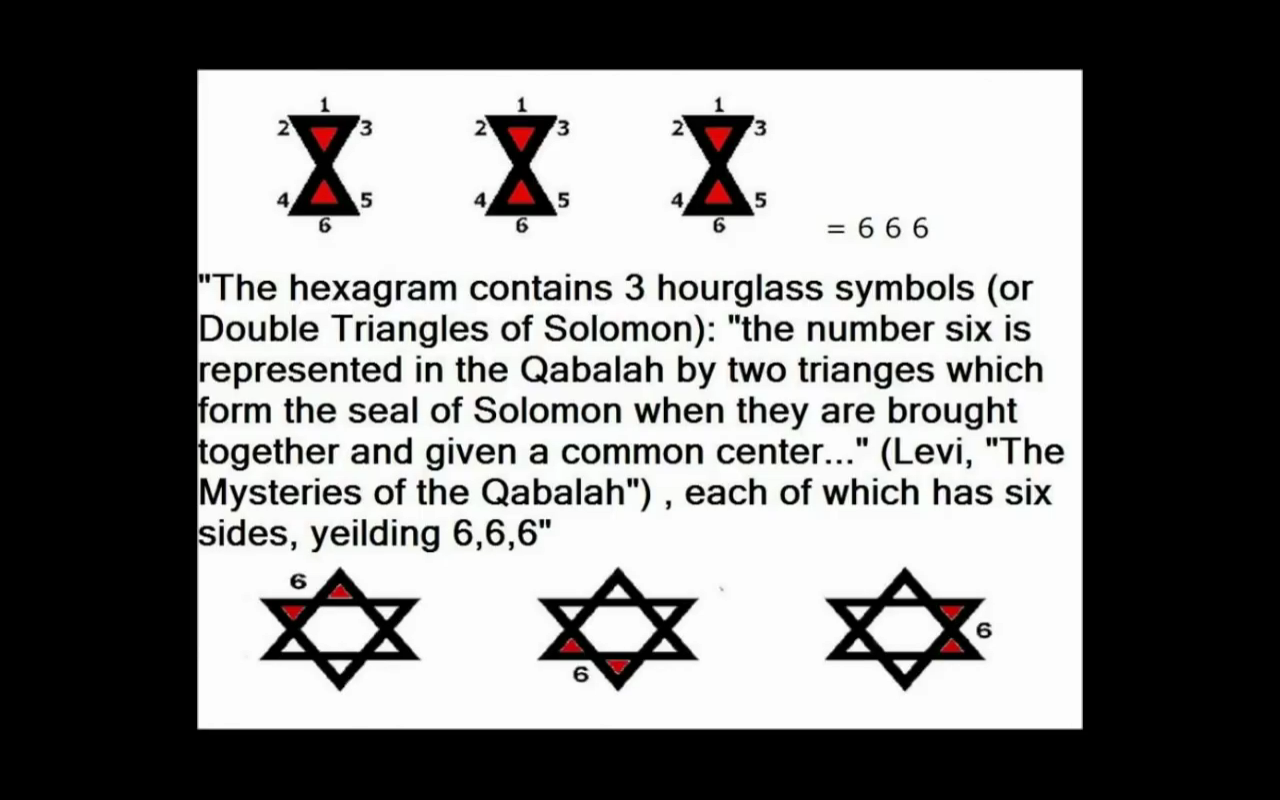
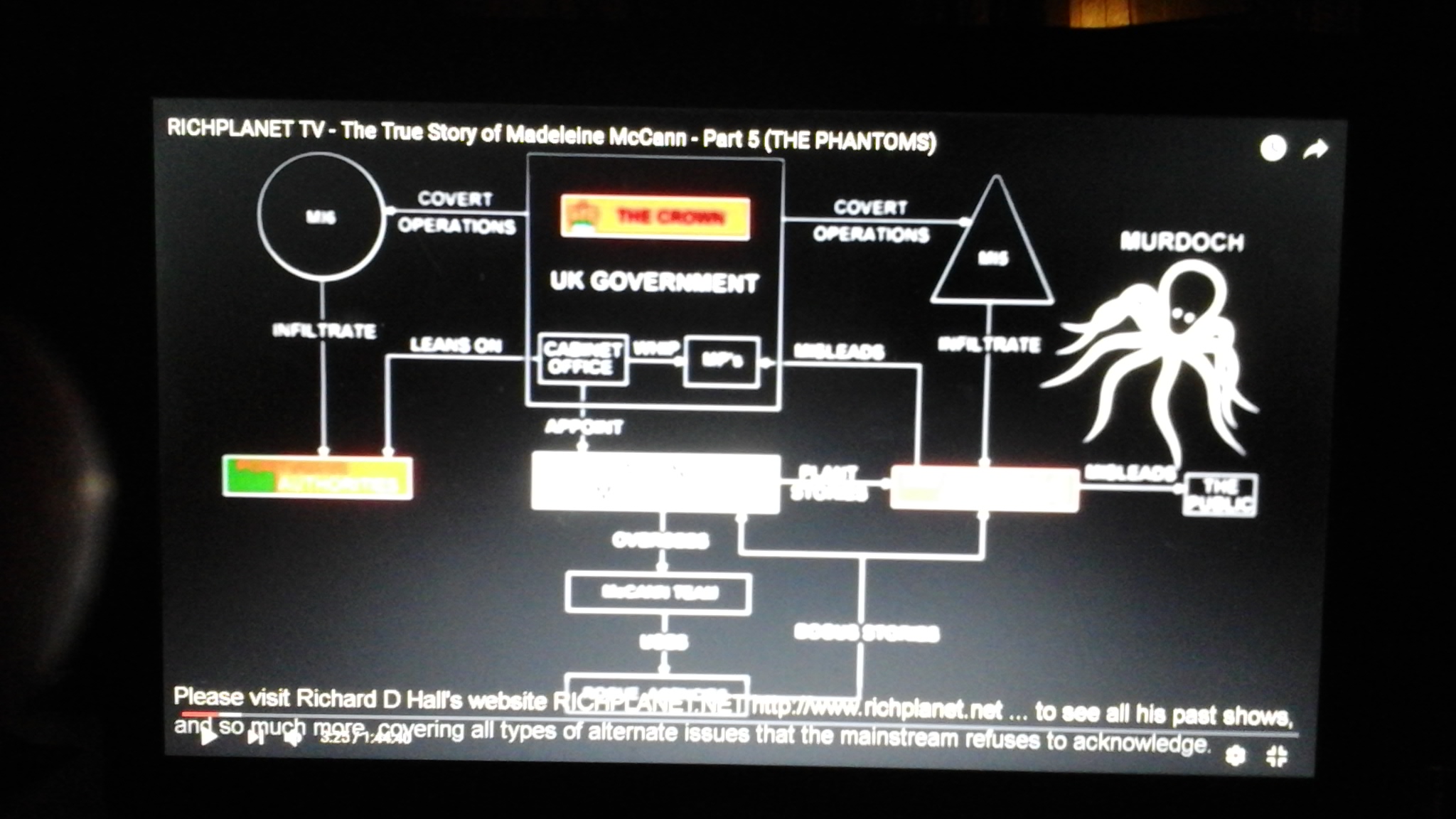
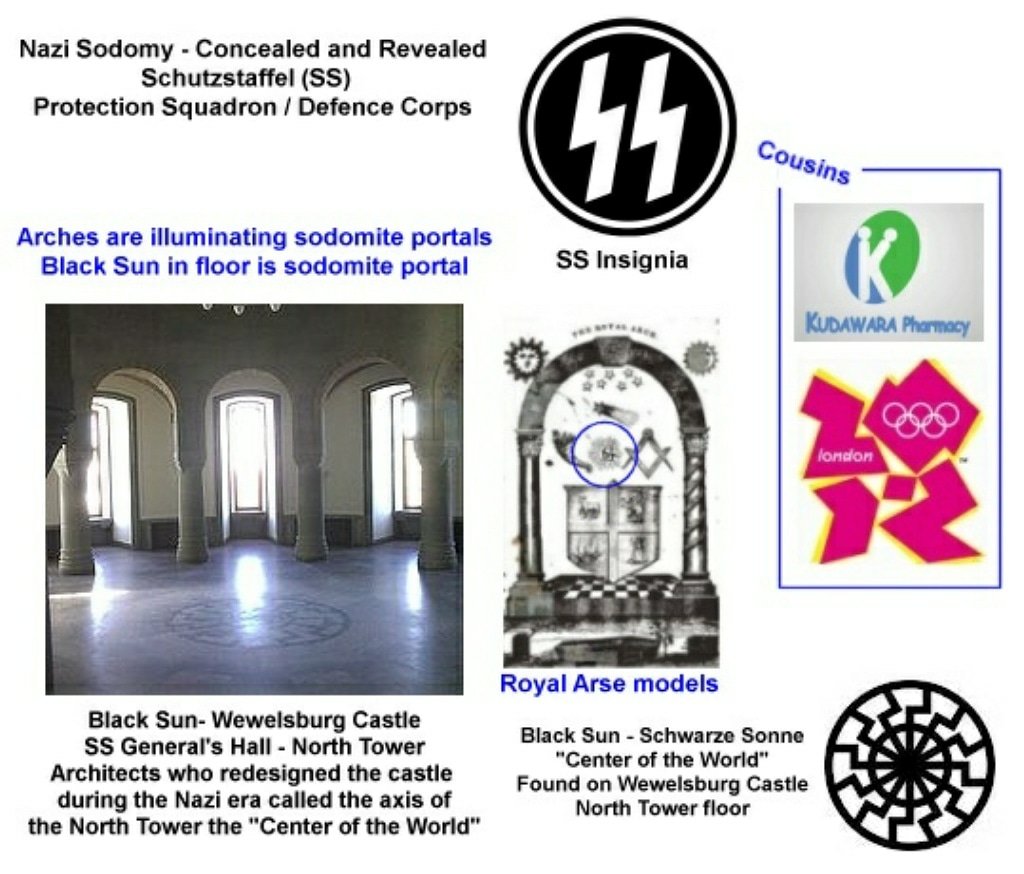
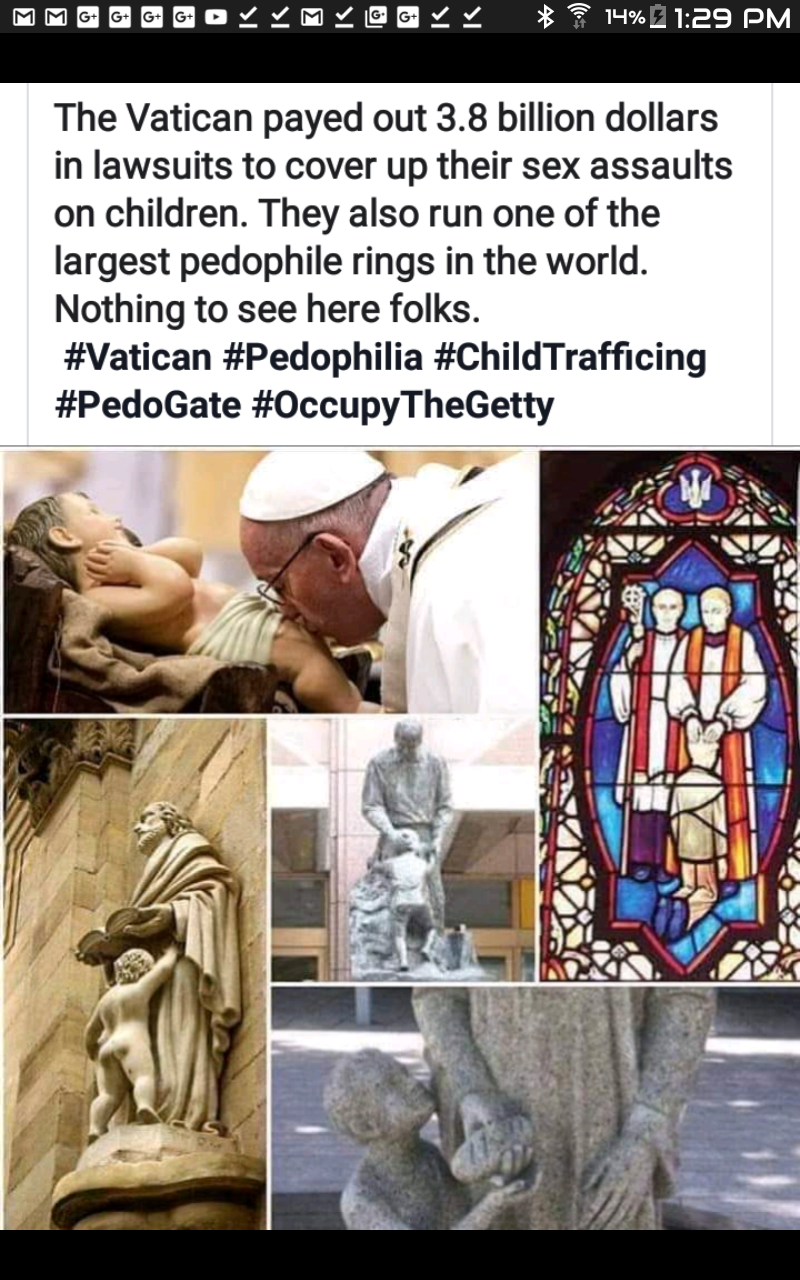
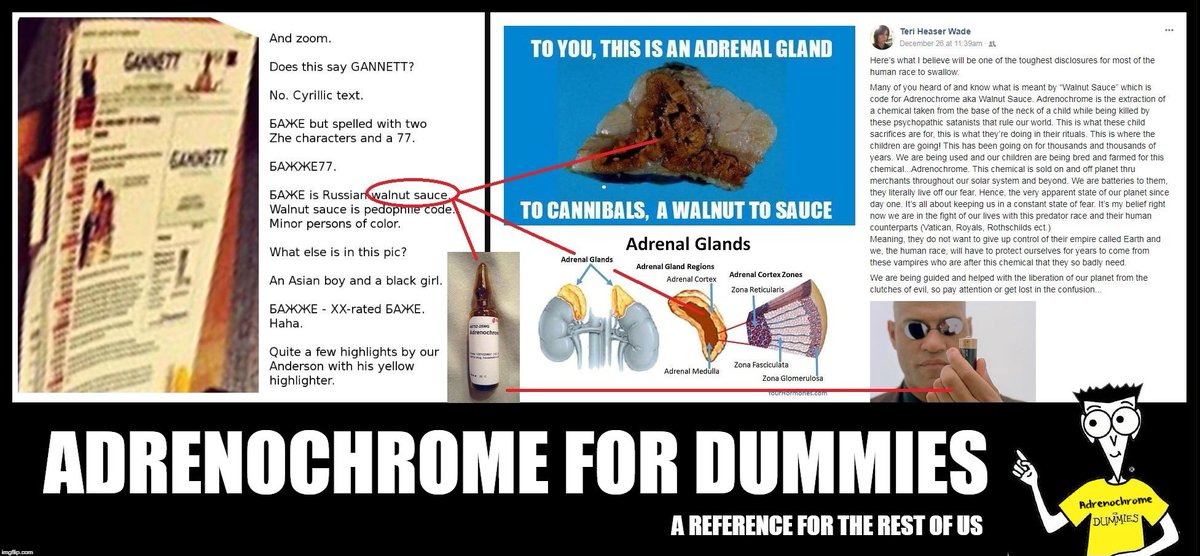
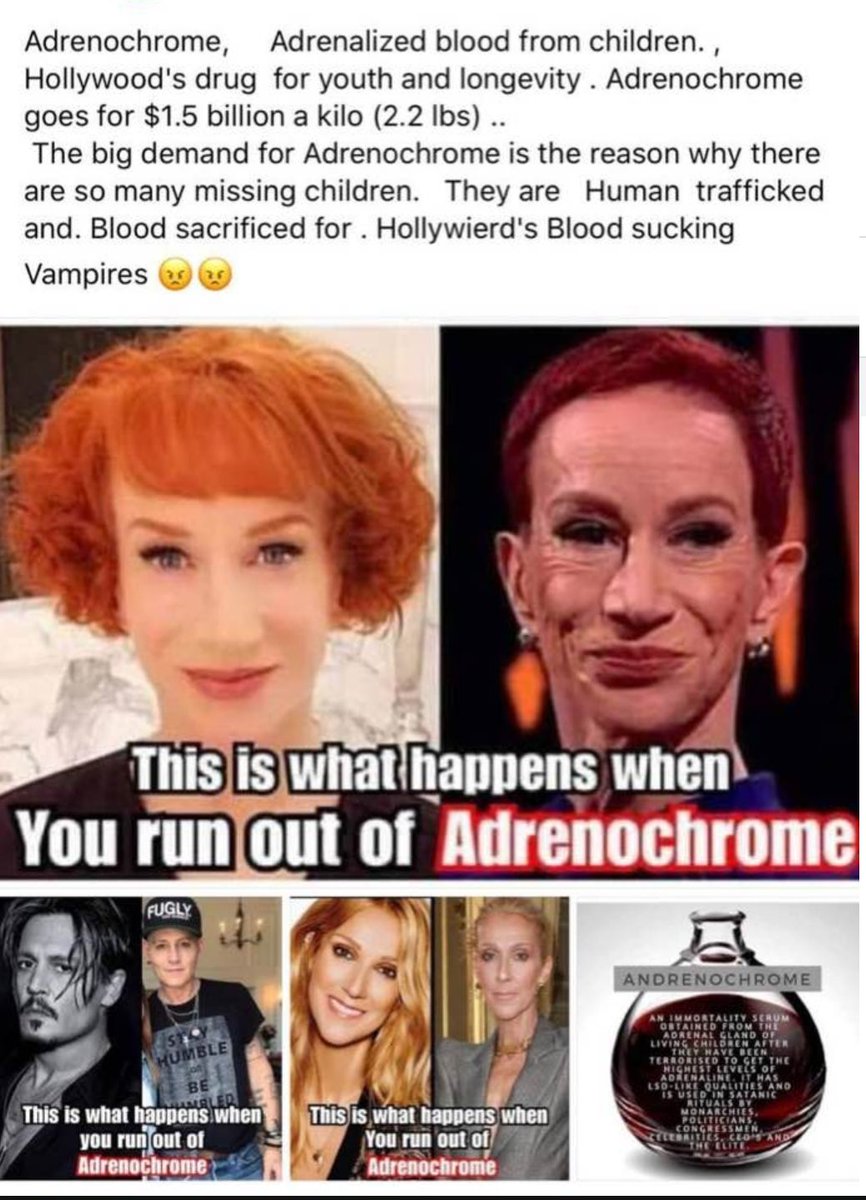
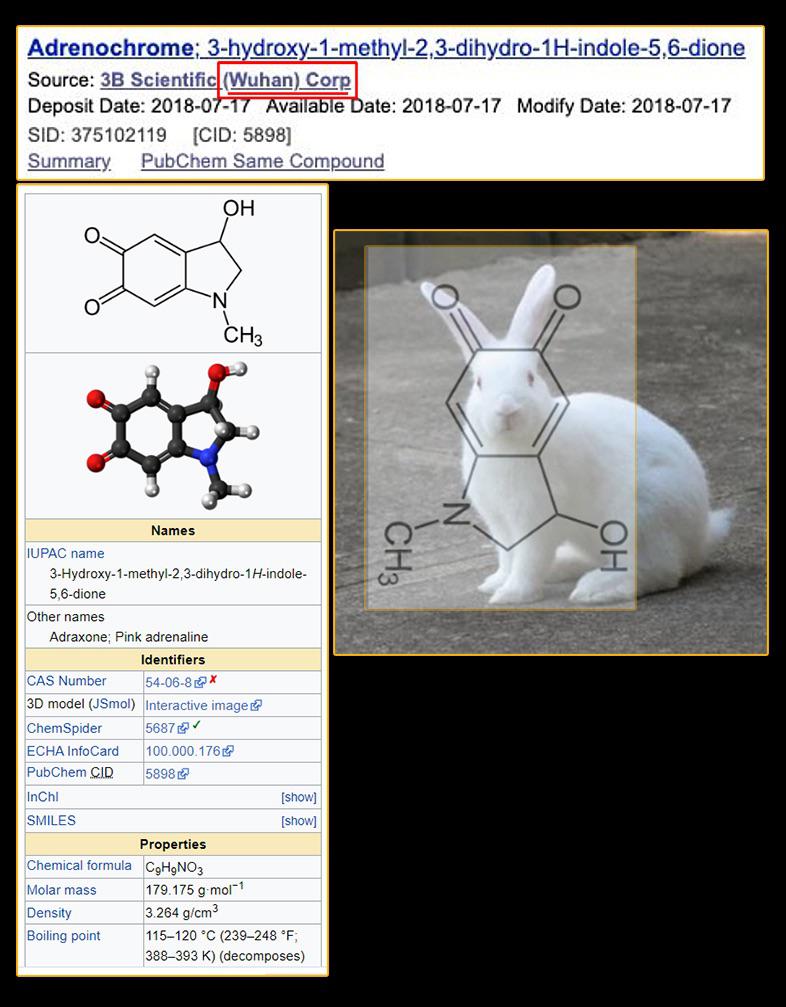
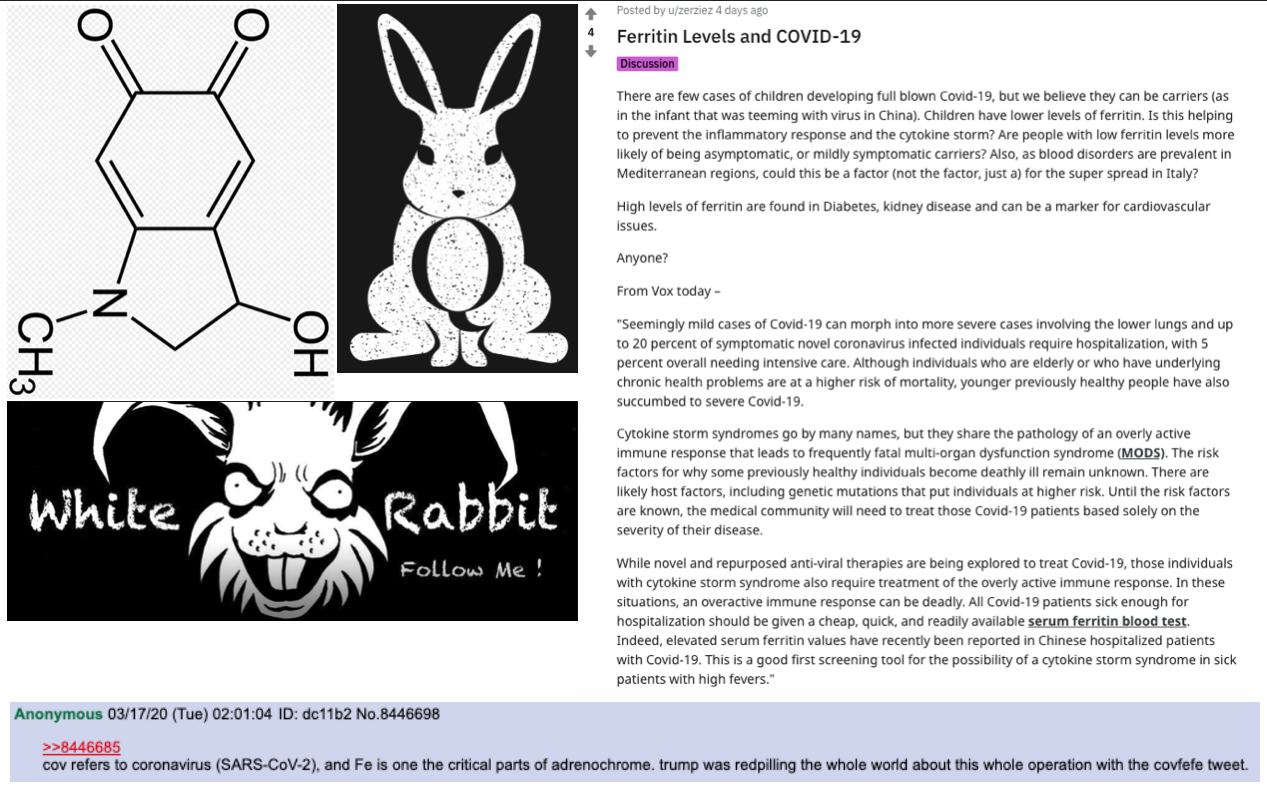
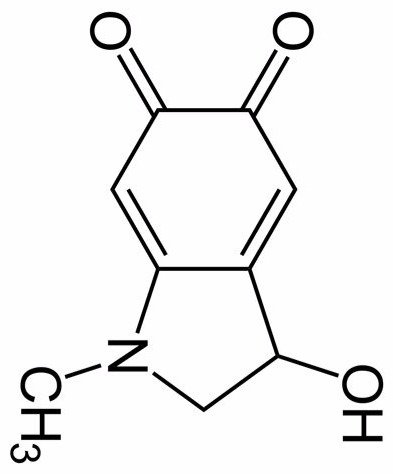
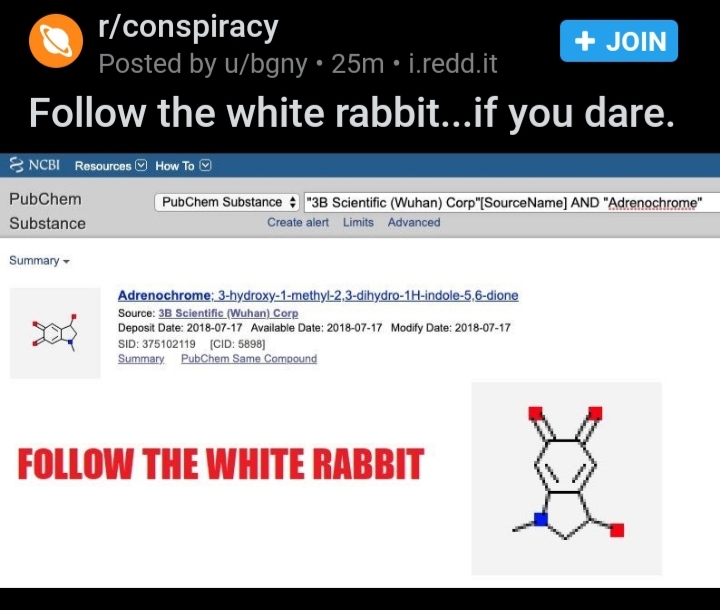
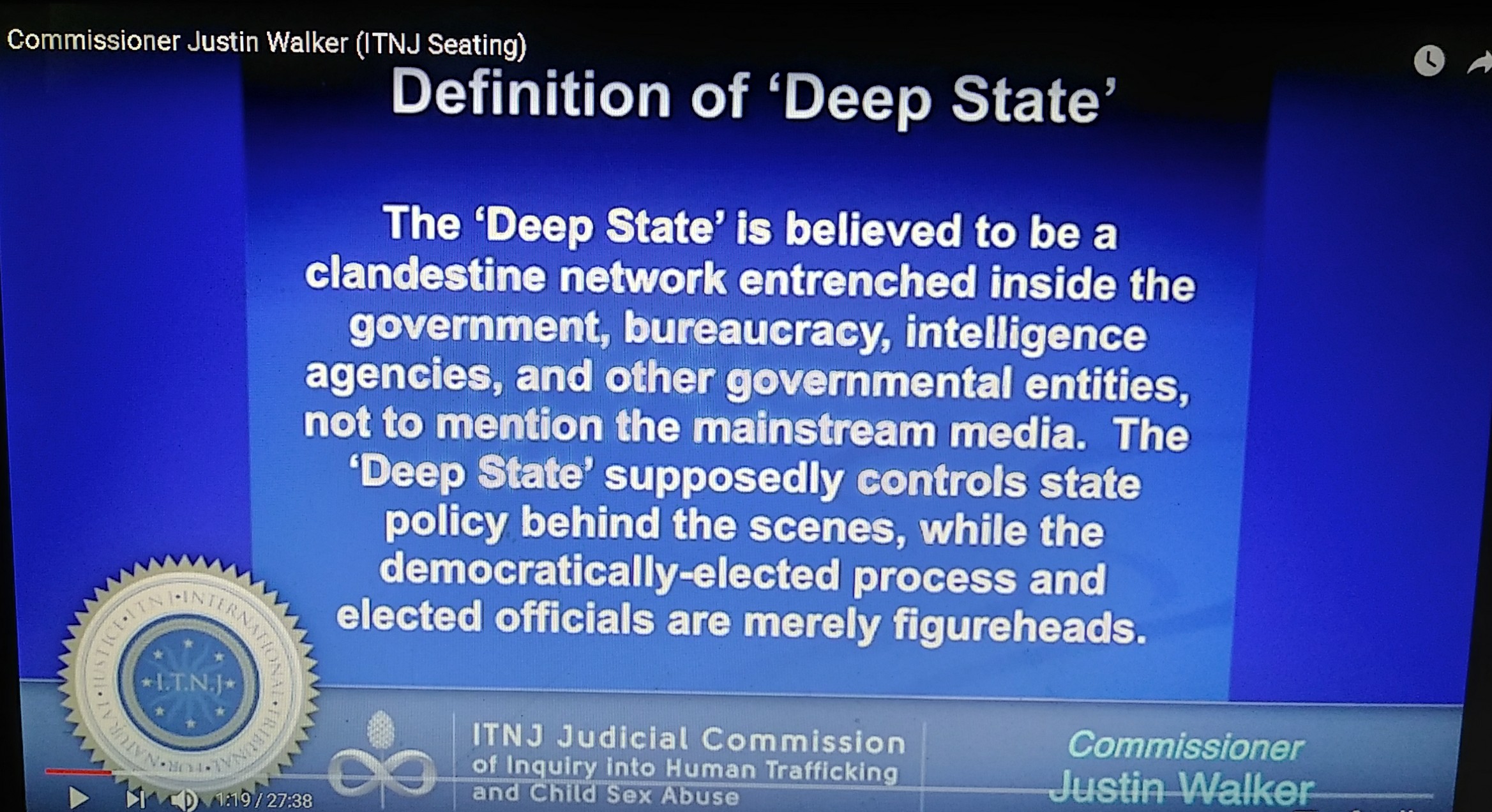
PEDOGATE: Women Operatives In Very High Places
Covert Anglo-American Network of “Crown Agents’ Sisters” Revealed
Abel Danger Mischief Makers – Mistress of the Revels – ‘Man-In-The-Middle’ Attacks
Posted: MONDAY, FEBRUARY 22, 2010
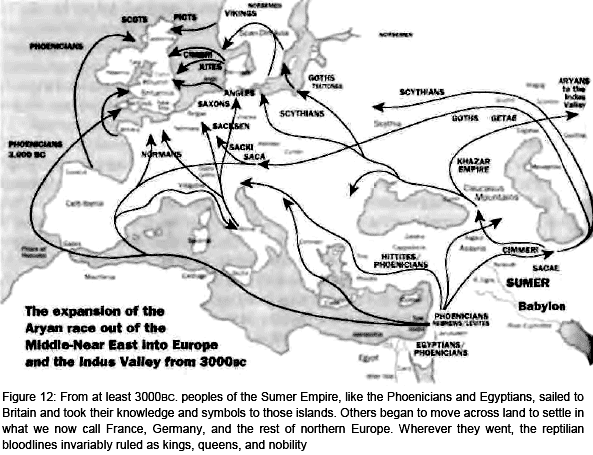
List (September 15, 2011), of Crown Agents’ Sisters who allegedly use pedophile extortionists and snuff-film patent pools to support ‘man-in-the-middle’ attacks on leaders with an M.O. of Matrix 5 communities (see Marcy below) and command, contract hit and spoliation crews that dates back to the 1629 foundation of the Worshipful Company of Spectacle Makers:
Mistress of the Revels
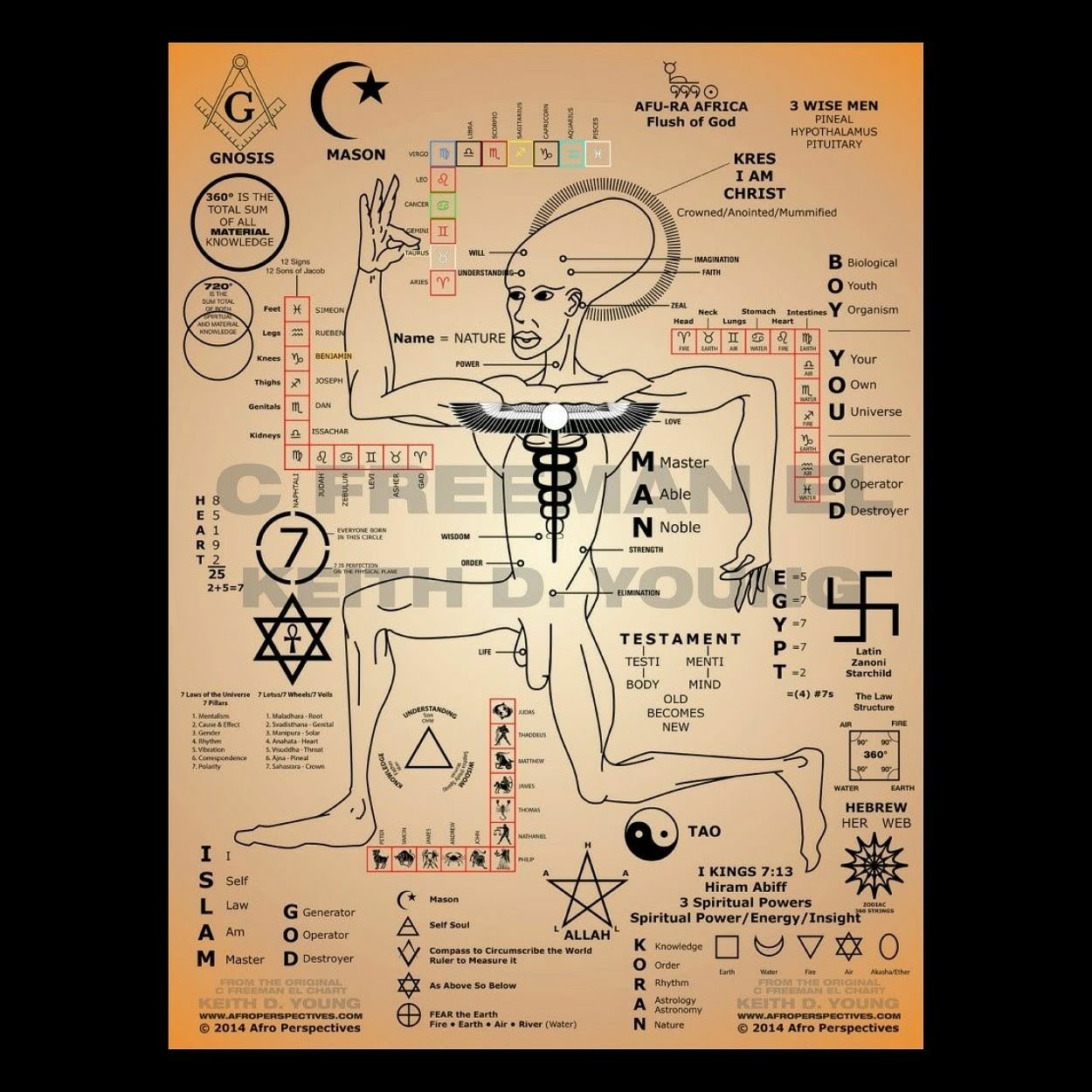
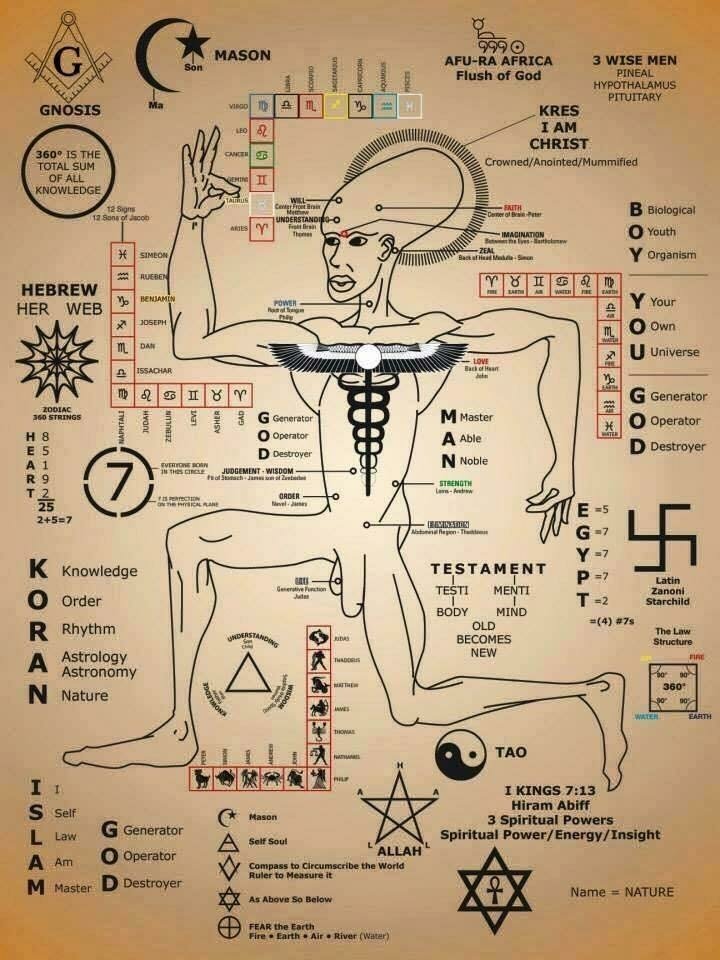
 1. Kristine Marcy (nee McConnell) “[Revised August 10, 2012: Kristine Marcy is a Matrix 5 principal and the 1979 founder and de-facto president of the Senior Executive Service (‘SES’); she allegedly borrowed British Bankers Association money at Libor Minus Sex Per Cent to modify ConAir – U.S. Justice Prisoner and Alien Transportation System – planes for missions such as the Norad Santa exercise of 1996; she allegedly flew ConAir prisoners on furlough to prepare a Libor $118,000 ransom note at a crime scene associated with the snuff film and torture killing of JonBenet Ramsey on Christmas Day 1996; she allegedly used the snuff film to extort national security concessions from JonBenet’s father and Lockheed Martin directors in 1996, including Lynne Cheney and Norman Mineta; she and co-recipients of the Gore Hammer awards, allegedly used Clipper chips and the Nortel-developed Joint Automated Booking Station (JABS) in the spoliation of evidence of the JonBenet murder in Boulder, Colorado in 1996, and the Gareth Williams murder some time in August 2010 in Pimlico, London, U.K.; she allegedly developed JABS for David Blood and Al Gore to authorize serial and/or mass murders of ‘Mindless Breathers – Useless Breeders’; she is allegedly rewarded with other JABS users for the management of evidence at Blood & Gore crime scenes with money laundered through the Department of Justice Assets Forfeiture Fund; she was the 1996 recipient of Vice President Gore’s Hammer Award for Reinventing Government Programs for her work in creating the Justice Prisoner and Alien Transportation System (JPATS – nick named ‘Con Air’); she allegedly organized the theft of PROMIS and its translation into a French version of JABS for La Sûreté du Québec and Francophonie 9/11; she and co-recipients of the Gore Hammer awards, allegedly used the Nortel JABS system in the spoliation of evidence of a home break-in at the former Glyndon property of her brother, Field McConnell; she allegedly conspired with FAA’s Collaborative Decision Makers who also won Gore Hammer awards, to overthrow the United States Government on 9/11; she allegedly sent bogus Con Air passenger manifests and flight schedules to the FAA’s air traffic control headquarters in Herndon, Va., to paralyze blue-team responses to electronic hijacking during the phony Gore Hammer war game on 9/11; she allegedly used Con Air to fly victims to cannibal oath ceremonies at a British Columbia pig farm where they would swear to uphold the principles espoused in Al Gore’s propaganda movie ‘An Inconvenient Truth’; she allegedly conspired with her former SBA loan syndicate client, Wells Fargo, to promote the Al Gore : Inconvenient Truth [Death by Breath?] propaganda on her brother’s birthday October 02, 2007 at the Wells Fargo Theatre in Denver, CO; she allegedly authorized DOJ Pride to set up a ConAir pedophile transport system to entrap and extort KPMG clients at SOS Children’s Villages in the State of Illinois and 130 countries around the world; she allegedly launched DOJ Pride in 1994 to infiltrate Uranian – third sex – entrapment experts into crime scene investigations to accuse the innocent and shelter the guilty; she allegedly used a Federal Bridge Certification Authority to give the U.K. Ministry of Defence an electronic warfare backdoor into the Air Force Special Operations Command and its SBA mentor-protégé programs for ‘Gore Hammer 9/11’; she allegedly converted a Pennsylvania mine to hold pedo-file images for use by her DOJ Pride colleagues to extort pedophile government employees and undermine the integrity of a Federal Bridge Certification Authority (‘FBCA’); she allegedly holds proxy keys to the FBCA which give Barack Obama distance from contract hits such as the Fast and Furious assassination of ATF agent Brian Terry; she is the former Senior Counsel for the Office of Detention and Removal Operations (DRO) of U.S. Immigration and Customs Enforcement (ICE); she allegedly issued time-lapse private keys to the SBA’s extorted 8(a) HUBZone voters to ensure Barack Hussein Obama was fraudulently elected POTUS 44 in November 2008; she allegedly procured time lapse keys for use by a matrix of Her Majesty’s Crown Uranian (see anagram for Manchurian) cells inside DOJ Pride to conceal Paperclip passport frauds exposing Obama as a citizen of the United Kingdom and Colonies (CUKC); she allegedly directs the extortion of man-in-the-middle officials in the U.S. Department of Justice, the Bar Associations of the District of Columbia and the U.S. Court of Military Appeals, and the U.S. Supreme Court; she appears to have used .tv snuff films to extort the Office of Personnel Management into concealing Obama’s ties to a Mau Mau oath-taking family in Kenya; she allegedly linked the U.S. Small Business Administration’s HUBZone Settlements to an E-Comm command center in British Columbia where 9-1-1 operators learn how to stage a murder during the production of a horror film production with unwitting (?) actors or extras; she allegedly formed a joint venture between Macdonald Dettwiler and Associates and the U.S. Justice Prisoner and Alien Transportation System (‘Con Air’) to use Sabre seat reservation technology to monitor the movements of pig farm oath takers; she allegedly used SBA 8(a) mentor-protégé companies to modify an EC135C Speckled Trout aircraft carrying General Henry Shelton and support a Uranian attempt to overthrow of the United States government on 9/11; she allegedly set up a revolving fund (# 15X4275) with bona vacantia – ownerless goods – in a joint venture with Star Chamber insiders, the Treasury Solicitor, Permira (Schroder Salomon Smith Barney in WTC#7) and organized crime groups to finance modifications of aircraft for the 9/11 attacks; she allegedly procured ‘Con Air’ Lear Jet aircraft for use by Bombardier’s homicidal EW pilot, Russell Williams to support the SES Speckled Trout chain of command and the decoy-and-drone maneuvers of 911; she allegedly used USIS files and Canadian Privy Council insider and NAPA vice president Lena Trudeau to create virtual ‘al-Qaeda’ operatives; she allegedly auctioned off SBA 8(a) CDOs just before the 9/11 attacks and assigned patented-device incendiary liquidation rights to D2 Banking and KPMG clients at Canary Wharf; she allegedly used images of Uranian pig-farm oath ceremonies to extort 9/11 cooperation from the likes of Donald Rumsfeld, Dick Cheney, Frank Carlucci, Lynn McNulty, Dr. David Finkleman, Gen. Ralph E. Eberhart, Rear Admiral Gordon Piche, Robert Mueller, Bruce McConnell and Generals Haig, Shelton and Shalikashvili; she is the de facto President and Chief Executive Officer of Washington D.C.-based NAPA (The National Academy of Public Administration); she allegedly infiltrated pig farm Greek Life oath takers into George Washington University, University of Chicago and Northwestern University and University of Hawaii (BA French) and Georgetown University ( MFS, master foreign service); she allegedly exfiltrated U.S. Marshals from Murrah Building OKC before initiating the bombs fraudulently attributed to a subsequently-executed decoy, Timothy McVeigh; we infer from spoliation through pay-per-view encryption that she re-assigned SBA liquidation rights in patent pool devices used on 9/11, including .tv to Crown Agents’ City & Guilds Livery Companies such as the Worshipful Company of Spectacle Makers]”
1. Kristine Marcy (nee McConnell) “[Revised August 10, 2012: Kristine Marcy is a Matrix 5 principal and the 1979 founder and de-facto president of the Senior Executive Service (‘SES’); she allegedly borrowed British Bankers Association money at Libor Minus Sex Per Cent to modify ConAir – U.S. Justice Prisoner and Alien Transportation System – planes for missions such as the Norad Santa exercise of 1996; she allegedly flew ConAir prisoners on furlough to prepare a Libor $118,000 ransom note at a crime scene associated with the snuff film and torture killing of JonBenet Ramsey on Christmas Day 1996; she allegedly used the snuff film to extort national security concessions from JonBenet’s father and Lockheed Martin directors in 1996, including Lynne Cheney and Norman Mineta; she and co-recipients of the Gore Hammer awards, allegedly used Clipper chips and the Nortel-developed Joint Automated Booking Station (JABS) in the spoliation of evidence of the JonBenet murder in Boulder, Colorado in 1996, and the Gareth Williams murder some time in August 2010 in Pimlico, London, U.K.; she allegedly developed JABS for David Blood and Al Gore to authorize serial and/or mass murders of ‘Mindless Breathers – Useless Breeders’; she is allegedly rewarded with other JABS users for the management of evidence at Blood & Gore crime scenes with money laundered through the Department of Justice Assets Forfeiture Fund; she was the 1996 recipient of Vice President Gore’s Hammer Award for Reinventing Government Programs for her work in creating the Justice Prisoner and Alien Transportation System (JPATS – nick named ‘Con Air’); she allegedly organized the theft of PROMIS and its translation into a French version of JABS for La Sûreté du Québec and Francophonie 9/11; she and co-recipients of the Gore Hammer awards, allegedly used the Nortel JABS system in the spoliation of evidence of a home break-in at the former Glyndon property of her brother, Field McConnell; she allegedly conspired with FAA’s Collaborative Decision Makers who also won Gore Hammer awards, to overthrow the United States Government on 9/11; she allegedly sent bogus Con Air passenger manifests and flight schedules to the FAA’s air traffic control headquarters in Herndon, Va., to paralyze blue-team responses to electronic hijacking during the phony Gore Hammer war game on 9/11; she allegedly used Con Air to fly victims to cannibal oath ceremonies at a British Columbia pig farm where they would swear to uphold the principles espoused in Al Gore’s propaganda movie ‘An Inconvenient Truth’; she allegedly conspired with her former SBA loan syndicate client, Wells Fargo, to promote the Al Gore : Inconvenient Truth [Death by Breath?] propaganda on her brother’s birthday October 02, 2007 at the Wells Fargo Theatre in Denver, CO; she allegedly authorized DOJ Pride to set up a ConAir pedophile transport system to entrap and extort KPMG clients at SOS Children’s Villages in the State of Illinois and 130 countries around the world; she allegedly launched DOJ Pride in 1994 to infiltrate Uranian – third sex – entrapment experts into crime scene investigations to accuse the innocent and shelter the guilty; she allegedly used a Federal Bridge Certification Authority to give the U.K. Ministry of Defence an electronic warfare backdoor into the Air Force Special Operations Command and its SBA mentor-protégé programs for ‘Gore Hammer 9/11’; she allegedly converted a Pennsylvania mine to hold pedo-file images for use by her DOJ Pride colleagues to extort pedophile government employees and undermine the integrity of a Federal Bridge Certification Authority (‘FBCA’); she allegedly holds proxy keys to the FBCA which give Barack Obama distance from contract hits such as the Fast and Furious assassination of ATF agent Brian Terry; she is the former Senior Counsel for the Office of Detention and Removal Operations (DRO) of U.S. Immigration and Customs Enforcement (ICE); she allegedly issued time-lapse private keys to the SBA’s extorted 8(a) HUBZone voters to ensure Barack Hussein Obama was fraudulently elected POTUS 44 in November 2008; she allegedly procured time lapse keys for use by a matrix of Her Majesty’s Crown Uranian (see anagram for Manchurian) cells inside DOJ Pride to conceal Paperclip passport frauds exposing Obama as a citizen of the United Kingdom and Colonies (CUKC); she allegedly directs the extortion of man-in-the-middle officials in the U.S. Department of Justice, the Bar Associations of the District of Columbia and the U.S. Court of Military Appeals, and the U.S. Supreme Court; she appears to have used .tv snuff films to extort the Office of Personnel Management into concealing Obama’s ties to a Mau Mau oath-taking family in Kenya; she allegedly linked the U.S. Small Business Administration’s HUBZone Settlements to an E-Comm command center in British Columbia where 9-1-1 operators learn how to stage a murder during the production of a horror film production with unwitting (?) actors or extras; she allegedly formed a joint venture between Macdonald Dettwiler and Associates and the U.S. Justice Prisoner and Alien Transportation System (‘Con Air’) to use Sabre seat reservation technology to monitor the movements of pig farm oath takers; she allegedly used SBA 8(a) mentor-protégé companies to modify an EC135C Speckled Trout aircraft carrying General Henry Shelton and support a Uranian attempt to overthrow of the United States government on 9/11; she allegedly set up a revolving fund (# 15X4275) with bona vacantia – ownerless goods – in a joint venture with Star Chamber insiders, the Treasury Solicitor, Permira (Schroder Salomon Smith Barney in WTC#7) and organized crime groups to finance modifications of aircraft for the 9/11 attacks; she allegedly procured ‘Con Air’ Lear Jet aircraft for use by Bombardier’s homicidal EW pilot, Russell Williams to support the SES Speckled Trout chain of command and the decoy-and-drone maneuvers of 911; she allegedly used USIS files and Canadian Privy Council insider and NAPA vice president Lena Trudeau to create virtual ‘al-Qaeda’ operatives; she allegedly auctioned off SBA 8(a) CDOs just before the 9/11 attacks and assigned patented-device incendiary liquidation rights to D2 Banking and KPMG clients at Canary Wharf; she allegedly used images of Uranian pig-farm oath ceremonies to extort 9/11 cooperation from the likes of Donald Rumsfeld, Dick Cheney, Frank Carlucci, Lynn McNulty, Dr. David Finkleman, Gen. Ralph E. Eberhart, Rear Admiral Gordon Piche, Robert Mueller, Bruce McConnell and Generals Haig, Shelton and Shalikashvili; she is the de facto President and Chief Executive Officer of Washington D.C.-based NAPA (The National Academy of Public Administration); she allegedly infiltrated pig farm Greek Life oath takers into George Washington University, University of Chicago and Northwestern University and University of Hawaii (BA French) and Georgetown University ( MFS, master foreign service); she allegedly exfiltrated U.S. Marshals from Murrah Building OKC before initiating the bombs fraudulently attributed to a subsequently-executed decoy, Timothy McVeigh; we infer from spoliation through pay-per-view encryption that she re-assigned SBA liquidation rights in patent pool devices used on 9/11, including .tv to Crown Agents’ City & Guilds Livery Companies such as the Worshipful Company of Spectacle Makers]”
 2. Samantha Cameron (nee ‘Snowy’ Sheffield)
2. Samantha Cameron (nee ‘Snowy’ Sheffield)
“[Revised July 23, 2012. Matrix 5 wife of the allegedly extorted man-in-the-middle Prime Minister of the United Kingdom, David Cameron; evidence she and her husband were ordered by trustees of the Thomson Reuters Foundation to develop a Carlton Communications snuff-film script – apparently financed by Libor panel banks – for the London Underground bombing of July 7th, 2005; evidence that on 9/11, she arranged multicast of ITV/Carlton idents followed by Naudet Brothers’ snuff-film images relayed via Schroder’s WTC Building #7; evidence her husband and fellow Bullingdon alumna synchronized ITV/Carlton idents with Schroders snuff film to associate ‘Pull it’ of WTC#7 with Twin Towers demolitions; evidence that Thomson Reuters-controlled Livery Companies sent her to New York on Monday September 10, 2001 to prepare a Matrix 5 man-in-the-middle attack on that city’s 9-1-1 operators; evidence that NYC 9-1-1 operators were deceived by 9/11 bait and switch calls; evidence she arranged root authority needed by the Worshipful Company of Spectacle Makers to film the demolition of WTC#7 and thereby confirm the destruction of evidence of Clipper-chip backdoors into the Mayor’s Office of Emergency Management; evidence she tried to establish an alibi for the production of VideoGuard snuff film images with the 9/11 Massive Attack group in New York with Hillary Clinton, Heather Mills and Sarah Ferguson; evidence she conspired with late Bullingdon Club alumnus and former U.K. Minister for War, Jack Profumo, in the use of Entrust public key infrastructure to conceal her Fag Mistress role during the pedophile man-in-the-middle propaganda attacks of 9/11; evidence she adapted a Matrix 5 pedophile-pimping strategy developed by her 17th century ancestor Nell Gwyn to procure VideoGuard-encrypted snuff-film images for the Treasury Solicitor to extort Livery Company support for 9/11 & 7/7 insurance frauds on Lloyd’s of London; evidence she used ‘Jane the Ripper’ oath takers, associated with various City and Guilds’ Livery Companies including The Musicians, to stage a Matrix-5 propaganda massive attack on New York on 9/11; evidence her mother, Viscountess Astor, provided ‘Fag Mistress’ services to Lord Boothby with the Kray Twins in the Astor-Club London of the ‘60s; evidence her ancestor Nell Gwynn provided Bona Vacantia contract-killing services through the Treasury Solicitor to the court of King Charles II; evidence she arranged for her husband to be employed by Michael Green as a ‘Haberdashers Ass’ from 1994 to 2001; evidence she ordered her husband to launder Carlton Communications’ pay-per-view revenues for the 9/11 Massive Attack through VideoGuard encryption networks which he allegedly integrated in the period 1990-1993 with the Bona Vacantia accounts of the Treasury Solicitor; evidence she ordered TSol – a London-based corporation sole – to settle bills presented by ownerless Livery Company special weapons and tactics teams for the murder of Todd Beamer et al. during phony war games on 911; evidence she ordered her husband to co-ordinate the production of Matrix 5 propaganda such as the docu-drama, ‘United 93’; evidence she plays a centuries-old role as ‘Mistress of the Revels’ or ‘agente provocatrice’ for lesbian or pedophile raves where witnesses are hired to entrap and extort future leaders; evidence she provided such services with Tricky’s Massive Attack group to Cameron’s Bullingdon Boys; evidence that her family entrapped David Cameron in a filmed pedophile rave at some time between his introduction to a tradition of pedophile rape and torture (beatings) at Eton College, through his work as a ‘Shipjumper’ with Jardine Fleming in Hong Kong, through his drunken property-smashing orgies at Oxford University’s oath taking Bullingdon Club; evidence that she ordered David Cameron and HSBC-Rothschild bankers to fund ‘ownerless SWAT teams’ to act for the Alliance of Small Island States in 1990 in ongoing man-in-the-middle propaganda attacks on the English Speaking Peoples; evidence that she or her mother ordered David Cameron to orchestrate the Black Wednesday sabotage of the U.K. Treasury [Solicitor] on 16 September 1992 when the pound sterling was withdrawn from the European Exchange Rate Mechanism; evidence of a seditious conspiracy between the Treasury Solicitor, the Cameron, Sheffield, Astor and Rothschild Families and George Soros – a WWII extortionist at a mere 14 years of age – to make a US$1 billion profit by short selling sterling; evidence she worked with Rebekah Brooks and Elisabeth Murdoch in the ’90s on the development of man-in-the-middle propaganda attacks on extorted leaders of industrialized societies to promote the ‘Catastrophic Anthropogenic Global Warming Causes Sea Rising and Flooding of Small Islands in the Age of Stupid’ myth and thereby justify a global tax on breath; Samantha Cameron graduated from City & Guilds’ Camberwell College of Arts; she is the former creative director of Smythson where she allegedly tracked and moved victims of pedophile and lesbian snuff-film raves with dual-use City & Guilds ‘bona vacantia’ products or services such as leather & skin passport covers (Leathersellers), Menzies Aviation weapons cargo and paramilitary-passenger handling systems (Guild of Air Pilots and Air Navigators and Information Technologists) and Newspaper Distribution (Stationers and Newspapermakers); she was allegedly alerted by her City & Guilds lesbian agents that Gareth Williams had enrolled at Central St Martin’s College of Art and Design in London and appeared to have hacked into Matrix 5 AOSIS network which she had helped to set up to launder CO2e money through her family office at D2 Banking Canada Square, Canary Wharf; evidence she procured a continuity of government authority to organize an illegal rave from Miriam Clegg, the Spanish wife of extorted man-in-the-middle Lord President of Council, Nick Clegg; evidence she used that authority to organize a City & Guilds lesbian rave at which Gareth Williams died; evidence she organized non-professional actors associated with Matrix 5 City & Guilds community into ownerless SWAT teams and left clues sufficient for Abel Danger to solve “Case of Haberdashers Ass and Beamer, Todd’ and ‘Case of the Folded Spook’]”
 3. Annabel Lucy Veronica Astor, Viscountess Astor (nee 1948 Jones) [CEO of OKA Direct, a home furnishings design company; former owner and designer of Annabel Jones jewellery business in London; mother of wife of British Prime Minister and Conservative Party leader David Cameron, Samantha Sheffield; she is daughter of Timothy Angus Jones and his wife Patricia David “Pandora” Clifford; her mother married secondly in 1961 to Michael Astor, habitué of the Astor Club alleged used by the Kray Twins to take control of the Metropolitan Police and House of Lords through a pedophile protection racket; Astor’s are considered to be the most powerful of the thirteen families or bloodline groups heading up the World Government plan; Astor’s allegedly portrayed as one of the 13 stars on the SES flag; individuals from the 13 families are mentioned in Dope Inc. [Crown Agents] as involved in some aspect of the drug trade: the Astor’s, Bundy’s, DuPont’s, Freeman’s, Kennedy’s, Li’s, Rockefellers, Rothschild’s, and Russell’s; other families also play key roles in the drug trade such as the Bronfman’s, Cabot’s, Shaw’s, Bacons, Perkins, Morgan, Forbes, Cisneros and Oppenheimer’s; Viscountess Astor paternal grandparents were Sir Roderick Jones, the Chairman of Reuters, and the novelist Enid Bagnold; Her mother Pandora Clifford was the daughter of the Hon. Sir Bede Edmund Hugh Clifford (son of William Hugh Clifford 10th Baron Clifford of Chudleigh, a descendant of King Charles II of England) by his wife Alice Devin Gundry]
3. Annabel Lucy Veronica Astor, Viscountess Astor (nee 1948 Jones) [CEO of OKA Direct, a home furnishings design company; former owner and designer of Annabel Jones jewellery business in London; mother of wife of British Prime Minister and Conservative Party leader David Cameron, Samantha Sheffield; she is daughter of Timothy Angus Jones and his wife Patricia David “Pandora” Clifford; her mother married secondly in 1961 to Michael Astor, habitué of the Astor Club alleged used by the Kray Twins to take control of the Metropolitan Police and House of Lords through a pedophile protection racket; Astor’s are considered to be the most powerful of the thirteen families or bloodline groups heading up the World Government plan; Astor’s allegedly portrayed as one of the 13 stars on the SES flag; individuals from the 13 families are mentioned in Dope Inc. [Crown Agents] as involved in some aspect of the drug trade: the Astor’s, Bundy’s, DuPont’s, Freeman’s, Kennedy’s, Li’s, Rockefellers, Rothschild’s, and Russell’s; other families also play key roles in the drug trade such as the Bronfman’s, Cabot’s, Shaw’s, Bacons, Perkins, Morgan, Forbes, Cisneros and Oppenheimer’s; Viscountess Astor paternal grandparents were Sir Roderick Jones, the Chairman of Reuters, and the novelist Enid Bagnold; Her mother Pandora Clifford was the daughter of the Hon. Sir Bede Edmund Hugh Clifford (son of William Hugh Clifford 10th Baron Clifford of Chudleigh, a descendant of King Charles II of England) by his wife Alice Devin Gundry]
 4. Hillary Clinton (nee Rodham) [Revised December 8, 2012 .. Allegedly uses SOS Children’s Villages to raise children for the pedophile sexual entrapment and extortion of prospective leaders such as Rhodes Scholar and former POTUS man-in-the-middle, Bill Clinton; she allegedly shuffled patent assignments used to build BBC Crimewatch timelines (‘Crimelines’) for murders dating back to at least 1984; she allegedly built Crimelines for the ‘Songbird’ profile executed by a patented guidance and control system in the bomb which demolished the Pentagon’s U.S. Navy Command Center on 9/11; she allegedly shuffled patent assignments for QRS-11 gyroscope sub-assemblies installed on a John ‘Songbird’ McCain weapons platform debris or evidence from which was removed on a Crimeline over the Pentagon Lawn on 9/11; she allegedly engaged in the sexual extortion of Joseph Giroir Jr. (former boss at Rose Law Firm), John Huang (former Commerce Department), John Riady (family partly owns Lippo Group in Indonesia where Barry Soetoro, now Barack Obama, was groomed as a pedophile entrapment expert) and various directors of Tyson Foods Inc., Wal-Mart Stores Inc. and BEI Technologies, Inc; as a patent lawyer, she allegedly assigned time lapse patents for BEI micromachined GyroChip sensors to support remote hijacking of systems related to Aircraft Flight Control, Helicopter Flight Control, Missile and Projectile Guidance, Unattended Guided Vehicle Navigation for Commercial and Military markets for everything from missiles to commercial light and heavy aircraft; as the Junior Senator from New York she allegedly used the Onion Router patent assignment with Sarah Ferguson to co-ordinate attack on Floor 101 of WTC#1 at their meeting the night before 9/11; she allegedly master minded the raid on Ron Brown’s office with T-Force and FBI’s Robert Hanssen to get continuity of government and encryption codes for D2 Banking and 9/11; Crown Agents’ USAID-SBA liquidations; ancestors associated with Oddfellows three-link binder of patents for contract killing; her 9/11 Modus Operandi was allegedly used by Crown Agents in 1836 arson at U.S. Patent Office to convert U.S. patents to exclusive use of City of London livery companies]”
4. Hillary Clinton (nee Rodham) [Revised December 8, 2012 .. Allegedly uses SOS Children’s Villages to raise children for the pedophile sexual entrapment and extortion of prospective leaders such as Rhodes Scholar and former POTUS man-in-the-middle, Bill Clinton; she allegedly shuffled patent assignments used to build BBC Crimewatch timelines (‘Crimelines’) for murders dating back to at least 1984; she allegedly built Crimelines for the ‘Songbird’ profile executed by a patented guidance and control system in the bomb which demolished the Pentagon’s U.S. Navy Command Center on 9/11; she allegedly shuffled patent assignments for QRS-11 gyroscope sub-assemblies installed on a John ‘Songbird’ McCain weapons platform debris or evidence from which was removed on a Crimeline over the Pentagon Lawn on 9/11; she allegedly engaged in the sexual extortion of Joseph Giroir Jr. (former boss at Rose Law Firm), John Huang (former Commerce Department), John Riady (family partly owns Lippo Group in Indonesia where Barry Soetoro, now Barack Obama, was groomed as a pedophile entrapment expert) and various directors of Tyson Foods Inc., Wal-Mart Stores Inc. and BEI Technologies, Inc; as a patent lawyer, she allegedly assigned time lapse patents for BEI micromachined GyroChip sensors to support remote hijacking of systems related to Aircraft Flight Control, Helicopter Flight Control, Missile and Projectile Guidance, Unattended Guided Vehicle Navigation for Commercial and Military markets for everything from missiles to commercial light and heavy aircraft; as the Junior Senator from New York she allegedly used the Onion Router patent assignment with Sarah Ferguson to co-ordinate attack on Floor 101 of WTC#1 at their meeting the night before 9/11; she allegedly master minded the raid on Ron Brown’s office with T-Force and FBI’s Robert Hanssen to get continuity of government and encryption codes for D2 Banking and 9/11; Crown Agents’ USAID-SBA liquidations; ancestors associated with Oddfellows three-link binder of patents for contract killing; her 9/11 Modus Operandi was allegedly used by Crown Agents in 1836 arson at U.S. Patent Office to convert U.S. patents to exclusive use of City of London livery companies]”
 6. Sarah, Duchess of York (nee Sarah Margaret Ferguson – Fergie) “[SARAH FERGUSON, LOST OFFICES IN WTC .. Howard Lutnick from Cantor Fitzgerald gave her office in New York on the 101st floor. Andrew flew to the US on 9/11 .. Fergie appointment .. for her Chances For Children charity with office in the World Trade Center KING: The famous doll story, too. They found the doll in the street. FERGUSON: Well, you know, the fact that she survived said to me that Little Red — how is it that my doll, for Chances For Children, she’s a symbol of the charity. KING: There’s the famous picture of the fireman finding her. Did you think that was an omen? FERGUSON: I did, Larry. You know, a lot of people would say, sure, you know, but I do, I really believe that it said to me, and I get Chances For Children up and running and get on an do more work and make sure you can give children a right to a healthy life” .. 1993, the Duchess founded Children in Crisis based in London with two current trustees: Grahame Harding and Paul Szkiler .. grown to help over 250,000 children annually in 10 countries around the world 2004 .. named official spokesperson of SOS Children’s Villages – USA 2006 .. established The Sarah Ferguson Foundation based in Toronto .. serve [exploit and extort] children and families in dire need .. China, Japan, Poland, Mexico, and cities across the United States .. filmed offering access to Prince Andrew for £500,000 .. heard to say “£500,000 when you can, to me, open doors” .. She is seen taking away a briefcase containing $40,000 (US) in cash” .. “The Prince Andrew, Duke of York (born 19 February 1960), second son third child of Queen Elizabeth II and Prince Philip … The Special Representative for International Trade and Investment for United Kingdom at trade fairs the world over .. took over from HRH The Duke of Kent in this role in 2001 .. 1979 Royal Naval College Flight.. signed on for 12 years from 11 May 1979 .. 1980 took the Royal Marines Green Beret commando course .. Invincible serve as a Sea King helicopter co-pilot .. anti-submarine warfare and anti-surface warfare, Exocet missile decoy, casualty evacuation, transport, and search and air rescue .. brief assignments to HMS Illustrious, RNAS Culdrose, and Joint Services School of Intelligence .. flight commander and pilot of the Lynx HAS3 on HMS Campbeltown from 1989 to 1991 .. flagship of NATO force in the North Atlantic from 1990 to 1991 former Senior Pilot of 815 Naval Air Squadron .. finish his naval career at the British Ministry of Defence until 2001, as officer of the Diplomatic Directorate of the Naval Staff .. On 19 February 2010 promoted to Rear Admiral .. Colonel-in-Chief of the Canadian Airborne Regiment (disbanded) [allegedly to create the core team for the 9/11 attack] .. Honorary Air Commodore of the Royal Air Force Lossiemouth; Personal Aide-de-Camp to Her Majesty The Queen; 1993-1999: Lieutenant-Commander, Captain, HMS Cottesmore; Senior Pilot, 815 NAS at RNAS Portland; Directorate of Naval Operations, British Ministry of Defence; 1999-2005: Commander, Diplomacy Section of the Naval Staff .. As the United Kingdom’s special trade representative, Prince Andrew frequently travels the world to promote British businesses .. revealed in the United States diplomatic cables leak [via Julian Assange Onion Router and pedophile network] Prince Andrew .. discussing bribery in Kyrgystan and the investigation into the Al-Yamamah arms deal and alleged kickbacks a senior Saudi royal had received in exchange for the multi-year, lucrative BAE Systems contract to provide equipment and training to Saudi security forces .. Prince Andrew also tours Canada to frequently undertake duties related to his military role there. Rick Peters, the former Commanding Officer of the Royal Highland Fusiliers of Canada stated: “[Prince Andrew]’s very well informed on Canadian military methods” … Freeman of the Worshipful Company of Shipwrights]”
6. Sarah, Duchess of York (nee Sarah Margaret Ferguson – Fergie) “[SARAH FERGUSON, LOST OFFICES IN WTC .. Howard Lutnick from Cantor Fitzgerald gave her office in New York on the 101st floor. Andrew flew to the US on 9/11 .. Fergie appointment .. for her Chances For Children charity with office in the World Trade Center KING: The famous doll story, too. They found the doll in the street. FERGUSON: Well, you know, the fact that she survived said to me that Little Red — how is it that my doll, for Chances For Children, she’s a symbol of the charity. KING: There’s the famous picture of the fireman finding her. Did you think that was an omen? FERGUSON: I did, Larry. You know, a lot of people would say, sure, you know, but I do, I really believe that it said to me, and I get Chances For Children up and running and get on an do more work and make sure you can give children a right to a healthy life” .. 1993, the Duchess founded Children in Crisis based in London with two current trustees: Grahame Harding and Paul Szkiler .. grown to help over 250,000 children annually in 10 countries around the world 2004 .. named official spokesperson of SOS Children’s Villages – USA 2006 .. established The Sarah Ferguson Foundation based in Toronto .. serve [exploit and extort] children and families in dire need .. China, Japan, Poland, Mexico, and cities across the United States .. filmed offering access to Prince Andrew for £500,000 .. heard to say “£500,000 when you can, to me, open doors” .. She is seen taking away a briefcase containing $40,000 (US) in cash” .. “The Prince Andrew, Duke of York (born 19 February 1960), second son third child of Queen Elizabeth II and Prince Philip … The Special Representative for International Trade and Investment for United Kingdom at trade fairs the world over .. took over from HRH The Duke of Kent in this role in 2001 .. 1979 Royal Naval College Flight.. signed on for 12 years from 11 May 1979 .. 1980 took the Royal Marines Green Beret commando course .. Invincible serve as a Sea King helicopter co-pilot .. anti-submarine warfare and anti-surface warfare, Exocet missile decoy, casualty evacuation, transport, and search and air rescue .. brief assignments to HMS Illustrious, RNAS Culdrose, and Joint Services School of Intelligence .. flight commander and pilot of the Lynx HAS3 on HMS Campbeltown from 1989 to 1991 .. flagship of NATO force in the North Atlantic from 1990 to 1991 former Senior Pilot of 815 Naval Air Squadron .. finish his naval career at the British Ministry of Defence until 2001, as officer of the Diplomatic Directorate of the Naval Staff .. On 19 February 2010 promoted to Rear Admiral .. Colonel-in-Chief of the Canadian Airborne Regiment (disbanded) [allegedly to create the core team for the 9/11 attack] .. Honorary Air Commodore of the Royal Air Force Lossiemouth; Personal Aide-de-Camp to Her Majesty The Queen; 1993-1999: Lieutenant-Commander, Captain, HMS Cottesmore; Senior Pilot, 815 NAS at RNAS Portland; Directorate of Naval Operations, British Ministry of Defence; 1999-2005: Commander, Diplomacy Section of the Naval Staff .. As the United Kingdom’s special trade representative, Prince Andrew frequently travels the world to promote British businesses .. revealed in the United States diplomatic cables leak [via Julian Assange Onion Router and pedophile network] Prince Andrew .. discussing bribery in Kyrgystan and the investigation into the Al-Yamamah arms deal and alleged kickbacks a senior Saudi royal had received in exchange for the multi-year, lucrative BAE Systems contract to provide equipment and training to Saudi security forces .. Prince Andrew also tours Canada to frequently undertake duties related to his military role there. Rick Peters, the former Commanding Officer of the Royal Highland Fusiliers of Canada stated: “[Prince Andrew]’s very well informed on Canadian military methods” … Freeman of the Worshipful Company of Shipwrights]”
7. Mary Harron “[Born in Ontario, Canada, in a film and theatre family; St Anne’s College, Oxford University; dated Tony Blair; moved to NYC into 1970s punk scene; first interview of Sex Pistols; 1980s drama critic for The Observer in London; executive producer The Weather Underground, directed TV episodes of Oz, Six Feet Under, Homicide: Life on the Street, The L Word and Big Love; currently developing film based on book Please Kill Me which details the 1970s New York punk scene; first movie, I Shot Andy Warhol 1996, story of Valerie Solanas who shot Andy Warhol and wrote SCUM Manifesto, a book detailing her ideas for ridding the world of men; second movie, American Psycho 2000 graphic descriptions of torture and murder by Patrick Bateman (Christian Bale), wealthy broker working at the fictional mergers and acquisitions firm Pierce & Pierce; The Notorious Bettie Page 2005, about 1950s pinup model a cult icon of sexuality who popularizes pornography]”
 8. Theresa Emerson (nee Yeuk-Si Tang) “[Husband is David Emerson, former Canadian foreign minister; “son-in-law of China”; he was director of MDA, the co-developer with SBA 8(a)’s Femme Comp Inc of the Onion Router for MCOINIII attacks on Allied naval ships and Final Approach to attack aircraft and co-developer with Countrywide of MindBox debt recovery software used through D2 Banking 9/11, Fannie Mae and BP-Deepwater Horizon bordereaux insurance frauds.]”
8. Theresa Emerson (nee Yeuk-Si Tang) “[Husband is David Emerson, former Canadian foreign minister; “son-in-law of China”; he was director of MDA, the co-developer with SBA 8(a)’s Femme Comp Inc of the Onion Router for MCOINIII attacks on Allied naval ships and Final Approach to attack aircraft and co-developer with Countrywide of MindBox debt recovery software used through D2 Banking 9/11, Fannie Mae and BP-Deepwater Horizon bordereaux insurance frauds.]”
 9. Linda Wright (nee Pickton) “[Revised December 11, 2011. Matrix 5 principal and sister of the allegedly extorted man-in-the-middle brothers, Dave and Willie (Robert) Pickton; she was allegedly given the unlawfully-delegated (ultra vires) Star Chamber authority of Canadian Privy Councilor, HRH Prince Philip, the Duke of Edinburgh, then President of City and Guilds, to hire guildsmen and women to film guests – including RCMP officials – at Piggy’s Palace Good Times Society cannibal feasts in B.C.; she allegedly used this authority to launch Matrix 5 propaganda attack on trustees of the RCMP’s pension and insurance funds; in 1996, she allegedly extorted her indebted brothers into running Piggy’s Palace (registered by the Canadian Privy Council in 1996) as a non-profit society intended to “organize, co-ordinate, manage and operate special events, functions, dances, shows and exhibitions on behalf of service organizations, sports organizations and other worthy groups”; she allegedly hired tradesmen through the Guild of Professional Home Services to hack domestic security systems through AT&T’s Clipper Chip and allow 9-1-1 operators to monitor and disrupt crime-scene investigations into B.C.’s pig-farm oath ceremonies (to 2001) and the murder of JonBenet Ramsey in 1996; she allegedly used her current Guild law-firm partner, Gordon H. Andreiuk – formerly employed at Ottawa’s Communications Security Establishment – to work with Crown Sister’s U.S. triple agent Robert Hanssen on the development of Clipper back doors into 9-1-1 emergency communications; she was the alleged fiduciary (or ‘off-book’ community organizer) of Matrix 5 “special events” at Piggy Palace–a converted building at the hog farm; she allegedly paid her distressed-debt brothers to stage drunken off-campus raves featuring “entertainment” by Downtown Eastside prostitutes orchestrated by lesbian prisoners on furlough from jails in Canada or America (Karla Homulka?); she allegedly knew that the women – many sacrificed in cannibal oath taking ceremonies – would not be missed, particularly because trustees of the Vancouver Police and RCMP pension funds had been tricked or extorted into investing in the mortgage on the development of the pig farm barn for the cannibal raves; soon after Piggy Palace opened in 1996, she and her brothers were sued by Port Coquitlam officials for violating city zoning ordinances; although she had the property zoned for agricultural use, she had “altered a large farm building on the land for the purpose of holding dances, concerts and other recreations” that sometimes drew as many as 1,800 persons; she allegedly arranged for her brother Willie to face 27 counts of first-degree murder related to women, mostly drug-addicted prostitutes, who disappeared from Vancouver’s seedy Downtown Eastside in the 1990s; she allegedly extorted VPD and RCMP officials to keep her out of court as a witness even though she must have known the women were disappearing on her property; as a Kerrisdale realtor, she was a best (?) friend of Carole Taylor (former Vancouver City councilor) and Nancy Campbell while their husbands Art Philips and Gordon Campbell were creating bcIMC – perhaps the world’s first pooled pig-farm pension plan to kick-back major crime-scene benefits to a city police force; following a New Year’s Eve party on December 31, 1998, she and her brothers were slapped with an injunction banning future parties, the court order noting that police were henceforth “authorized to arrest and remove any person” attending public events at the farm; her “society” finally lost its nonprofit status in January 2000, for failure to provide mandatory financial statements”; she told the RCMP that her pig farmer brother Willie was mentally “slow”; she contradicted herself by saying he wasn’t slow and he was good mechanically; she said he quit school at the age of 16 to focus on farming and didn’t do very well academically,”; she allegedly hired extortionists through Clipper Ripper Guilds, including Air Pilots and Air Navigators and Professional Home Services, to commission and bug Boeing headquarters before 9/11 and conceal a Matrix 5 man-in-the-middle propaganda attack on the United States government by City of Chicago and Vancouver Settlement Movement insiders; she allegedly conspired with the CAI Private Equity Group and insiders of the Ontario Teachers Pension Plan and the B.C. Investment Management Corporation (‘bcIMC’) to become controlling ‘pig-farm’ investors in Macdonald Dettwiler and its MindBox, BC OnLine and Instrument Approach Procedures services which would be needed to support Chicago Boeing’s 911 attack; after her parents died, she set up Dave Pickton to handle the business end of things and tell Willie Pickton when to go to bed at night; she placed her brother in a mobile home on the Dominion Avenue property to run a small-scale piggery and slaughter operation; she arranged for Willie Pickton to mortgage his share of the larger Dominion Avenue property to the lawyer Peter Ritchie for $375,000 in April 2002 in the form of a demand loan as Ritchie’s retainer; she arranged for Willie’s lawyers to launch a Robotham application in 2002, asking a judge to order him to receive a publicly funded defence; she had MDA MindBox and BC OnLine land title records ‘adjusted’ to show a long list of charges, mortgages and judgments registered against the two properties, often against Pickton’s share and most pre-dating the government’s mortgage; she and David Pickton, for example, registered a mortgage on the pig farm itself through a numbered company in 1998; she also registered a mortgage in 1998 on the smaller Burns Road property, this time keeping the ownership with her brothers to stay at arm’s length from the alleged Matrix 5 oath-taking ceremonies; she told the government that if it wanted to foreclose on the properties it would have to take her and her brother to court and apply to force a sale because of their joint ownership; she reminded government insiders of the rule of “first in time, first in line,” meaning that earlier creditors would be paid before the province; she extorted B.C. government insiders to use bcIMC securities to put a mortgage worth $10 million with no interest rate and no repayment schedule on the pig farm including the Dominion Avenue and Burns Road properties where both mortgages carry Willie’s signature; she used the money to cover the publicly funded defence of her brother Willie; she therefore ensured that funds were available to pay the lawyers to maintain Willie as a cutout for the lesbian and pedophile communities of Matrix 5; she had the mortgage registered on the suburban Port Coquitlam property and a nearby smaller parcel, on Feb. 28, 2003, a year after police raided the farm and arrested Willie; she arranged for the lender to be listed as the B.C. Crown, represented by the attorney general, where a lawyer in the ministry’s legal services branch, authorized the registration in a Feb. 27 2003 letter to the New Westminster land title office; she and her fellow Crown Agents’ Sisters, allegedly extorted control over New Westminster land title office through co-conspirator, Nancy Campbell, a member of bcIMC; she has allegedly used MDA’s 9-1-1 and MindBox automated [pig-farm] debt recovery system to entrap and extort top officials and consultants in Fannie Mae and Freddie Mac, including Newt Gingrich]”
9. Linda Wright (nee Pickton) “[Revised December 11, 2011. Matrix 5 principal and sister of the allegedly extorted man-in-the-middle brothers, Dave and Willie (Robert) Pickton; she was allegedly given the unlawfully-delegated (ultra vires) Star Chamber authority of Canadian Privy Councilor, HRH Prince Philip, the Duke of Edinburgh, then President of City and Guilds, to hire guildsmen and women to film guests – including RCMP officials – at Piggy’s Palace Good Times Society cannibal feasts in B.C.; she allegedly used this authority to launch Matrix 5 propaganda attack on trustees of the RCMP’s pension and insurance funds; in 1996, she allegedly extorted her indebted brothers into running Piggy’s Palace (registered by the Canadian Privy Council in 1996) as a non-profit society intended to “organize, co-ordinate, manage and operate special events, functions, dances, shows and exhibitions on behalf of service organizations, sports organizations and other worthy groups”; she allegedly hired tradesmen through the Guild of Professional Home Services to hack domestic security systems through AT&T’s Clipper Chip and allow 9-1-1 operators to monitor and disrupt crime-scene investigations into B.C.’s pig-farm oath ceremonies (to 2001) and the murder of JonBenet Ramsey in 1996; she allegedly used her current Guild law-firm partner, Gordon H. Andreiuk – formerly employed at Ottawa’s Communications Security Establishment – to work with Crown Sister’s U.S. triple agent Robert Hanssen on the development of Clipper back doors into 9-1-1 emergency communications; she was the alleged fiduciary (or ‘off-book’ community organizer) of Matrix 5 “special events” at Piggy Palace–a converted building at the hog farm; she allegedly paid her distressed-debt brothers to stage drunken off-campus raves featuring “entertainment” by Downtown Eastside prostitutes orchestrated by lesbian prisoners on furlough from jails in Canada or America (Karla Homulka?); she allegedly knew that the women – many sacrificed in cannibal oath taking ceremonies – would not be missed, particularly because trustees of the Vancouver Police and RCMP pension funds had been tricked or extorted into investing in the mortgage on the development of the pig farm barn for the cannibal raves; soon after Piggy Palace opened in 1996, she and her brothers were sued by Port Coquitlam officials for violating city zoning ordinances; although she had the property zoned for agricultural use, she had “altered a large farm building on the land for the purpose of holding dances, concerts and other recreations” that sometimes drew as many as 1,800 persons; she allegedly arranged for her brother Willie to face 27 counts of first-degree murder related to women, mostly drug-addicted prostitutes, who disappeared from Vancouver’s seedy Downtown Eastside in the 1990s; she allegedly extorted VPD and RCMP officials to keep her out of court as a witness even though she must have known the women were disappearing on her property; as a Kerrisdale realtor, she was a best (?) friend of Carole Taylor (former Vancouver City councilor) and Nancy Campbell while their husbands Art Philips and Gordon Campbell were creating bcIMC – perhaps the world’s first pooled pig-farm pension plan to kick-back major crime-scene benefits to a city police force; following a New Year’s Eve party on December 31, 1998, she and her brothers were slapped with an injunction banning future parties, the court order noting that police were henceforth “authorized to arrest and remove any person” attending public events at the farm; her “society” finally lost its nonprofit status in January 2000, for failure to provide mandatory financial statements”; she told the RCMP that her pig farmer brother Willie was mentally “slow”; she contradicted herself by saying he wasn’t slow and he was good mechanically; she said he quit school at the age of 16 to focus on farming and didn’t do very well academically,”; she allegedly hired extortionists through Clipper Ripper Guilds, including Air Pilots and Air Navigators and Professional Home Services, to commission and bug Boeing headquarters before 9/11 and conceal a Matrix 5 man-in-the-middle propaganda attack on the United States government by City of Chicago and Vancouver Settlement Movement insiders; she allegedly conspired with the CAI Private Equity Group and insiders of the Ontario Teachers Pension Plan and the B.C. Investment Management Corporation (‘bcIMC’) to become controlling ‘pig-farm’ investors in Macdonald Dettwiler and its MindBox, BC OnLine and Instrument Approach Procedures services which would be needed to support Chicago Boeing’s 911 attack; after her parents died, she set up Dave Pickton to handle the business end of things and tell Willie Pickton when to go to bed at night; she placed her brother in a mobile home on the Dominion Avenue property to run a small-scale piggery and slaughter operation; she arranged for Willie Pickton to mortgage his share of the larger Dominion Avenue property to the lawyer Peter Ritchie for $375,000 in April 2002 in the form of a demand loan as Ritchie’s retainer; she arranged for Willie’s lawyers to launch a Robotham application in 2002, asking a judge to order him to receive a publicly funded defence; she had MDA MindBox and BC OnLine land title records ‘adjusted’ to show a long list of charges, mortgages and judgments registered against the two properties, often against Pickton’s share and most pre-dating the government’s mortgage; she and David Pickton, for example, registered a mortgage on the pig farm itself through a numbered company in 1998; she also registered a mortgage in 1998 on the smaller Burns Road property, this time keeping the ownership with her brothers to stay at arm’s length from the alleged Matrix 5 oath-taking ceremonies; she told the government that if it wanted to foreclose on the properties it would have to take her and her brother to court and apply to force a sale because of their joint ownership; she reminded government insiders of the rule of “first in time, first in line,” meaning that earlier creditors would be paid before the province; she extorted B.C. government insiders to use bcIMC securities to put a mortgage worth $10 million with no interest rate and no repayment schedule on the pig farm including the Dominion Avenue and Burns Road properties where both mortgages carry Willie’s signature; she used the money to cover the publicly funded defence of her brother Willie; she therefore ensured that funds were available to pay the lawyers to maintain Willie as a cutout for the lesbian and pedophile communities of Matrix 5; she had the mortgage registered on the suburban Port Coquitlam property and a nearby smaller parcel, on Feb. 28, 2003, a year after police raided the farm and arrested Willie; she arranged for the lender to be listed as the B.C. Crown, represented by the attorney general, where a lawyer in the ministry’s legal services branch, authorized the registration in a Feb. 27 2003 letter to the New Westminster land title office; she and her fellow Crown Agents’ Sisters, allegedly extorted control over New Westminster land title office through co-conspirator, Nancy Campbell, a member of bcIMC; she has allegedly used MDA’s 9-1-1 and MindBox automated [pig-farm] debt recovery system to entrap and extort top officials and consultants in Fannie Mae and Freddie Mac, including Newt Gingrich]”
 10. Vicky Huhne or Pryce (nee 1952) “[Revised February 26, 2012. Former senior economist and consultant to the allegedly extorted man-in-the-middle clients of KPMG; she allegedly used ‘Worshipful Time Lapse Companies’, including Management Consultants and World Traders with her erstwhile KPMG colleague Michael Peat, to arrange a 30 hour time-lapse tax shelter through 9/11 to entrap and extort the custodians of the Queen’s Privy Purse and the bona vacantia accounts of the Duchy of Lancaster; she allegedly used the Federal Bridge Certification Authority to trigger Son of BOSS tax shelters for client insiders on 9/11; she is the former wife of allegedly extorted Chris Huhne, the recently resigned Secretary of State for Energy and Climate Change; she allegedly entered into a triangular Uranian relationship with her former husband’s lover, the bisexual Carina Trimingham; she was recently charged with her ex in perverting the course of justice; she is possibly an illegitimate Greek-born (1953) daughter of Prince Philip, the Grand Master of the Guild of Air Pilots and Air Navigators on 9/11, and an underage mother; she is the former Master of Worshipful Company of Management Consultants; she allegedly worked as an UK Government Economic Service insider to build a covert ‘chat room’ with the Treasury Solicitor for 9/11; she is an LSE Fabian who has allegedly been engineering predatory credit-default swaps in City & Guilds supply chains; she has allegedly enriched KGEN lesbians through the Family Offices of D2 Banking at Canary Wharf; she allegedly set up tScheme / DEADF007 authorities for Jardine Fleming and its ‘Auld Alliance’ families; she allegedly arranged bogus “bordereau” insurance cover for ‘liquidation’ of extorted borrowers in re Exxon Valdez, Military Bank, Williams & Glyn’s Bank, Royal Bank of Scotland, the Department for Trade and Industry and FTI; she is a reviewer for the Internet Watch Foundation and an alleged practitioner in the dual use of the Federal Bridge to monitor and entrap NetFlix viewers of child pornography]”
10. Vicky Huhne or Pryce (nee 1952) “[Revised February 26, 2012. Former senior economist and consultant to the allegedly extorted man-in-the-middle clients of KPMG; she allegedly used ‘Worshipful Time Lapse Companies’, including Management Consultants and World Traders with her erstwhile KPMG colleague Michael Peat, to arrange a 30 hour time-lapse tax shelter through 9/11 to entrap and extort the custodians of the Queen’s Privy Purse and the bona vacantia accounts of the Duchy of Lancaster; she allegedly used the Federal Bridge Certification Authority to trigger Son of BOSS tax shelters for client insiders on 9/11; she is the former wife of allegedly extorted Chris Huhne, the recently resigned Secretary of State for Energy and Climate Change; she allegedly entered into a triangular Uranian relationship with her former husband’s lover, the bisexual Carina Trimingham; she was recently charged with her ex in perverting the course of justice; she is possibly an illegitimate Greek-born (1953) daughter of Prince Philip, the Grand Master of the Guild of Air Pilots and Air Navigators on 9/11, and an underage mother; she is the former Master of Worshipful Company of Management Consultants; she allegedly worked as an UK Government Economic Service insider to build a covert ‘chat room’ with the Treasury Solicitor for 9/11; she is an LSE Fabian who has allegedly been engineering predatory credit-default swaps in City & Guilds supply chains; she has allegedly enriched KGEN lesbians through the Family Offices of D2 Banking at Canary Wharf; she allegedly set up tScheme / DEADF007 authorities for Jardine Fleming and its ‘Auld Alliance’ families; she allegedly arranged bogus “bordereau” insurance cover for ‘liquidation’ of extorted borrowers in re Exxon Valdez, Military Bank, Williams & Glyn’s Bank, Royal Bank of Scotland, the Department for Trade and Industry and FTI; she is a reviewer for the Internet Watch Foundation and an alleged practitioner in the dual use of the Federal Bridge to monitor and entrap NetFlix viewers of child pornography]”
11. Miriam Clegg “[Revised September 11, 2012. Matrix 5 principal and Femme Comp wife of the allegedly-extorted man-in-the-middle Nick Clegg, Minister for Constitutional and Political Reform in the U.K. coalition government of David Cameron; she allegedly used Alpine RapidEye surveillance and Onion Router technology to relay a license to kill Saad al-Hilli – a prospective whistleblower to the decoy-and-drone flying events of 9/11; she allegedly ordered al Hilli killed to stop him from revealing her client’s – British Bankers’ Nadhmi Auchi – escrow agreements with Julian Assange and Macdonald Dettwiler and Associates – Canada’s RapidEye contractor – to relay encrypted Onion Router license-to-kill messages for al-Qaeda hit teams on 9/11; she allegedly extorts her husband in his multiple roles, including a British Liberal Democrat politician, the Deputy Prime Minister of the United Kingdom and the Lord President of the Council; she allegedly ordered her husband to have code breaker Gareth Williams tortured and killed by suffocation in a hockey bag after his DEADF007 signature was found in the Stuxnet/Flame malware of logic process controllers Iran’s uranium enrichment program; she allegedly ordered her husband and his D2 Banking colleagues at Canada Square to try and snuff out traces of Flame malware used in the May 9 sabotage of Sukhoi Superjet; she was a Partner and head of international trade practice for multi-national law firm DLA Piper (2006-2011); she allegedly co-ordinated or extorted DLA Partners, Michael Lester, the former BAE Systems group legal director, and Frank Menaker, the former Lockheed Martin general counsel, into the payment of $400 million hush money to the DOJ Forfeiture Fund for the Saudi warplane bribes; she allegedly used her husband’s office to procure Bessemer’s VeriSign keys to the Federal Bridge and a Silent Witness role in the spoliation of evidence of Bessemer agents at the spy-in-the-bag (Gareth Williams) crime scene; she left Foreign Office in 2006 as an expert in the Middle East peace process and the racketeering arbitrage of the UN Oil-for-Food program under Robin Cook who was allegedly the victim of a patented hit on 6 August 2005; she allegedly extorted Cook as the Lord President of the Privy Council between 8 June 2001 to 18 March 2003; she’s allegedly cool at husband’s “no more than 30 “sexual encounters” which AD suspects include abuse of children in front of a video camera but outside the reach of Common Law; her husband studied the genocidal Deep Green child-killing movement at University of Minnesota in 1990; her husband interned in New York under the homosexual entrapment expert Christopher Hitchens; her husband moved to Brussels into G24 where he allegedly trained for the 911 attacks through the coordinated use of PKI and patented devices to control airline supply chains to former Soviet Union and Transport Corridor for Europe, the Caucasus and Asia; her husband took a second master’s degree at the College of Europe in Bruges where he and she appear to have been targeted for Dutroux-style pedophile entrapment; her husband’s great-great aunt Moura Budberg was mistress of Sir R. H. Bruce Lockhart, a double-agent for both the Soviet Union and British intelligence who served the two Odd Fellows – Winston Churchill and Franklin D. Roosevelt – who decided to nuke Hiroshima and Nagasaki; she is a former senior adviser in cabinet of EU external relations commissioner Chris Patten and the cabinet of Benita Ferrero-Waldner who was former Chef de protocole for Secretary General Boutros-Ghali at the UN in New York during the Rwanda Genocide; she was responsible for EU relations for the United States and the Middle East; she joined DLA Piper EU, Competition and Trade practice in London as a senior consultant; she is an expert in EU law and trade in the telecommunications and energy sectors; she is a former European Commissions’ leading trade negotiator at the WTO on telecommunication, energy, postal, construction and information services; she is former competition and regulatory lawyer for BT in Brussels; she has a masters degree from the College of Europe in Bruges (Belgium); she is a senior associate member of St Anthony’s College, Oxford; she was allegedly extorting Dr. Patrick Van Eecke as the man-in-the-middle of DLA Piper’s Internet law group who specializes in Mozilla open-source software, e-commerce, e-government, digital signatures and PKI, data protection, cyber-criminality and data protection; allegedly extorted staff at D2 Banking and PKI Sevices, Canary Wharf, and the U.S. Department of Commerce’s National Institute of Standards and Technology; allegedly authorized development of plaintext injection attacks against SSL to fool users into thinking session is secure and convert session to a true man-in-the-middle attack through Mozilla, VeriSign and Entrust; she allegedly created rogue CAs in Livery Company supply chains to allow Sisters to intercept traffic to a secure Web site and steal or plant sensitive information such as passwords and credit card data or phony clues; allegedly managed transition of security industry has from flawed MD5 to equally flawed SHA-1; she allegedly authorized Entrust to infiltrate the ePassports EAC Conformity & Interoperability Tests in Prague, Czech Republic and allow EU to move Matrix 5 pedophile assets and evade interception; allegedly allowed Entrust to build backdoor public key infrastructure (PKI) into the open-source community through Sun Microsystems, Inc. and the Mozilla Foundation; she allegedly authorized Silent Witnesses on the FBCA to ‘hijack’ AA Flight 77 in a Free Flight patented hit of pilot Captain “Chic” Burlingame (USNA 1971) and his crew and passengers; she and her fellow Crown Agents Sisters must now await reprisal by the late Captain Chic’s fellow Marines – Semper Fi]”
12. Baroness Sue Garden (nee Button) “[Wife of late 9/11 war-game maestro Tim Garden; he was Director of Royal Institute of International Affairs at Chatham House, London; from mid 1998, he undertook projects for the British Government [Crown Agents], the US Department of Defense and NATO; he was Visiting Professor at the Centre for Defence Studies at King’s College London from 2000, engaged in research projects on improving European defence capabilities, Defence Diplomacy, interoperability for NATO forces and counter-terrorism; he was military advisor on BBC television series Crisis Command and his publications include: Can Deterrence Last? and The Technology Trap; he gave [allegeldy false] evidence to Defence Committee on the new threats after 11 September 2001; she set up Financial Services Group of Livery Companies; House of Lords EU sub-committee for Home affairs report on cyber attack; Volunteer Citizens’ Advice Bureaux, welfare counsellor, military caseworker; 1988 – 2000, advisory until 2008 in City & Guilds vocational qualifications for Oddfellow Security Professionals and other illegally-bonded (?) users of Onion Router encryption; member World Traders’ Livery Company since 2000, Master 2008-09, spokesperson in Lords for Children, Schools and Families]”
13. Cherie Blair (nee Booth) “[Her MitM husband Tony Blair placed lesbian onion ring in GCHQ in 1997 to monitor pedophile trade; Oracle-LSE For You, Matrix Terrorists, Law of the European Union, European Convention on Human Rights]”
14. Jamie Gorelick “[Revised June 21, 2012: Presently, Gorelick represents BP in its sabotaged defense against Deepwater Horizon related lawsuits co-ordinated through Entrust PKI by Lena Trudeau; Gorelick is a former director of Schlumberger (the 40% owner of Transocean, the owner/operator of the Deepwater Horizon and alleged sponsor of a phony cat-bond arranged through D2 Banking, Canada Square, Canary Wharf); she allegedly authorized Matrix 5 saboteurs and SWAT teams, apparently commanded by the sexually-extorted former CIA Director John Deutch, to place customized dial-a-yield chemical cutter devices in various WTC box columns and Lloyd’s Register/Martec incendiary bombs on the Deepwater Horizon; she allegedly co-sponsored cat bond for total loss of DH rig a few weeks before the total loss; she allegedly cancelled DH Cement Job and pulled Schlumberger crew off the rig without recording the CBL and just prior to sabotage and the filing of the phony cat-bond claim on Lloyd’s Names; she was Deputy Attorney General of the United States during the Clinton administration; she banned the use of strong encryption; she called for adoption of key-escrow Entrust developed by Lena Trudeau for the Canadian Privy Council and John Deutch at CIA to support MitM attacks on America; she allowed Matrix 5 assassins and saboteurs to obtain Federal government access to encrypted communications; co-founder of DOJ Pride with Kristine Marcy who allegedly gave the lesbian, pedophile Janet Reno access to children moved by JPATS (`Con Air’) through the privatized prison system; she allegedly spoliated evidence of Matrix 5 1993 contract hits of Vince Foster and the black British pedophile oath takers at Waco; she allegedly stole a copy of Promis software with Kristine Marcy and translated it into French for integration into Entrust virtual war rooms and use in Daubert defense of terrorists and spies; she was appointed by the anthrax-extorted former Senate Democratic Leader Tom Daschle to serve as a commissioner on the National Commission on Terrorist Attacks Upon the United States; her association with major tragedies and high-profile American scandals of the past two decades has led some in the press to dub her the “Mistress of Disaster”; former Vice Chairman of Federal National Mortgage Association (Fannie Mae) from 1997 to 2003; she allegedly infiltrated Fannie with Matrix 5 8(a) lesbian saboteurs to drive credit-default frauds through MindBox and trigger automated cat-bond debt recovery from bankrupts during the so-called Global Financial Crisis; at Fannie, she served alongside former Clinton Administration official Franklin Raines who benefited from the 911 murder of Carlton Bartels with a subsequent interest in Bartels’ CO2e patent; she allegedly used Entrust to execute and conceal Fannie Mae $10 billion accounting frauds; in her op-ed letter in the Washington Post she states that: “At last week’s hearing, Attorney General John Ashcroft, facing criticism, asserted that ‘the single greatest structural cause for September 11 was the wall that segregated criminal investigators and intelligence agents’ and that I built that wall through a March 1995 memo.”; she used Entrust’s “Gorelick Wall” in a Tomoye virtual war room to block anti-terror investigators from accessing the computer of Zacarias Moussaoui, the 20th hijacker who was then in custody on an immigration violation enabled by Kristine Marcy; she used Entrust “Gorelick Wall” to block investigation into contributions to the Clinton-Gore Presidential re-election campaign from foreign sources involving the likes of John Huang and Charlie Trie where Entrust identities were hidden by straw donors.]”
15. Dame Stephanie “Steve” Shirley “[Revised January 17, 2012. First Master of the allegedly extorted men-in-the-middle of the Worshipful Company of Information Technologists (WCoIT); she funded the Company’s City base to the tune of £5 million; she was allegedly transported to Britain by Crown Agents’ operatives in Interpol as an unaccompanied Kindertransport child refugee; she was alleged hired as a spy to intercept post-war communications relating to Kindertransport and Interpol’s pedophile trade at the Royal Mail’s Post Office in Dollis Hill, London; she was allegedly financed by Crown Agents as the founder of the software company, Flexible Information (F.I.) Group (later Xansa, acquired by Steria) in 1962; she was told to employ only women and allegedly trained a significant number of lesbian pedophiles in the use of computer encryption to support man-in-the-middle attacks on government, business and industry leaders; she adopted the name “Steve”, apparently to show contempt for men and women in the Judeo-Christian, family-based heteropatriarchal societies of what Churchill called the ‘English Speaking Peoples’; she began infiltrating radical feminists into the City and Guilds after gaining the Freedom of the City of London in 1987; she allegedly used her £150m wealth to buy into – and take control of – charities during her retirement, including the Worshipful Company of Information Technologists (‘WCIT’) and the Oxford Internet Institute, part of the Oxford University through the Shirley Foundation; she is the alleged sponsor of DK Matai and D2 Banking’s digital data archives of pedophile snuff films; she allegedly procures D2 Banking content through the University Settlement Movement in London and Chicago, the Mormon’s Bountiful polygamist community in British Columbia and the SOS Children’s Villages headquarters in New York; she is the head of Shirley Trust; she is the radical feminist patron of the think-tank Tomorrow’s Company; she was born in 1933 during the last year of Lustmord and hyperinflation in Weimar Republic which we allege was orchestrated by Crown Agents and Interpol pedophiles using the Playfair cipher to conceal the movement of orphaned children through the Treasury Solicitor’s bona vacantia accounts.]”
16. Cressida Dick (nee Dick) “[Revised July 8, 2012. Cressida Dick is a Matrix 5 principal and an alleged early adopter of the Joint Automated Booking Station JABS for spoliation of evidence at crime scenes associated with murder-for-hire; she allegedly extorted insider of the Thomson Reuters’ Libor bank cartel to fund lesbian-controlled P3 construction contracts; she was an alleged lesbian principal in a Libor contract for the use of a “Gold Room” JABS to coordinate the 2005 London Underground bombing campaign; she allegedly used the Gold Room to coordinate the July 22nd murder of prospective Gold Room whistleblower, Jean Charles de Menezes, a Brazilian technician who had installed ADT CCTV cameras which generated images of the real July bombers; she allegedly used a JABS network set up by Wells Fargo at Canada Square in an attempted contract hit of the Russian banker, German Gorbuntsov; she is a sponsor of an alleged Common Purpose conspiracy, having attended a course in 1995/96 while serving in Thames Valley Police; she is allegedly engaged with fellow Common Purpose leaders in the lesbian and pedophile extortion of heterosexuals under the guise of promoting diversity; she allegedly first used JABS to conceal CCTV images associated with the murder of Princess Diana; she allegedly used a JABS installation at Wells Fargo’s Canada Square offices, Canary Wharf, to e-mail DNA, fingerprint and CCTV images from crime scenes associated with the murder of Gareth Williams (The Case of the Folded Spook); she has allegedly been using JABS for illegal surveillance of Ministers, VIP’s and Royal Family with Rebekah Wade; she was educated at the Dragon School (Oxford), Oxford High School, and Balliol College, Oxford; she allegedly worked with a large accountancy firm on early developments of PKI and what is now the U.S. Federal Bridge Certification Authority before joining the Metropolitan Police in 1983; she served as a Constable, Sergeant and Inspector in Central, South West and South East London; she was seconded to the staff of the Accelerated Promotion Course at Bramshill; she transferred to Thames Valley Police as Superintendent Operations; she subsequently spent three years as Area Commander in charge of policing the city of Oxford where she allegedly helped Bullingdon Club members organize illegal oath ceremonies; she attended the Strategic Command Course; she took a career break and studied full time for an M. Phil. in Criminology where she allegedly developed an alibi for the planning of the 9/11 attack with University Settlement Movement radicals, including John Profumo the late Bullingdon Club cleaner of Toynbee Hall toilet bowls; she returned to the Met as a Commander in June 2001 where she allegedly began working on the Wells Fargo pass-through certificates to finance the 9/11 contract hits; she used the position of Director of the Diversity Directorate to give her pan-London strategic responsibility for extorting silence or consent from heterosexual witnesses to organized crime (cf. two decades previously, Viscountess Astor and the Kray Twins); she joined the Specialist Crime Directorate in 2003; she was commander in charge of Serious & Organised Crime and Trident; she was promoted to Deputy Assistant Commissioner in February 2007 and moved to Specialist Operations in charge of protection and security in London; she was the Met’s representative on the “PROTECT” strand of the Government’s Counter Terrorism Strategy; she was promoted to be the first female Assistant Commissioner in the Met in July 2009; she was the Specialist Operations lead in the Met’s preparation for the Olympics and has allegedly planted bombs at various venues to extort government leaders into giving more concessions to the bankers at Canada Square; she took over Specialist Crime Directorate, which investigates the majority of serious crimes that occur in London; she implemented JABS control of evidence from crime scenes associated with murder, kidnap, shootings, rape, armed robbery, gun supply, child abuse, major fraud, e-crime and drugs networks; she used JABS to deliver and manipulate (spoliation) forensic evidence, intelligence and covert policing capability to the whole of the Met; she used JABS to take a command and control role for Met in snuff-film production on 9/11, the Tsunami, and the 2005 and 2007 terrorist attacks in London; she learned how to act as a hostage negotiator in 1989 and is chair of the National Negotiator Group; she is a long standing member of BAWP (British Association of Women in Policing and was appointed President in October 2010; she allegedly extorted Sir Paul Robert Stephenson, the former Metropolitan Police Commissioner, and John Yates, a former assistant commissioner, into resigning over the News International phone hacking affair which she appears to have orchestrated with Rebekah Wade using the Wells Fargo, Canada Square JABS network; she was appointed, assistant commissioner specialist operations in the wake of the resignations she had allegedly extorted and held the rank until 23 January 2012.]”
17. Eliza Manningham-Buller “[Oracle-MI5-CIA, Airwave; Money laundered with Net1, CRYPTOCard and Entrust technologies; Amec-Spie TETRA, Serco, Promis, K-Branch, IRA, Pan Am 103, NetJets 9/12, 7/7, RAF Brize Norton, Rendition, Waterboarding, Daughter Reginald Manningham-Buller of Bodkin’s Dope Inc. case]”
 18. Paule Gauthier “[Chair of SIRC 1996-2005 through the development of CANARIE and alleged use of Piggy’s Palace as Crown-registered charity for sexual extortion of top officials.]”
18. Paule Gauthier “[Chair of SIRC 1996-2005 through the development of CANARIE and alleged use of Piggy’s Palace as Crown-registered charity for sexual extortion of top officials.]”
19. France Desmarais (nee Chrétien) “[Daughter former Prime Minister of Canada Jean Chrétien. Husband Andre Desmarais; Special Assistant, Minister of Justice of Canada; Power Financial Corp; Groupe Bruxelles Lambert S.A.; Great-West Lifeco Inc. and Great-West Life Assurance Company; Pargesa Holding S.A.; Bertelsmann AG; Seagram; Director of Bombardier Inc.-Metronet, until 2004; Vivendi; Canada China Business Council; Chief Executive’s Council of International Advisers of The Government of the Hong Kong Special Administrative Region; CITIC International Advisory Council; Canadian Executive, United States Executive, Canadian Investment and Credit, United States Investment and Credit and Corporate Management Committees]”
20. Michelle Obama (nee Robinson) “[Revised July 17, 2012: Matrix 5 principal and wife of allegedly-extorted man-in-the-middle Barack Obama, a Citizen of the United Kingdom and Colonies and the 44th President of the United States; she allegedly built intellectual property in snuff films with former Sidley Austin lawyer, Bernardine ‘Torture Paradigm’ Dohrn; she allegedly uses archived snuff-film content to extort silence from witnesses to contract hits; she allegedly used Sidley Austin, to build an escrow service for Libor bankers to hide proceeds of crime and pay for contract hits; she allegedly procured DOJ Pride root authority for her lesbian associates in Illinois and SOS [Pedophile] Villages in Mexico to arrange Fast and Furious contract hits; she allegedly authorized Femme Comp’s use of Entrust PKI to buy alibis for Interpol or NATO Matrix 5 contract hits; she allegedly led Sidley Austin meetings in 1991 with the Senior Executive Service in Washington D.C. to sponsor use of 9-1-1 Clipper encryption chips to monitor Matrix 5 MitM propaganda attacks; she allegedly used 9-1-1 Clipper chips to monitor the 2009 contract hit of Wendy Ladner Beaudry at a Vancouver, B.C. crime scene; she allegedly controls terrorist alumni of the Jane Addams’ University Settlement Movement (founded Chicago 1891); she allegedly worked with terrorist mentor Bernardine Dohrn on the design of Greek Life oath taking involving late term abortion and pedophile traps; she allegedly extorted managers of the Illinois Municipal Retirement Fund (IMRF) and the Chicago Firemen’s Annuity & Benefit fund (CFABF) into buying rights in Permira VideoGuard pay-per-view snuff films on 9/11; in July 2008, she was awarded an honorary membership to the 100-year-old black sorority Alpha Kappa Alpha; she allegedly used Clipper encryption to synchronize the spoliation of evidence of a VideoGuard snuff-film studio in WTC#7 serving pay-per-view pedophile clients of SOS Children’s Villages in over 100 countries; she was allegedly recruited in 1984 at Princeton for a career as a Matrix 5 sextortionist by Henry Bienen, her Central Intelligence Agency [CIA] handler and the future president of Northwestern University; she allegedly helped Weather Underground terrorist boss Bernardine Dohrn build NU’s matrix of five community groups (‘Matrix 5’) using Entrust public key infrastructure provided by Bienen to authorize contract killing, sabotage and virtual deception; she was born 1964 in Chicago, Illinois to Marian and Fraser Robinson III, a Chicago city pump operator and a precinct captain for the mobbed-up Democratic Party machine; she graduated as a francophone from high school in 1981; Bienen guided her in sociology and African-American studies at Princeton where her 1985 thesis titled “Princeton-Educated Blacks and the Black Community” shows her focus on community organization of ethnic conflict; Bienen sent her to study law at Harvard to ‘rub raw the sores of discontent’; she sponsored crony hiring of professors who belonged to SBA 8(a)-listed minority groups; she launched libelous attacks on landlords using phony complaints from ‘virtual’ low-income tenants; she graduated from Harvard Law School in 1988; Bienen arranged for her to join Chicago law firm Sidley & Austin to develop expertise in intellectual property law and marketing; he assigned her to work in a ‘dual-use’ Sidley team to represent Union Carbide Corp. in its 1990 legal fight re a sale of a chemical business unit to Arco Chemical Co. and spoliation of evidence of Matrix 5 sabotage of Union Carbide’s Bhopal plant in India – 47 tons of water injected into a bath containing 42 tons of methyl isocyanate; he assigned her to work on a ‘dual-use’ Sidley team re IP associated with Barney the Purple Dinosaur AND the spoliation of evidence of role of Worshipful Company of Spectacle Makers in VideoGuard propaganda broadcast of BBC snuff films as virtual news over PBS; he assigned her to build a Women @ Sidley group of lesbians and work on federal bridge encryption protocols stolen from Ron Brown’s office; he assigned her to work with lesbians in Kristine Marcy’s DOJ Pride to build iCAIR for Matrix 5 sabotage, assassination and virtual deception; he assigned her to work on IP and patent protection for Unabomb devices trademarked with initials ‘FC’ standing for Femme Comp Inc; he transferred her in 1991 to work as mayoral assistant with Valerie Jarrett, then chief of staff to Chicago Mayor Richard Daley and a target for SOS sextortion who ultimately handed control of the City to terrorists in the University Settlement Movement; he transferred her in 1993 to head up a new Chicago office of Public Allies to create Matrix 5 training groups for young revolutionaries; he assigned her as associate dean of student services at University of Chicago to radicalize students; he assigned her as executive director of community affairs at University of Chicago Hospitals where she allegedly promoted use of VideoGuard encrypted images of late-term abortions to extort leaders of churches and community groups; he allegedly arranged for her pay increase from $122,000 to $316,000 a year and promotion to a vice president at the University of Chicago Hospitals; he allegedly showed her how to use Entrust PKI root authority to help her husband win a U.S. Senate seat in 2004; he allegedly helped heruse SOS Pedophile Villages to entrap and extort fellow members on the Chicago Council on Global Affairs; he allegedly showed her how to use SES Clipper and Entrust PKI to exploit 9-1-1 snuff-film images of the 911 attacks and the presence of University Settlement Movement killers at the Mumbai Massacre crime scenes.]”
 21. Bernardine Dohrn “[Revised September 3, 2012. Matrix 5 principal and mentor of an allegedly-extorted man-in-the-middle a.k.a. Barack Obama, a Citizen of the United Kingdom and Colonies and the 44th President of the United States; she was allegedly hired by Sidley Austin in 1984 to build a snuff-film escrow service for clients in the British Bankers’ Association to extort rapid recovery of Libor-rigged loans; she allegedly arranged for Charlie Manson’s “family” in the summer of ’69 to steal an NBC-TV truck loaded with equipment for snuff film production; her 3-fingered fork salute is now allegedly the covert sign needed to access the D2 Banking snuff-film archive at Canada Square, Canary Wharf; she allegedly developed Sidley Austin’s torture practice by grooming interns for a LGBT career in sexual entrapment and extortion of wealthy family-office clients; she allegedly closed Jane ‘The Ripper’ Addams’ Hull House and associated kindergarten service to cover an evidentiary trail dating back decades which leads to the late Jack Profumo – a Bullingdon Club pedophile and former UK minister for war; she allegedly helped Profumo develop the Toynbee Hall snuff film attack on the Munich Olympic Games in 1972; she is allegedly helped Bullingdon Club alumni and Toynbee Hall saboteurs to prepare the subsequently-thwarted bombing campaign for the London Olympic Games; she allegedly used the Sidley Austin family office service to arrange a contract hit of Wendy Ladner Beaudry and protect the Fortress investment in the Vancouver Winter Olympics; she is allegedly using Murdoch VideoGuard encryption to conceal pay-per-view snuff films sold through Sidley Austin to pedophile clients of SOS Children’s Villages in over 100 countries; she allegedly built Northwestern University’s link to the Federal Bridge Certification Authority for an attempted overthrow of the United States government on 9/11; she allegedly used Sidley Austin and DLA Piper’s family office services to procure time-lapse images of “Torture: Paradigms and Practice” at the Mumbai Massacre crime scenes.]”
21. Bernardine Dohrn “[Revised September 3, 2012. Matrix 5 principal and mentor of an allegedly-extorted man-in-the-middle a.k.a. Barack Obama, a Citizen of the United Kingdom and Colonies and the 44th President of the United States; she was allegedly hired by Sidley Austin in 1984 to build a snuff-film escrow service for clients in the British Bankers’ Association to extort rapid recovery of Libor-rigged loans; she allegedly arranged for Charlie Manson’s “family” in the summer of ’69 to steal an NBC-TV truck loaded with equipment for snuff film production; her 3-fingered fork salute is now allegedly the covert sign needed to access the D2 Banking snuff-film archive at Canada Square, Canary Wharf; she allegedly developed Sidley Austin’s torture practice by grooming interns for a LGBT career in sexual entrapment and extortion of wealthy family-office clients; she allegedly closed Jane ‘The Ripper’ Addams’ Hull House and associated kindergarten service to cover an evidentiary trail dating back decades which leads to the late Jack Profumo – a Bullingdon Club pedophile and former UK minister for war; she allegedly helped Profumo develop the Toynbee Hall snuff film attack on the Munich Olympic Games in 1972; she is allegedly helped Bullingdon Club alumni and Toynbee Hall saboteurs to prepare the subsequently-thwarted bombing campaign for the London Olympic Games; she allegedly used the Sidley Austin family office service to arrange a contract hit of Wendy Ladner Beaudry and protect the Fortress investment in the Vancouver Winter Olympics; she is allegedly using Murdoch VideoGuard encryption to conceal pay-per-view snuff films sold through Sidley Austin to pedophile clients of SOS Children’s Villages in over 100 countries; she allegedly built Northwestern University’s link to the Federal Bridge Certification Authority for an attempted overthrow of the United States government on 9/11; she allegedly used Sidley Austin and DLA Piper’s family office services to procure time-lapse images of “Torture: Paradigms and Practice” at the Mumbai Massacre crime scenes.]”
 22. Charlotte Bryan “[Revised March 18, 2012: Charlotte Bryan is a Matrix 5 principal of the Senior Executive Service (‘SES’) with Kristine Marcy, Field McConnell’s sister; she allegedly drove the Free Flight conspiracy at FAA headquarters and in Brussels with an erstwhile DLA Piper lawyer, Miriam Clegg; she allegedly entrapped and extorted U.S. and international airports and air carriers with time-lapse threats to illegally-modified aircraft, procured through leveraged leases structured by law firms such as DLA Piper and Sidley Austin; she allegedly received the Gore Hammer Award for her work with co-awardee, Kristine Marcy, on the integration of Con Air (JPATS) C4ISR into Crown Agents’ Sisters’ plans for Free Flight 9/11; she has over 36 years of federal experience including senior management responsibilities at the Federal Aviation Administration (FAA) and the Transportation Security Administration (TSA); she directed and managed U.S. airport security programs for over 429 airports for more than a decade; she was allegedly responsible for the leveraged lease and crony privatization of Stewart International Airport with National Express’s legal advisers DLA Piper; she sponsored the FAA’s Aviation Security Regulatory Program and forced commercial airports to adopt Free Flight; she used the shock-and-awe aftermath of Free Flight 9/11 to manage a phony FAA nationwide outreach program; she allegedly worked with Clinton Rubin associates to extort a share of the proceeds of 9/11 insurance claims from DLA Piper client Willis; she has allegedly compromised, terrified and silenced airline executives, aviation commissioners, state and local representatives, trade organizations, pilot and flight attendant unions, industry leaders, and airport and air carrier association members who would otherwise expose Free Flight time-lapse conspiracies to assassinate high value targets; she served as the TSA’s first Stakeholder Liaison and later as its first General Manager for Commercial Airports; she then served as TSA’s Assistant Administrator for Transportation Sector Network Management, responsible for 10 modal security offices including surface, rail and air transportation; she has significant experience working with U.S. and foreign air carriers on international aviation compliance issues; she served as the FAA’s Aviation Security Air Carrier Division Manager, where she worked with the major airlines and their security officials as the Principal Security Inspector in FAA offices in Europe, Africa and the Middle East; she graduated from the University of Maryland; she completed Northwestern University’s Kellogg School of Management Executive Program; she received a Masters in Public Administration from George Washington University.]”
22. Charlotte Bryan “[Revised March 18, 2012: Charlotte Bryan is a Matrix 5 principal of the Senior Executive Service (‘SES’) with Kristine Marcy, Field McConnell’s sister; she allegedly drove the Free Flight conspiracy at FAA headquarters and in Brussels with an erstwhile DLA Piper lawyer, Miriam Clegg; she allegedly entrapped and extorted U.S. and international airports and air carriers with time-lapse threats to illegally-modified aircraft, procured through leveraged leases structured by law firms such as DLA Piper and Sidley Austin; she allegedly received the Gore Hammer Award for her work with co-awardee, Kristine Marcy, on the integration of Con Air (JPATS) C4ISR into Crown Agents’ Sisters’ plans for Free Flight 9/11; she has over 36 years of federal experience including senior management responsibilities at the Federal Aviation Administration (FAA) and the Transportation Security Administration (TSA); she directed and managed U.S. airport security programs for over 429 airports for more than a decade; she was allegedly responsible for the leveraged lease and crony privatization of Stewart International Airport with National Express’s legal advisers DLA Piper; she sponsored the FAA’s Aviation Security Regulatory Program and forced commercial airports to adopt Free Flight; she used the shock-and-awe aftermath of Free Flight 9/11 to manage a phony FAA nationwide outreach program; she allegedly worked with Clinton Rubin associates to extort a share of the proceeds of 9/11 insurance claims from DLA Piper client Willis; she has allegedly compromised, terrified and silenced airline executives, aviation commissioners, state and local representatives, trade organizations, pilot and flight attendant unions, industry leaders, and airport and air carrier association members who would otherwise expose Free Flight time-lapse conspiracies to assassinate high value targets; she served as the TSA’s first Stakeholder Liaison and later as its first General Manager for Commercial Airports; she then served as TSA’s Assistant Administrator for Transportation Sector Network Management, responsible for 10 modal security offices including surface, rail and air transportation; she has significant experience working with U.S. and foreign air carriers on international aviation compliance issues; she served as the FAA’s Aviation Security Air Carrier Division Manager, where she worked with the major airlines and their security officials as the Principal Security Inspector in FAA offices in Europe, Africa and the Middle East; she graduated from the University of Maryland; she completed Northwestern University’s Kellogg School of Management Executive Program; she received a Masters in Public Administration from George Washington University.]”
 23. Lucy Adams “[Director/sponsor of LGBT quotas and ‘Diversity Dividend’ in Serco and BBC; Women in London’s Economy conference; Government must provide incentives and penalties for procurers to commit to diversity; Ascension Island transmission towers used to broadcast snuff films on 9/11 and 7/7.]”
23. Lucy Adams “[Director/sponsor of LGBT quotas and ‘Diversity Dividend’ in Serco and BBC; Women in London’s Economy conference; Government must provide incentives and penalties for procurers to commit to diversity; Ascension Island transmission towers used to broadcast snuff films on 9/11 and 7/7.]”
24. Alison Woodhams “[BBC World Service COO since 2004; BBC Group Financial Controller 2001-04; used AT & T Istel and Net1 to reward special weapons and tactics and propaganda teams deployed through BBC World Service Ascension Island in 43 languages]”
25. Nancy Pelosi (nee D’Alesandro) “[Speaker U.S United States House Representatives; Appropriations and ^ Committees. Son Paul Pelosi Jr.; Cisco Urban Development for Metronet tracking of victims; NASA Ames Research Center, AirPatrol Corporation; Bank of America Securities, Bank of America; Countrywide MindBox loan-recovery bordereaux for contract hits on 9/11 et al and JP Morgan]”
 26. Anna Chapman (nee Kushchenko) “[Revised June 16, 2012. Alleged expert in same-sex pedophile entrapment and extortion of clients in NetJets Europe and the Navigator hedge fund of Mayfair; allegedly used FondServisBank hackers in Moscow to hedge the Flame-induced (malware) crash of a Sukhoi SuperJet 100 on May 9 with long investments in Bombardier; allegedly directed the hit team which set up the murder of GCHQ code breaker Gareth Williams to stop him from exposing ongoing use of Flame to sabotage the Federal Bridge Certification Authority; allegedly used Flame to trigger pre-insured or hedged incidents such as the sinking of the Deepwater Horizon drilling rig and the crash of the Sukhoi SuperJet 100; she is an alleged former organizer of sex tourism at Barclays (Banker for Rebekah SOS Children’s Villages), NetJets and Navigator Asset Management in the City of London and for various mortgage bordereaux brokers in New York and KIT-Fortis in Russia and Belgium; she pleaded guilty to a charge of conspiracy to act as an agent of a foreign government; allegedly deported by Valerie Jarrett and Kristine Marcy to Russia July 8, 2010 in Russia-United States’ crony prisoner swap using Sabre booking on Con Air and covert time-share NetJets aircraft]”
26. Anna Chapman (nee Kushchenko) “[Revised June 16, 2012. Alleged expert in same-sex pedophile entrapment and extortion of clients in NetJets Europe and the Navigator hedge fund of Mayfair; allegedly used FondServisBank hackers in Moscow to hedge the Flame-induced (malware) crash of a Sukhoi SuperJet 100 on May 9 with long investments in Bombardier; allegedly directed the hit team which set up the murder of GCHQ code breaker Gareth Williams to stop him from exposing ongoing use of Flame to sabotage the Federal Bridge Certification Authority; allegedly used Flame to trigger pre-insured or hedged incidents such as the sinking of the Deepwater Horizon drilling rig and the crash of the Sukhoi SuperJet 100; she is an alleged former organizer of sex tourism at Barclays (Banker for Rebekah SOS Children’s Villages), NetJets and Navigator Asset Management in the City of London and for various mortgage bordereaux brokers in New York and KIT-Fortis in Russia and Belgium; she pleaded guilty to a charge of conspiracy to act as an agent of a foreign government; allegedly deported by Valerie Jarrett and Kristine Marcy to Russia July 8, 2010 in Russia-United States’ crony prisoner swap using Sabre booking on Con Air and covert time-share NetJets aircraft]”
27. Mila Mulroney (nee Milica Pivnički) “[On the Take, decade of crime, greed and corruption at 24 Sussex Drive; husband former Canadian Prime Minister Brian Mulroney; opening ceremony Canada Square; shoe fetishist; Balkans War. Alleged sextortion of husband and Yves Fortier, his former boss at Ogilvy Renault, Oxford University Rhodes Scholar (1960), Security Council (October 1989); London Court of International Arbitration Development through the 9/11]”
28. Julia Middleton (nee Morland) “[Common Purpose; French lycee; Economics degree LSE. CP supporters; BBC business editor Robert Peston, Metropolitan Police Assistant Deputy Commissioner Cressida Dick and many TOPOFFS; Uses Civilia FRS8 exemption to launder money for members in central and local government, Houses of Parliament, police, military, legal profession, BBC, NHS, church, 8,500 quangos, education, social services, civil service, and regional development agencies; Founder DEMOS with Obama and Rockefeller Brothers Fund; $64 trillion Carbon Disclosure Project, Media Standards Trust with Salz of Rothschild), Good Governance Network, Impetus Trust, and Alfanar]”

29. Anne Elizabeth Sikorski (nee Applebaum) “[Husband Polish Foreign Minister Radoslaw Sikorski, a Bullingdon ‘Blood and Steal’ Club member with David Cameron and Boris Johnson; supports Roman Polanski, snuff-film producer and pedophile rapist; Father is Harvey M. Applebaum, Covington and Burling partner with A-G Holder; she earned a B.A. (summa cum laude) at Yale University (1986), where she was elected to Phi Beta Kappa (Founded at The College of William and Mary on December 5, 1776, as the first collegiate Greek-letter fraternity); Marshall Scholar, London School of Economics (1987); St Antony’s College, Oxford; as a Marshall Scholar at the London School of Economics she earned a master’s degree in international relations (1987); Warsaw, Poland 1988 for The Economist; former editor at The Spectator; Former columnist for Daily Telegraph and Sunday Telegraph ergo spins for The Stationers.]”

30. Jana Clemmow (nee Bennett) “[Husband owner of Juniper peer to peer media production company and Oxford buddy of Blair. She linked to U.S. Discovery Communications; Director Vision BBC Fiction, Knowledge, Children’s and Entertainment, in-house TV and multi-media content through BBC Vision Productions; claimed £4,862 in expenses for taxi fares in 3 months to make confidential calls “in private.]”
 31. Laura Liswood (nee Liswood) “[Women and Power – Mechanisms to Advance Women’s Leadership; SCREAM pay-per-view; Council of Women World Leaders, Managing Director, Global Leadership and Diversity for Goldman Sachs; Abacus extorts men to allow a woman President of the United States; former GM Pacific Northwest and TWA; Boston Consulting Group; author ‘Serving Them Right’ and ‘ The Loudest Duck’; Seattle’s Women’s Commission; Seattle Woman; May’s List; In 2000, three-year term on Defense Advisory Committee on Women in the Services (DACOWITS); reserve police officer in Washington, D.C. Metropolitan Police Department after 9/11]”
31. Laura Liswood (nee Liswood) “[Women and Power – Mechanisms to Advance Women’s Leadership; SCREAM pay-per-view; Council of Women World Leaders, Managing Director, Global Leadership and Diversity for Goldman Sachs; Abacus extorts men to allow a woman President of the United States; former GM Pacific Northwest and TWA; Boston Consulting Group; author ‘Serving Them Right’ and ‘ The Loudest Duck’; Seattle’s Women’s Commission; Seattle Woman; May’s List; In 2000, three-year term on Defense Advisory Committee on Women in the Services (DACOWITS); reserve police officer in Washington, D.C. Metropolitan Police Department after 9/11]”
32. Brenda Stewart “[Senior V-P Net1; extorted (?) control of Dr. Belamant patents in COPAC (Chip Off-Line Pre-Authorized Card) and Net 1 universal electronic payment systems (or UEPS) for saboteurs, assassins and pedophiles based in unbanked or underdeveloped economies in South Africa, Europe, Asia, and Latin America]”
 33. Hanne Strong (nee Marstrand) “[Revised December 7, 2011. Matrix 5 principal and wife of the allegedly extorted man-in-the-middle Maurice Strong, a former pass officer position in the Identification Unit of the U.N. Security Section who apparently went on to use his CalTex job as a front in Kenya in 1953-1954 to develop Mau Mau oath ceremonies with Obama’s grandfather; she allegedly ran the lesbian-friendly Manitou Foundation near Baca Ranch and ordered her Canadian husband to sponsor a depopulationist program in China in the ‘80s where families would have second babies killed, bought or confiscated for use by SOS Children’s Villages Mothers to entrap government or military leaders; she and her husband and his family are directly or indirectly responsible for the abortion of 450 million fetuses and the genocidal killing of up to 80 million Chinese citizens.]”
33. Hanne Strong (nee Marstrand) “[Revised December 7, 2011. Matrix 5 principal and wife of the allegedly extorted man-in-the-middle Maurice Strong, a former pass officer position in the Identification Unit of the U.N. Security Section who apparently went on to use his CalTex job as a front in Kenya in 1953-1954 to develop Mau Mau oath ceremonies with Obama’s grandfather; she allegedly ran the lesbian-friendly Manitou Foundation near Baca Ranch and ordered her Canadian husband to sponsor a depopulationist program in China in the ‘80s where families would have second babies killed, bought or confiscated for use by SOS Children’s Villages Mothers to entrap government or military leaders; she and her husband and his family are directly or indirectly responsible for the abortion of 450 million fetuses and the genocidal killing of up to 80 million Chinese citizens.]”
 34. Winnie Mandela (nee Madikizela) “[Sexual extortionist, pedophile and kidnapper; ex wife Nelson Mandela; used young men and children as personal bodyguards in Mandela United Football Club; rubber tyres filled with petrol, ignited as “necklaces”; used Net 1 (?) to pay killers of 14-year-old Stompie Seipei; 1983 ANC car bomb of military headquarters in Pretoria; 1988 BBC World Service propaganda rock concert Wembley Stadium; Harry Belafonte, Whitney Houston, Roberta Flack, Stevie Wonder; smuggled message from Mandela read out, watched by 72,000 spectators, 200 million viewers in 60 countries.]”
34. Winnie Mandela (nee Madikizela) “[Sexual extortionist, pedophile and kidnapper; ex wife Nelson Mandela; used young men and children as personal bodyguards in Mandela United Football Club; rubber tyres filled with petrol, ignited as “necklaces”; used Net 1 (?) to pay killers of 14-year-old Stompie Seipei; 1983 ANC car bomb of military headquarters in Pretoria; 1988 BBC World Service propaganda rock concert Wembley Stadium; Harry Belafonte, Whitney Houston, Roberta Flack, Stevie Wonder; smuggled message from Mandela read out, watched by 72,000 spectators, 200 million viewers in 60 countries.]”

35. Franny Armstrong ( ?), “[Spanner Films, indie pop group The Band of Holy Joy, McLibel; Drowned Out; Narmada Dam Project; 10:10 No Pressure snuff film of exploding kids; ‘We ‘killed’ five people to make No Pressure – a mere blip compared to the 300,000 real people who now die each year from climate change’ The Age of Stupid in New Orleans; Passion Pictures client of Sohonet showed special effects of UNDEX after Hurricane Katrina.]”
36. Dame Julia Charity Cleverdon DCVO, CBE “[Late husband John Garnett, was director of the Industrial Society. She is Vice-President Business in the Community; was Chief Executive from April 1992 – March 2008; sponsors Age of Stupid linkage of environmental impact, diversity, workplace practice and ethical operations in the wider marketplace; Teach First; National Council for Educational Excellence; Prime Minister’s Talent and Enterprise Taskforce Advisory Group; ‘In Kind Direct’; Helena Kennedy Bursary Scheme; World Wildlife Fund; former Director Industrial Society’s Education and Inner City Division; industrial relations British Leyland]”
 37. Charlotte Beers “[Uncle Ben’s; J. Walter Thompson first female vice president in firm’s 106-year history; Tatham-Laird & Kudner CEO; Ogilvy & Mather Worldwide Chairman and CEO (1992-1997); handed over to Shelly Lazarus; J. Walter Thompson Worldwide chairman; 2 October 2001 sworn in as Under Secretary of State for Public Diplomacy and Public Affairs (at the US Department of State); assigned, amongst other things, to sell so-called War on Terrorism [WTF?] to [Stupid Men and Women in] public]”
37. Charlotte Beers “[Uncle Ben’s; J. Walter Thompson first female vice president in firm’s 106-year history; Tatham-Laird & Kudner CEO; Ogilvy & Mather Worldwide Chairman and CEO (1992-1997); handed over to Shelly Lazarus; J. Walter Thompson Worldwide chairman; 2 October 2001 sworn in as Under Secretary of State for Public Diplomacy and Public Affairs (at the US Department of State); assigned, amongst other things, to sell so-called War on Terrorism [WTF?] to [Stupid Men and Women in] public]”
38. Shelly Lazarus “[CEO and chairman of Ogilvy & Mather Worldwide; branding for American Express, Dove, Ford, Kraft, Kodak and IBM; ‘I’ve always believed that a brand is a relationship. And like all good relationships, it is built on trust .. we established Neo@Ogilvy, our digital media, direct response and search marketing unit two years ago. Mobile marketing also has a lot of potential .. mobile devices have become the “third screen,” and in some cases, the primary screen. We’ve formed digital innovation labs in five key markets around the world … Gaming [event arbitrage and bordereau insurance fraud?] is another hot area in which our digital labs are innovating’]”

39. Condoleezza Rice “[66th United States Secretary of State; President Bush’s National Security Advisor during first term; political science Stanford University Provost 1993 to 1999; chaired Millennium Challenge Corporation; Met CIA Director George Tenet July 10, 2001 in “emergency meeting” on impending al Qaeda attack; in PEOC with Lynne Cheney when Sisters disrupted 9/11 response by Dick Cheney and George Bush.]”

40. Heather Boyles “[Director Partner Relations Internet2; Non-US networking initiatives; US federal research networks; US-based advanced regional networks; Oversaw Internet2 International Relations program from its first partnership in 1997 with Canada’s CANARIE organization to over 45 partnerships today; Director of Policy and Special Projects at Federation of American Research Networks (FARNET); Master’s Degree International Affairs: International Economic Policy, American University in Washington, DC and a Bachelor’s Degree in International Studies and German from Indiana University of Pennsylvania.]”

41. Lily Safra (nee Watkins) “[Daughter Wolf White Watkins, British railway engineer; At age 17 husband 1, Mario Cohen, an Argentine hosiery magnate; 1965 husband 2 Alfredo Monteverde, leader in the Brazilian household appliance distribution business after establishing Ponto Frio brand; suicided by two shots from a revolver in his bed; all his assets to her and his former banker, Edmond Safra cut off the rest of the family; 1972 husband 3, Samuel Bendahan; 1976 husband 4, Edmond Safra, founder Republic National Bank of New York [and founder investor in Canary Wharf Group] who was killed in a fire that was determined to be arson security camera tapes from the night went missing; French examining judge claims trial “fixed in advance”; couple had no children together.]”
42. Joanne Ellis “[Group General Counsel at Sohonet Limited London, United Kingdom; Motion Pictures and Film; tScheme encryption for FC-KU crime scene management; former Commercial / Legal Director at BT Global Services; former Senior Legal Counsel at 02 (Airwave) Telefonica; former General Counsel, EMEA at Hitachi Data Systems.]”
 43. Jill Knesek “[Chief Security Officer BT Global Services; responsible for all security matters globally including Strategy, Security Policy & Compliance, Physical Security, Information Security, Travel Security, Regulatory Compliance and Investigations; former Director of Reactive Operations for the Cable & Wireless Managed Security Services group; in 1998 joined FBI as a Special Agent in Computer Crime Squad in the Los Angeles field office; Kevin Mitnick co-case agent; Mafiaboy FBI case agent with Royal Canadian Mounted Police (RCMP) in Montreal, Canada; case agent for first FBI undercover operation that infiltrated the hacker community to support many criminal investigations in the U.S. and abroad and National Infrastructure and Protection Center (NIPC) during Kosovo bombings; CISSP (Certified Information Systems Security Professional); CISM (Certified Information Security Manager). Office El Segundo, CA; routinely travels to London, New York and Washington DC area; monitored movement of Gareth Williams.]”
43. Jill Knesek “[Chief Security Officer BT Global Services; responsible for all security matters globally including Strategy, Security Policy & Compliance, Physical Security, Information Security, Travel Security, Regulatory Compliance and Investigations; former Director of Reactive Operations for the Cable & Wireless Managed Security Services group; in 1998 joined FBI as a Special Agent in Computer Crime Squad in the Los Angeles field office; Kevin Mitnick co-case agent; Mafiaboy FBI case agent with Royal Canadian Mounted Police (RCMP) in Montreal, Canada; case agent for first FBI undercover operation that infiltrated the hacker community to support many criminal investigations in the U.S. and abroad and National Infrastructure and Protection Center (NIPC) during Kosovo bombings; CISSP (Certified Information Systems Security Professional); CISM (Certified Information Security Manager). Office El Segundo, CA; routinely travels to London, New York and Washington DC area; monitored movement of Gareth Williams.]”

44. Darleen A. Druyun “[Former Principal Deputy Undersecretary of the Air Force for Acquisition and Boeing executive; Kennedy School of Government, Harvard University; United States Air Force tanker contract fraud; plan to speed up payments by Air Force to McDonnell Douglas; guilty of inflating price of contract to favor her future employer and passing information on competing Airbus A330 MRTT bid (from EADS); nine months in jail for corruption; transported by Marcy’s ConAir; Boeing paid D2 Banking 8(a) investors $615 million fine for involvement including sale of QRS11 for nuclear weapons guidance; guilty in award initial Small Diameter Bomb contract to Boeing. Donald Rumsfeld [former boss of Kristine Marcy in 1969] “what she did was acquire a great deal of authority and make a lot of decisions; very little adult supervision.”]
45. Kristin Franceschi “[Partner DLA Piper; January 1987 – Present (24+ years); Baltimore, Maryland Area; Industry Law Practice; issuers; credit enhancers, portfolio managers, and sponsors re public and private offerings of municipal and corporate debt securities; derivative transactions, including swap transactions integrated with municipal securities; incorporates hedging documentation into credit structure of the bond issue [bordereaux receivables; IRS arbitrage rules to permit transactions that might not otherwise be possible.]”

46. Angelina Jolie (née Angelina Jolie Voight) “[With SOS Children’s Villages named Nathalie Nozile as first Jolie Legal Fellow to protect Haiti’s vulnerable children; “Nathalie has .. unique perspective of growing up in an SOS Village .. returns to help strengthen Haitian judicial system .. a force…just wait and see”; father’s side, Czechoslovak and German descent; mother’s side French Canadian and Iroquois; eleven years old at Lee Strasberg Theatre Institute; at 14, dropped out of acting classes; dreamed of becoming a funeral director; black clothing, purple hair; moshed with live-in boyfriend; ‘punk kid with tattoos’; “I collected knives and always had certain things around. For some reason, ritual of having cut myself and feeling the pain, maybe feeling alive, feeling some kind of release, it was somehow therapeutic to me”; estranged from father Voight who claims she has “serious mental problems”; trophy abductions of children from SOS orphanages; baby tattoos with heavy bruising show geographical coordinates detailing where her four children, three adopted, were plucked; Maddox (Cambodia); Zahara (Ethiopia); Shiloh (Namibia biological) and Pax Thien (Vietnam); ongoing corruption and extortion of Office of the United Nations High Commissioner for Refugees (UNHCR; est. December 14, 1950).]”
47. Adrienne Clarkson (née Poy) “[1999 appointment as Canadian governor general by Elizabeth II Queen of Canada until succeeded by Michaëlle Jean in 2005; evidence she used David Johnston – then a CAI Special Investor in Macdonald Dettwiler Associates and now the current Canadian Governor General – to develop patent pool devices for pedophile oath taking, snuff-film production and crime scene spoliation at the Pickton pig farm and during the events of 911; evidence of illegal bordereau or CDS swap agreements in MDA with Johnston; 1941 refugee from Hong Kong; CBC producer and broadcaster for CBC; promoted Ontario culture in France and other European countries; anti-monarchist; paternal grandfather emigrated in the late 19th century to Chiltern, Australia and operated a general store called Willie Ah Poy Fruitier and Confectioner; Poy’s first son, William born in Victoria but later worked with his father for Canadian government in Hong Kong where he married Ethel Poy; two children: Neville born October 29, 1935, and Adrienne, born February 10, 1939; she hid in Hong Kong basements during Japanese invasion of the territory in 1941; Canadian government repatriated her father in 1942; post-graduate work in 1962, at the Sorbonne; 1963 married Stephen Clarkson a University of Toronto political science professor; three daughters: Kyra, born in 1969, and twins Blaise and Chloe, born in 1971; Chloe died of Sudden Infant Death Syndrome; Adrienne and Stephen divorced four years later, with Stephen being awarded full custody of the two surviving children, subsequently, Stephen’s second wife, Christina McCall adopted the two girls, who eventually became estranged from their [pedophile?] mother for several decades; president and publisher of McClelland and Stewart; highly unpopular with employees; Clarkson accompanied to Rideau Hall by her long time partner, John Ralston Saul, a former assistant to national oil company Petro-Canada’s first Chair, the allegedly genocidal pedophile Maurice F. Strong; Saul travelled with guerrilla armies in North Africa and South East Asia countries where he allegedly used SOS Pedophile Villages as pedophile entrapment centers to extort silence; following September 11, 2001, Clarkson praised Operation Yellow Ribbon saying “communities across the country selflessly opened their homes and hearts to stranded air travelers” but, as Canadian Governor General at the time of 911, she must have authorized the use of Canadian patent pools, including PKI/Onion Router encryption devices, by Macdonald Dettwiler and Associates and SBA 8(a) companies to stage a simulated man-in-the-middle attack on the United States government!; she ramped up spending of Crown ‘Agents’ funds at Rideau Hall by 200%; 2003 budget estimated at CAD $41 million; in 2003; she made a 19 day circumpolar “northern identity” tour with visits to Russia, Finland, and Iceland [SOS Pedophile Villages?] in company of Colonel Russell Williams, an allegedly-pedophile leader of an ‘al-Qaeda’ SWAT team on 911 and Maurice Strong, an allegedly-pedophile leader of an SOS Children’s Villages SWAT team on 911.]”
48. Lady de Rothschild (nee Lynn Forester) “[CEO of E.L. Rothschild, a holding company for the Economist business magazine which she uses to extort her third husband, Sir Evelyn Robert de Rothschild, into supporting man-in-the-middle propaganda attacks on the United States and its Sovereign Allies; daughter of John Kenneth Forester, president and owner of the General Aviation Company now Meridian in Teterboro, N.J.; Phi Beta Kappa Pomona College; Columbia Law School; Graduate Institute of International Studies in Geneva, Switzerland; 1980-1984 associate at Simpson Thacher & Bartlett law firm; 1984-1989 extorted telecommunications billionaire John Kluge to obtain position as Executive V-P for Development at Metromedia Inc; 60% interest in TPI Communications Inc, partly owned and financed by Motorola which she used to sabotage Motorola FDNY firefighter radios on 9/11; formed FirstMark Communications Inc in 1995; received first fixed wireless broadband licences for New York City, Los Angeles, San Francisco and Boston which she allegedly used in fraudulent client-server swaps on 9/11; founded Luxembourg-based wireless broadband venture FirstMark Communications Europe in 1998; acquired fixed broadband licences for Germany, Spain, France, Switzerland, Luxembourg and Finland and built a 20,000 km fiber network through-out continental Europe which she allegedly used in fraudulent client-server swaps and Sohonet post production of snuff film 9/11; allegedly extorted her fellow directors at FirstMark included Nathan Myhrvold of Microsoft, Washington D.C. power broker Vernon Jordan and Henry Kissinger; sold company in June 2000 in a $1 billion financing to raise funds for 911 client server swap; director Estée Lauder and The Economist Group; second husband, Andrew Stein a New York politician and son of a multi-millionaire businessman, Jerry Finklestein, was Manhattan Borough President at the time of their marriage; she allegedly forced Stein to arrange the sale of the WTC Twin Towers before 911 to camouflage the rigging of building with incendiary bombs by Amec (UK) and QinetiQ; introduced to Sir Evelyn de Rothschild by Henry Kissinger at the 1998 Bilderberg Group conference in Scotland; they married on November 30, 2000 in London and were invited by the 911 patent pool lawyer Hillary Clinton to spend their honeymoon at the White House; major fund raiser for Clinton’s 2008 Presidential bid; endorsed John McCain for President; attempting to set up a No Labels front organization to control a bicameral Congress with 8(a) Taser Chicks and sexual extortionists.]”
49. Ariane de Rothschild (nee Langner) “[born 1965 in San Salvador; wife of Baron Benjamin de Rothschild; vice-president of Edmond de Rothschild Holding SA since 1999 where she allegedly directs mortgage-based extortion of worldwide SOS `Mothers’ and pedophile alumni of SOS Children’s Villages – including Algeria and El Salvador – through the Bombardier Fund of Funds; MBA from Pace University in New York; former broker at Société Générale in New York; extorted U.S. insurance group AIG, to enter the French and European markets; member of the Board of Directors of the private banks Compagnie Financière Edmond de Rothschild in France and Banque privée Edmond de Rothschild in Switzerland; secret controller of Bombardier electronic warfare and GAPAN/ALPA patent pool contract hits with the Bombardier family, Bain Capital and the Caisse de dépôt et placement du Québec; Ariane de Rothschild Fellows Program, in partnership with Columbia Business School, University of Cambridge and ESSEC is hiding the bogus bio of Obama; she runs Edmond de Rothschild Group among other wine properties in Bordeaux (Château Clarke, Chateau Malmaison, Château des Laurets), Spain (Vega Sicilia), South Africa and Argentina; manages Le Domaine du Mont d’Arbois, a luxury hotel complex in Megève; she leads a syndicated debt investment vehicle for a racketeering influenced and corrupt organization (RICO) of the PENSION COMMITTEE OF THE UNIVERSITY OF MONTREAL PENSION PLAN [where unwitting faculty were invested in the massacre of a group of apolitical women engineers by `une gang de féministes’]; BANCO NOMINEES (I.O.M.) LIMITED, BANK OF BERMUDA (LUXEMBOURG), S.A., now called HSBC Security Services (Luxembourg) S.A., on behalf of Liberty Ermitage North American Absolute Fund Ltd., BANQUE PRIVEE EDMOND DE ROTHSCHILD EUROPE, CACEIS BANK LUXEMBOURG, as assignee of Banque Privee Edmond De Rothschild Europe/Isofin f/k/a Credit Agricole Investor Services Bank Luxembourg .. BASE FORCE, LTD., BOMBARDIER TRUST (CANADA), as agent of the administrators of the pension funds of Bombardier Inc. whose assets are collectively invested in the Bombardier Trust (Canada) (Foreign Assets) Fund [and the CC-144s which allegedly served as transports, patrol aircraft, and electronic ‘spoofers’ in Pan Am 103] THE BOMBARDIER TRUST (UK), THE BOMBARDIER TRUST (U.S.) MASTER TRUST .. COMMONFUND GLOBAL HEDGED PARTNERS, LLC, CONDOR ALTERNATIVE FUND, THE CORBETT FAMILY CHARITABLE FOUNDATION INC., THE CORONATION INTERNATIONAL ACTIVE FUND OF FUNDS, FORTIS [BNP Paribas Oil-for-Food and Anna Chapman sexual extortionist] GLOBAL CUSTODY MANAGEMENT AND TRUSTEE SERVICES (IRELAND) LIMITED as trustee for Coronation Universal Fund .. MELLON BANK, N.A., as Trustee for the Dominion Resources Inc. Master Trust .. FONDATION LUCIE ET ANDRE CHAGNON, ANDRE CHAGNON, SOJECCI II LTEE., FONDATION LILLA, GOULAM INVESTMENTS INC., GTALPHA, CHRISTA GUNTER, HERMES TRADING LTD., HSBC PRIVATE BANK (SUISSE) SA, formerly known as HSBC Republic (Suisse) SA .. KREDEITBANK LUXEMBOURG, NC SPECIAL OPPORTUNITIES FUND, KUWAIT AND MIDDLE EAST FINANCIAL INVESTMENT COMPANY, LA COMPAGNIE FINANCIERE EDMOND DE ROTHSCHILD BANQUE .. LGT BANK IN LIECHTENSTEIN AG .. MAESTRO TRADING, INC .. NATIONAL BANK OF CANADA .. PENSION COMMITEE OF REGIME DES RENTES DU MOUVEMENT DESJARDINS .. THE PENSION COMMITTEE OF THE PENSION PLAN FOR THE REGIME de RETRAITE DE LA CORPORATION DE L’ECOLE POLYTECHNIQUE [where unwitting faculty were invested in the massacre of a group of apolitical women engineers by `une gang de féministes’]; ROTHSCHILD GESTION, SATNAM INVESTMENTS LTD., SEVEN SEAS PORTFOLIO A LIMITED, SIGNET MULTI-MANAGER INC., UEB (UNITED EUROPEAN BANK) GENEVA (SWITZERLAND), SIL NOMINEES LIMITED, SPGP (Societe Privee de Gestion de Patrimoine) .. STARVEST FUNDS, LTD., THE TAURUS FUND, Successor-in-Interest to Turkos Seventeen Limited .. WESTWIND FOUNDATION HOLDINGS LTD., WYATT INCORPORATED EMPLOYEES PROFIT SHARING PLAN, 171212 CANADA, INC. .. COMMERZBANK GLOBAL ALTERNATIVE LIMITED, COMMERZBANK ALTERNATIVE STATEGIES-GLOBAL HEDGE; directed racketeering loans and extortion of inter alia .. BANC OF AMERICA SECURITIES LLC; CITCO FUND SERVICES (CURACAO), N.V., THE CITCO GROUP LIMITED, … PRICEWATERHO– USECOOPERS (NETHERLANDS ANTILLES), INTERNATIONAL FUND SERVICES (IRELAND) LIMITED]”
 50. Dr. Elaine C. Kamarck (nee ?) “[Alleged co-principal feminist for the pedophile extortion of U.S. Investigation Services clients – including Office of the Canadian Governor General and the Lord President of the Council – employees and Advisory Board members; a former Director of the National Performance Review; Lecturer in Public Policy at Harvard’s John F. Kennedy School of Government {where Maurice Strong’s dissertation on the use of Mau Mau pedophile oath taking is archived}; came to Kennedy School in 1997 after a career in politics and government; 1980s, she was one of the founders of the New Democrat movement that helped elect Bill Clinton [as an allegedly extorted man-in-the-middle] president; served in the White House from 1993 to 1997, where she created and managed the Clinton Administration’s National Performance Review, also known as Reinventing Government [which allegedly required the assassination of Vincent Foster and Ron Brown to procure the continuity of government protocols for Crown Agents Sisters’ 911]; has served as Director of Visions of Governance for the Twenty-First Century and as Faculty Advisor to the Innovations in American Government Awards Program at Kennedy School; in 2000, she took a leave of absence to work as Senior Policy Advisor to the presidential campaign of Al Gore {to prepare the media campaign for the Global Warming scam; she researches the role of the Internet in virtual deception, net-centric warfare; 21st-century government, in political campaigns, homeland defense, intelligence reorganization, and governmental reform and innovation; Ph.D. in political science from the University of California, Berkeley; author of a wannabee ‘Rules for Radicals’ entitled “The End of Government As We Know It: Policy Implementation in the 21st Century”; author of “Primary Politics: How Presidential Candidates Have Shaped {Corrupted} the Modern Nominating System”; she has worked as a senior fellow at the Progressive Policy Institute and has written regular columns for Newsday and the Los Angeles Times.]”
50. Dr. Elaine C. Kamarck (nee ?) “[Alleged co-principal feminist for the pedophile extortion of U.S. Investigation Services clients – including Office of the Canadian Governor General and the Lord President of the Council – employees and Advisory Board members; a former Director of the National Performance Review; Lecturer in Public Policy at Harvard’s John F. Kennedy School of Government {where Maurice Strong’s dissertation on the use of Mau Mau pedophile oath taking is archived}; came to Kennedy School in 1997 after a career in politics and government; 1980s, she was one of the founders of the New Democrat movement that helped elect Bill Clinton [as an allegedly extorted man-in-the-middle] president; served in the White House from 1993 to 1997, where she created and managed the Clinton Administration’s National Performance Review, also known as Reinventing Government [which allegedly required the assassination of Vincent Foster and Ron Brown to procure the continuity of government protocols for Crown Agents Sisters’ 911]; has served as Director of Visions of Governance for the Twenty-First Century and as Faculty Advisor to the Innovations in American Government Awards Program at Kennedy School; in 2000, she took a leave of absence to work as Senior Policy Advisor to the presidential campaign of Al Gore {to prepare the media campaign for the Global Warming scam; she researches the role of the Internet in virtual deception, net-centric warfare; 21st-century government, in political campaigns, homeland defense, intelligence reorganization, and governmental reform and innovation; Ph.D. in political science from the University of California, Berkeley; author of a wannabee ‘Rules for Radicals’ entitled “The End of Government As We Know It: Policy Implementation in the 21st Century”; author of “Primary Politics: How Presidential Candidates Have Shaped {Corrupted} the Modern Nominating System”; she has worked as a senior fellow at the Progressive Policy Institute and has written regular columns for Newsday and the Los Angeles Times.]”
 51. Joanne O. Isham (nee?) “[Alleged co-principal feminist for the pedophile extortion of U.S. Investigation Services clients – including Office of the Canadian Governor General and the Lord President of the Council – employees and Advisory Board members; as President of Isham Associates, she works with clients in the Defense and Intelligence sectors to develop strategies, identify high-value opportunities, address critical challenges and transform their business; former Senior Vice President for L-1 Identity Solutions—a market leader in identity management [and alleged passport frauds]; from 2007-2008, she was Chief Operating Officer of High Performance Technologies, Inc. (HPTi) specializing in computational science; enterprise technology and planning; systems architecture and engineering; secure software development and knowledge discovery and visualization [of 911 snuff films]; former Vice President / Deputy General Manager of Network Systems at BAE Systems, responsible for new mission focus within the Intelligence Community, Department of Defense and Department of Homeland Security; prior to BAE Systems, she served as a member of the Senior Intelligence Service and a career officer at the Central Intelligence Agency (CIA); after the failure of an attempted coup d’etat on September 11, 2001 until her retirement in 2006, she served as Deputy Director of the National Geospatial-Intelligence Agency; prior to that she served as Deputy Director for Science and Technology at the CIA, serving as the principal overseer of the CIA’s scientific and technical program with QinetiQ in clandestine technical activities and Agency research and development; former CIA’s Associate Deputy Director for Science and Technology and held other senior management positions in the CIA and other Intelligence Community organizations; former Director of Congressional Affairs for the Director of Central Intelligence (DCI); former Deputy Director of the Resource management Office of the Community Management Staff (CMS) and as CMS’ Director of Program Analysis; oversaw budget and resource issues spanning the entire Intelligence Community and integration with Bombardier Fund of Funds for 911 attack; spent a number of years on assignment to the National Reconnaissance Office as Director of Legislative Affairs; recipient of National Intelligence Distinguished Service Medal, Department of Defense Distinguished Civilian Service Award, National Intelligence Medal of Achievement, CIA Distinguished Intelligence Medal, NGA Distinguished Intelligence Medal and DIA Director’s Awards; member of Senior Advisory Group for Director of National Intelligence; Board of Trustees for Analytic Services Inc.; Board of Directors for Applied Analysis, Incorporated; INSA and Open Geospatial Consortium; graduate of the University of Notre Dame].”
51. Joanne O. Isham (nee?) “[Alleged co-principal feminist for the pedophile extortion of U.S. Investigation Services clients – including Office of the Canadian Governor General and the Lord President of the Council – employees and Advisory Board members; as President of Isham Associates, she works with clients in the Defense and Intelligence sectors to develop strategies, identify high-value opportunities, address critical challenges and transform their business; former Senior Vice President for L-1 Identity Solutions—a market leader in identity management [and alleged passport frauds]; from 2007-2008, she was Chief Operating Officer of High Performance Technologies, Inc. (HPTi) specializing in computational science; enterprise technology and planning; systems architecture and engineering; secure software development and knowledge discovery and visualization [of 911 snuff films]; former Vice President / Deputy General Manager of Network Systems at BAE Systems, responsible for new mission focus within the Intelligence Community, Department of Defense and Department of Homeland Security; prior to BAE Systems, she served as a member of the Senior Intelligence Service and a career officer at the Central Intelligence Agency (CIA); after the failure of an attempted coup d’etat on September 11, 2001 until her retirement in 2006, she served as Deputy Director of the National Geospatial-Intelligence Agency; prior to that she served as Deputy Director for Science and Technology at the CIA, serving as the principal overseer of the CIA’s scientific and technical program with QinetiQ in clandestine technical activities and Agency research and development; former CIA’s Associate Deputy Director for Science and Technology and held other senior management positions in the CIA and other Intelligence Community organizations; former Director of Congressional Affairs for the Director of Central Intelligence (DCI); former Deputy Director of the Resource management Office of the Community Management Staff (CMS) and as CMS’ Director of Program Analysis; oversaw budget and resource issues spanning the entire Intelligence Community and integration with Bombardier Fund of Funds for 911 attack; spent a number of years on assignment to the National Reconnaissance Office as Director of Legislative Affairs; recipient of National Intelligence Distinguished Service Medal, Department of Defense Distinguished Civilian Service Award, National Intelligence Medal of Achievement, CIA Distinguished Intelligence Medal, NGA Distinguished Intelligence Medal and DIA Director’s Awards; member of Senior Advisory Group for Director of National Intelligence; Board of Trustees for Analytic Services Inc.; Board of Directors for Applied Analysis, Incorporated; INSA and Open Geospatial Consortium; graduate of the University of Notre Dame].”
 52. Jalynn Hamilton Bennett (nee?) “[Revised December 28, 2011. Matrix 5 principal and partner (?) of up to 50 extorted man-in-the-middle special investors in the CAI Private Equity Group; as a Wellesley College alumna, Bennett allegedly used Mitt Romney to hedge and Julian Assange to hack pension-fund investors in mortgages ‘secured’ by snuff films, allegedly generated at the Pickton pig farm in British Columbia for sponsors of the Dyke Ball – a “creative black-tie” event hosted by Spectrum, Wellesley’s LGBT organization; she allegedly directed CAI to finance the development of Entrust public key infrastructure by Nortel and MDA to execute MitM attacks on the VPD and RCMP crime scene investigators at the pig farm; CAI special investor with Canadian Governor General David Johnston and a former Bombardier director Pierre Lortie; she allegedly organized a Master Trust with Equity of Canada for the development of a GAPAN/ALPA Bombardier electronic warfare capability to execute patented contract hits; uses Bombardier EW to co-ordinate the spoliation of crime scenes with her CAI colleagues and fellow CA Sisters; she allegedly helped to hire and promote pedophile extortionist and Bombardier EW pilot Russell Williams to execute WTC 1993, Vince Foster, Murrah Building, JonBenet Ramsey, USS Cole, 911, Space Shuttle Columbia, Air France Flight 447, and Beverley Eckert; she is President at Jalynn H. Bennett and Associates Ltd.; Director of Teck Resources Limited since 1989; prior to that she was associated for nearly 25 years with The Manufacturers Life Insurance Company; former Director at CIBC World Markets and Canadian Imperial Bank of Commerce since 1994; former director Teck Cominco Ltd., since April 27, 2005; former Independent Director engaged in pump-and-dump and patent-asset stripping of Nortel Networks Corp.; and Nortel Networks Limited since June 29, 2005; Director at Sears Canada Inc., CIBC, Hospital for Sick Kids Foundation, and the Cadillac Fairview Corporation Limited; member of Advisory Board at Investeco Capital Corp; former Director at CanWest Media Inc., from 2000 to January 2005 and Canwest Global Communications Corp. from January 1998 to March 2005 where she liquidated the former media assets of the Hollinger Chain to abort any investigation by Conrad Black’s journalists into her role with David Johnston, Pierre Lortie and Russell Williams in the 911 attacks on America; she was a former director Bombardier Inc., from 2002 to December 2004 where she allegedly conspired with co-Sister Ariane de Rothschild in integrating Equity of Canada with the co-investors in the Bombardier Master Trust; former director of Bank of Canada; past Chairman at the Ontario Teachers’ Pension Plan Board Investment Committee where she acquired control of Macdonald Dettwiler and Associates development of Entrust/PKI and Onion Router encryption for a 911 MitM attack; former Commissioner of the Ontario Securities Commission; former Member of the Canadian Institute of Chartered Accountants 2000 Toronto Stock Exchange Committee on Corporate Governance; Member of the National Advisory Board, Canada’s Outstanding CEO of the Year, and a Member of the Trinity College Endowment Campaign Cabinet; Director of SickKids Foundation]”
52. Jalynn Hamilton Bennett (nee?) “[Revised December 28, 2011. Matrix 5 principal and partner (?) of up to 50 extorted man-in-the-middle special investors in the CAI Private Equity Group; as a Wellesley College alumna, Bennett allegedly used Mitt Romney to hedge and Julian Assange to hack pension-fund investors in mortgages ‘secured’ by snuff films, allegedly generated at the Pickton pig farm in British Columbia for sponsors of the Dyke Ball – a “creative black-tie” event hosted by Spectrum, Wellesley’s LGBT organization; she allegedly directed CAI to finance the development of Entrust public key infrastructure by Nortel and MDA to execute MitM attacks on the VPD and RCMP crime scene investigators at the pig farm; CAI special investor with Canadian Governor General David Johnston and a former Bombardier director Pierre Lortie; she allegedly organized a Master Trust with Equity of Canada for the development of a GAPAN/ALPA Bombardier electronic warfare capability to execute patented contract hits; uses Bombardier EW to co-ordinate the spoliation of crime scenes with her CAI colleagues and fellow CA Sisters; she allegedly helped to hire and promote pedophile extortionist and Bombardier EW pilot Russell Williams to execute WTC 1993, Vince Foster, Murrah Building, JonBenet Ramsey, USS Cole, 911, Space Shuttle Columbia, Air France Flight 447, and Beverley Eckert; she is President at Jalynn H. Bennett and Associates Ltd.; Director of Teck Resources Limited since 1989; prior to that she was associated for nearly 25 years with The Manufacturers Life Insurance Company; former Director at CIBC World Markets and Canadian Imperial Bank of Commerce since 1994; former director Teck Cominco Ltd., since April 27, 2005; former Independent Director engaged in pump-and-dump and patent-asset stripping of Nortel Networks Corp.; and Nortel Networks Limited since June 29, 2005; Director at Sears Canada Inc., CIBC, Hospital for Sick Kids Foundation, and the Cadillac Fairview Corporation Limited; member of Advisory Board at Investeco Capital Corp; former Director at CanWest Media Inc., from 2000 to January 2005 and Canwest Global Communications Corp. from January 1998 to March 2005 where she liquidated the former media assets of the Hollinger Chain to abort any investigation by Conrad Black’s journalists into her role with David Johnston, Pierre Lortie and Russell Williams in the 911 attacks on America; she was a former director Bombardier Inc., from 2002 to December 2004 where she allegedly conspired with co-Sister Ariane de Rothschild in integrating Equity of Canada with the co-investors in the Bombardier Master Trust; former director of Bank of Canada; past Chairman at the Ontario Teachers’ Pension Plan Board Investment Committee where she acquired control of Macdonald Dettwiler and Associates development of Entrust/PKI and Onion Router encryption for a 911 MitM attack; former Commissioner of the Ontario Securities Commission; former Member of the Canadian Institute of Chartered Accountants 2000 Toronto Stock Exchange Committee on Corporate Governance; Member of the National Advisory Board, Canada’s Outstanding CEO of the Year, and a Member of the Trinity College Endowment Campaign Cabinet; Director of SickKids Foundation]”
 53. Ronalee “Rona” Ambrose (nee?) “[Privy Councilor; incumbent Minister of Public Works and Government Services, and Receiver General for Canada responsible for depositing and withdrawing funds from the Consolidated Revenue Fund of Canada; former Vice-Chair of the Treasury Board Cabinet committee where she allegedly integrated Equity of Canada with racketeering co-investors in the Bombardier Master Trust; former Minister of State for Status of Women Canada where she allegedly helped to promote Crown Agents Sisters and pedophiles into controlling positions; former Minister of Western Economic Diversification whose parliamentary secretary, Russ Hiebert, allegedly helped to procure the Bombardier EW technology at Abbotsford Airport for a surprise attack by Bombardier’s pedophile pilot and killer, Russell Williams, on Vancouver 2010 Winter Olympics; Minister of Intergovernmental Affairs and President of the Queen’s Privy Council for Canada where it appears that hundreds of members have been set up for sexual extortion by the pedophile EW pilot and killer Russell Williams; former communication consultant and public policy consultant for the Alberta government; grew up both in Brazil and in Parkland County, Alberta; fluent English, Spanish, Portuguese, and intermediate French; “working women want to make their own choices, we don’t need old white guys telling us what to do”; appointed Environment Minister in Prime Minister Stephen Harper’s government where she refused to kill or proved herself incapable of killing Maurice Strong’s Kyoto scam.]”
53. Ronalee “Rona” Ambrose (nee?) “[Privy Councilor; incumbent Minister of Public Works and Government Services, and Receiver General for Canada responsible for depositing and withdrawing funds from the Consolidated Revenue Fund of Canada; former Vice-Chair of the Treasury Board Cabinet committee where she allegedly integrated Equity of Canada with racketeering co-investors in the Bombardier Master Trust; former Minister of State for Status of Women Canada where she allegedly helped to promote Crown Agents Sisters and pedophiles into controlling positions; former Minister of Western Economic Diversification whose parliamentary secretary, Russ Hiebert, allegedly helped to procure the Bombardier EW technology at Abbotsford Airport for a surprise attack by Bombardier’s pedophile pilot and killer, Russell Williams, on Vancouver 2010 Winter Olympics; Minister of Intergovernmental Affairs and President of the Queen’s Privy Council for Canada where it appears that hundreds of members have been set up for sexual extortion by the pedophile EW pilot and killer Russell Williams; former communication consultant and public policy consultant for the Alberta government; grew up both in Brazil and in Parkland County, Alberta; fluent English, Spanish, Portuguese, and intermediate French; “working women want to make their own choices, we don’t need old white guys telling us what to do”; appointed Environment Minister in Prime Minister Stephen Harper’s government where she refused to kill or proved herself incapable of killing Maurice Strong’s Kyoto scam.]”
54. Samantha Power (nee SOS Children’s Villages breeding station?) “[Special Assistant to President Barack Obama; after 2008 presidential election joined Department of State transition team and is therefore a co-sponsor with Kristine Marcy and Lena Trudeau of the NAPA Matrix 5 RICO community; runs Office of Multilateral Affairs and Human Rights as Senior Director of Multilateral Affairs on the Staff of the National Security Council; Founding Executive Director and the Anna Lindh Professor of Practice of Global Leadership and Public Policy of the Carr Center for Human Rights Policy at Harvard University’s Kennedy School of Government; expert observer and alleged inciter of genocides, including Yugoslav Wars; former senior adviser to Obama until March 2008 when she resigned from his presidential campaign under controversy; alleged user of Privy Council Entrust PKI to bypass BHO and authorize illegal attack on Libya; born in Dublin, Ireland, and emigrated to the United States in 1979; graduated from Yale University; from 1993 to 1996 worked as a journalist, covering the Yugoslav wars; returned to the United States and attended Harvard Law School graduating in 1999; author of A Problem from Hell: America and the Age of Genocide; analyst of failure of governments and international community to collectively identify, recognize and then respond effectively to genocides ranging from the Armenian Genocide to the Rwandan Genocide; spent 2005–06 working in the office of U.S. Senator Barack Obama as a foreign policy fellow, where she directed Obama’s play in the Darfur conflict; in a March 6 interview with The Scotsman, she said: “We fucked up in Ohio. In Ohio, they are obsessed and Hillary is going to town on it, because she knows Ohio’s the only place they can win”. “She is a monster, too — that is off the record — she is stooping to anything… if you are poor and she is telling you some story about how Obama is going to take your job away, maybe it will be more effective”; Power argues re genocides that “you don’t get any extra credit for doing the right thing”. “It’s up to us” to change that calculus, she said. “My prescription,” she said, “would be that the level of American and international engagement would ratchet up commensurate with the abuse on the ground’; she has allegedly uses the Marcy-Trudeau Matrix 5 communities to stimulate abuse and justify intervention.]”
55. Valerie Bowman Jarrett (nee Bowman) “[Revised May 22, 2012. Matrix 5 advisor to the allegedly extorted man-in-the-middle POTUS 44, Barack Obama; she is the Chair of Obama’s allegedly extorted White House Council on Women and Girls; she allegedly authorized same sex-and lesbian insider traders to hack Nasdaq auction software and trigger short-selling fraud on Facebook shareholders including its heterosexual founder Mark Zuckerberg; she is a former member of the allegedly extorted board of the Chicago Stock Exchange (2000–2007, as Chairman, 2004–2007); senior advisor to Obama for Public Engagement and Intergovernmental Affairs; former co-chairperson of Obama-Biden Transition Project and therefore co-sponsor with same-sex extortionists, Kristine Marcy and Lena Trudeau of the NAPA Matrix 5 RICO community; she was born in Shiraz, Iran to American parents James E. Bowman and Barbara Taylor Bowman; when she was five, the family moved to London for one year, returning to Chicago in 1963; her mother, Barbara T. Bowman was one of four child advocates that created the Erikson Institute to provide advanced knowledge in child development for teachers and other professionals working with young children; as a child she spoke Persian and French; married in 1983 to Dr. William Robert Jarrett, son of Chicago Sun-Times reporter Vernon Jarrett a pedophile (?) buddy of Obama’s pedophile mentor, Frank Marshall Davis; former Deputy Corporation Counsel for Finance and Development working for Chicago Mayor Harold Washington; former Deputy Chief of Staff for Mayor Richard Daley during which time (1991) she hired Michelle Robinson, then engaged to Barack Obama, away from Sidley Austin where they were mentored by terrorist boss Bernardine Dohrn; former Commissioner of Department of Planning and Development from 1992 through 1995; former Chair of the Chicago Transit Board from 1995 to 2005; former Chairman of the Board of Trustees of the University of Chicago Medical Center; former Vice Chairman of the Board of Trustees of the University of Chicago; one of three Senior Advisors to President Obama; holds retitled position of Assistant to the President for Intergovernmental Affairs and Public Engagement, managing White House Office of Public Engagement, Office of Intergovernmental Affairs, Office of Urban Affairs and White House Office of Olympic, Paralympic, and Youth Sport.]”
56. Tessa Tennant (née Davies) “[First Chair, co-founder and now trustee of the $71 trillion Carbon Disclosure Project ‘CDP’ launched by Cherie Blair on December 4, 2000; Tessa Tennant is a Matrix 5 Community organizer for CDP special investors who allegedly use a CO2e dictator game developed by Stephen Harper, Robert Oxoby and Tom Flanagan at the University of Calgary to place members’ pension funds in fraudulent and extortionate catastrophe bonds; she allegedly set up a 911 cat bond with HSBC/D2 Banking to be triggered by the murder of CO2e founder Carlton Bartels in WTC#1 and the double-occurrence cat bond demolition of the Twin Towers; Tennant is Chair of The Ice Organisation Ltd, an environmental kickback program designed to bribe selected consumer and punish others; co-founder of UK’s first equity investment fund for sustainable development in 1988; Trustee Chair of the Global Cool Foundation; first Chair and co-founder of The Association for Sustainable and Responsible Investment in Asia (ASrIA) based in Hong Kong and of the UK Social Investment Forum; former Board member of the Calvert Social Funds, Washington DC 1993-2009; served on environmental advisory panels for the UK Government and, The UN Environment Programme launched by the genocidal pedophile Maurice Strong in 1972, and HRH the Prince of Wales in an extorted partnership with DLA Piper; Fellow of the Schumacher Society].”
 59. Laureen Ann Harper (née Teskey) “[Revised September 16, 2012. Matrix 5 principal and wife of allegedly extorted man-in-the-middle Stephen Harper, Canada’s 22nd Prime Minister who was formerly a computer programmer and systems integrator, first in the Alberta oil fields and later with Imperial Oil in Calgary; she allegedly began working on a graphical interface with Macdonald Dettwiler and Associates for an RCMP-FBI Joint Automated Booking Station (‘JABS’) in 1996; she allegedly used Libor-rated funds to develop a graphical user interface (‘GUI’) for MDA’s RapidEye snuff film production; she is allegedly aware that Macdonald Dettwiler and Associates used her interface to procure RapidEye images of the assassination of Saad al-Hilli after he had threatened to expose the role of the British Bankers’ Association and Ba’ath Party leaders in the theft of $32 billion from the UN Oil For Food program; she is allegedly aware of the snuff-film methods used by BBA insiders to ensure the loyalty and obedience of orphaned (bona vacantia) children and similarly situated family members; she allegedly developed a phony social-media crime-scene investigation service for the launch of the Virtual Global Taskforce in 2003; she allegedly used the interface for the spoliation of images of crime scenes associated with kitty-porn fugitive Luka Magnotta and the murder of Chinese national Jun Lin in Montreal; she “made a pilgrimage” (a quote by husband) through 13 countries in Africa with a six-month trek in the mid-’80s; she allegedly secured safe passage on this one-woman (?) pilgrimage with guerrilla soldiers by helping them to produce snuff films for entrapment and extortion of victims of the SOS Children’s Villages pedophile trade; she is an expert with her husband on the vulnerability of the Federal Bridge Certification Authority to man-in-the middle propaganda attacks; she allegedly designed a graphical interface to support a web-based man-in-the-middle attack on the bridge of the USS Cole through a cell of traitors at HMCS Trinity, Halifax; in 2000, she allegedly used Macdonald Dettwiler and Associates’ MCOIN III system to backdoor the Trinity Federal Bridge Certification Authority; she allegedly configured MCOIN III to trick the USS Cole bridge commander into sailing to an ambush in Aden Harbor; she allegedly helped to generate and distribute a propaganda video for ambush of the USS Cole, best entitled ‘Wag the OBL Dog’; she allegedly used the Trinity Federal Bridge to track Piggy Palace Good Times Society assets (including EW pilot Russell Williams and victim DNA), through crime scenes associated with police entrapment and extortion at the Pickton pig farm in British Columbia; she allegedly integrated VideoGuard encryption with decoy graphics to sell footage of pre-insured death-by-plane events including Operation Nanook during August 2011 and Global Guardian / al-Qaeda war games of 911; she allegedly worked with Harper strategist and University of Calgary political scientist Tom Flanagan, on a graphical-user interface to the Carbon Disclosure Landlord Game, apparently played by Carlton Bartels before the snuff film made of the demolition of WTC#1 on 9/11; she is an alleged accessory – before or after the fact – to the development of Southern Alberta’s century-old pedophile trade by polygamous wives of leaders of the Church of Jesus Christ of Latter-Day Saints (Mormons); she is an alleged accessory – before or after the fact – to the development of a fifty-year old pedophile trade by the ‘Aunties’ and ‘Mothers’ of SOS Children’s Villages sponsored by Canadian Governors General including the late Jeanne Sauvé and her ‘bearded’ kickboxing partner, Michaelle Jean; she was born in Turner Valley, rural town south-west of Calgary, Alberta; her parents were ranchers who owned an electrical contracting company; parents divorced in 1991; she graduated from Oilfields High School; she dumped journalism and focused on photography at the Southern Alberta Institute of Technology with emphasis on computer-generated graphics; she was married to New Zealander Neil Fenton – met on trek – from 1985 to 1988 in Canada; she was a graphic artist for GTO Printing, but Fenton wanted to own a restaurant; children were not in the plan and they split in 1988; she allegedly infiltrated the Calgary Progressive Conservative Party through MP Jim Hawkes; she allegedly infiltrated the Reform Party of Canada in the late 1980s; she allegedly generated propaganda graphics for party, including poster for Reform MP Deborah Grey who had taken Stephen Harper to Ottawa as her assistant; she met Harper at a Reform Party assembly in Saskatoon in 1990; she helped him with graphics for his M.A. thesis; they were married in 1993 by a justice of the peace in their house in Calgary’s Scenic Acres neighborhood; she has gender-identity issues; she was a wild high-school rabble rouser; she was a down and dirty Chick Flick dirt bike owner; she was allegedly disarmed by Grade 12 boys in a chainsaw incident; she operated a blowtorch while spot welding a gala chandelier; she acts the part of radical feminista and gets last word with her husband even inside G8, G20; she covertly directs CSIS/RCMP monitoring and security through Entrust backdoor into .tv; she models herself on the militant Maureen McTeer and the control-freak wife Aline Chrétien; she allegedly uses Blackberry to text messages to gay male friends about cute male air stewards [and pilots?] she encounters while traveling; she ran a successful graphical user interface design company from 1989 to 2002; she became the breadwinner for her family while Harper honed his political skills; she allegedly hijacked the REFORM party and its Canadian Alliance offshoot; she used her business to extort her ‘nerdy’ husband as a “kept man” in 2002; she funded Harper’s challenge to Stockwell DAY for leadership of the CANADIAN ALLIANCE, the offshoot of Reform; she designed signs for Harper that violated party specs; she rejected family’s Progressive Conservative agenda for gender-identity schtick; she rejected her family’s roots in United Church; she forced Harper to make formal apology to Chinese community for head tax levied on Chinese workers in late 19th century; her radar is all attuned to optics; she arrived in Ottawa as Laureen Teskey, a folksy, motorcycle-riding Albertan, joked about “mucky-mucks” and drank beer from the bottle; post-2006 election, she’s been retrofitted; she is informally called “first lady” by PMO; she was a booster for the proposed North American Free Trade Agreement to strengthen Matrix 5 power over the sovereign state of CANADA to the benefit of the 100+ Livery Companies; when the new leader of the Opposition and his family relocated to Ottawa, her sister, Diana, took over remaining contracts and she allegedly continued to use a video camera for sexual entrapment of members of the ‘patriarchy’ by her Chick Flick friends; the perception among staffers is that the couple have been scheming their way to 24 Sussex for the last 15 years; she recently extorted husband into appointing SOS patron David Johnston as governor general while sweetening the pot for his wife Sharon with free rides at RCMP stables; she allegedly forced Johnston to host Aga Khan – sponsor of Crown Agents – and promote SOS / Matrix 5 propaganda for the indoctrination of young children between birth and 3 and even prenatal; she allegedly forced Johnston to authorize burning of Russell Williams uniforms and is inferred guilty of spoliation of evidence of a Privy Council pedophile trade through the SOS; she is allegedly party to the spoliation of evidence of the contract killing of two alleged witnesses to the SOS pedophile trade, Jessica Lloyd and Marie-France Comeau; she allegedly used Blackberry/Entrust devices to order RCMP/Military Police to drop crime scene investigations into SOS-generated child and snuff-film pornography on EW pilot Russell Williams .tv computer files.]”
59. Laureen Ann Harper (née Teskey) “[Revised September 16, 2012. Matrix 5 principal and wife of allegedly extorted man-in-the-middle Stephen Harper, Canada’s 22nd Prime Minister who was formerly a computer programmer and systems integrator, first in the Alberta oil fields and later with Imperial Oil in Calgary; she allegedly began working on a graphical interface with Macdonald Dettwiler and Associates for an RCMP-FBI Joint Automated Booking Station (‘JABS’) in 1996; she allegedly used Libor-rated funds to develop a graphical user interface (‘GUI’) for MDA’s RapidEye snuff film production; she is allegedly aware that Macdonald Dettwiler and Associates used her interface to procure RapidEye images of the assassination of Saad al-Hilli after he had threatened to expose the role of the British Bankers’ Association and Ba’ath Party leaders in the theft of $32 billion from the UN Oil For Food program; she is allegedly aware of the snuff-film methods used by BBA insiders to ensure the loyalty and obedience of orphaned (bona vacantia) children and similarly situated family members; she allegedly developed a phony social-media crime-scene investigation service for the launch of the Virtual Global Taskforce in 2003; she allegedly used the interface for the spoliation of images of crime scenes associated with kitty-porn fugitive Luka Magnotta and the murder of Chinese national Jun Lin in Montreal; she “made a pilgrimage” (a quote by husband) through 13 countries in Africa with a six-month trek in the mid-’80s; she allegedly secured safe passage on this one-woman (?) pilgrimage with guerrilla soldiers by helping them to produce snuff films for entrapment and extortion of victims of the SOS Children’s Villages pedophile trade; she is an expert with her husband on the vulnerability of the Federal Bridge Certification Authority to man-in-the middle propaganda attacks; she allegedly designed a graphical interface to support a web-based man-in-the-middle attack on the bridge of the USS Cole through a cell of traitors at HMCS Trinity, Halifax; in 2000, she allegedly used Macdonald Dettwiler and Associates’ MCOIN III system to backdoor the Trinity Federal Bridge Certification Authority; she allegedly configured MCOIN III to trick the USS Cole bridge commander into sailing to an ambush in Aden Harbor; she allegedly helped to generate and distribute a propaganda video for ambush of the USS Cole, best entitled ‘Wag the OBL Dog’; she allegedly used the Trinity Federal Bridge to track Piggy Palace Good Times Society assets (including EW pilot Russell Williams and victim DNA), through crime scenes associated with police entrapment and extortion at the Pickton pig farm in British Columbia; she allegedly integrated VideoGuard encryption with decoy graphics to sell footage of pre-insured death-by-plane events including Operation Nanook during August 2011 and Global Guardian / al-Qaeda war games of 911; she allegedly worked with Harper strategist and University of Calgary political scientist Tom Flanagan, on a graphical-user interface to the Carbon Disclosure Landlord Game, apparently played by Carlton Bartels before the snuff film made of the demolition of WTC#1 on 9/11; she is an alleged accessory – before or after the fact – to the development of Southern Alberta’s century-old pedophile trade by polygamous wives of leaders of the Church of Jesus Christ of Latter-Day Saints (Mormons); she is an alleged accessory – before or after the fact – to the development of a fifty-year old pedophile trade by the ‘Aunties’ and ‘Mothers’ of SOS Children’s Villages sponsored by Canadian Governors General including the late Jeanne Sauvé and her ‘bearded’ kickboxing partner, Michaelle Jean; she was born in Turner Valley, rural town south-west of Calgary, Alberta; her parents were ranchers who owned an electrical contracting company; parents divorced in 1991; she graduated from Oilfields High School; she dumped journalism and focused on photography at the Southern Alberta Institute of Technology with emphasis on computer-generated graphics; she was married to New Zealander Neil Fenton – met on trek – from 1985 to 1988 in Canada; she was a graphic artist for GTO Printing, but Fenton wanted to own a restaurant; children were not in the plan and they split in 1988; she allegedly infiltrated the Calgary Progressive Conservative Party through MP Jim Hawkes; she allegedly infiltrated the Reform Party of Canada in the late 1980s; she allegedly generated propaganda graphics for party, including poster for Reform MP Deborah Grey who had taken Stephen Harper to Ottawa as her assistant; she met Harper at a Reform Party assembly in Saskatoon in 1990; she helped him with graphics for his M.A. thesis; they were married in 1993 by a justice of the peace in their house in Calgary’s Scenic Acres neighborhood; she has gender-identity issues; she was a wild high-school rabble rouser; she was a down and dirty Chick Flick dirt bike owner; she was allegedly disarmed by Grade 12 boys in a chainsaw incident; she operated a blowtorch while spot welding a gala chandelier; she acts the part of radical feminista and gets last word with her husband even inside G8, G20; she covertly directs CSIS/RCMP monitoring and security through Entrust backdoor into .tv; she models herself on the militant Maureen McTeer and the control-freak wife Aline Chrétien; she allegedly uses Blackberry to text messages to gay male friends about cute male air stewards [and pilots?] she encounters while traveling; she ran a successful graphical user interface design company from 1989 to 2002; she became the breadwinner for her family while Harper honed his political skills; she allegedly hijacked the REFORM party and its Canadian Alliance offshoot; she used her business to extort her ‘nerdy’ husband as a “kept man” in 2002; she funded Harper’s challenge to Stockwell DAY for leadership of the CANADIAN ALLIANCE, the offshoot of Reform; she designed signs for Harper that violated party specs; she rejected family’s Progressive Conservative agenda for gender-identity schtick; she rejected her family’s roots in United Church; she forced Harper to make formal apology to Chinese community for head tax levied on Chinese workers in late 19th century; her radar is all attuned to optics; she arrived in Ottawa as Laureen Teskey, a folksy, motorcycle-riding Albertan, joked about “mucky-mucks” and drank beer from the bottle; post-2006 election, she’s been retrofitted; she is informally called “first lady” by PMO; she was a booster for the proposed North American Free Trade Agreement to strengthen Matrix 5 power over the sovereign state of CANADA to the benefit of the 100+ Livery Companies; when the new leader of the Opposition and his family relocated to Ottawa, her sister, Diana, took over remaining contracts and she allegedly continued to use a video camera for sexual entrapment of members of the ‘patriarchy’ by her Chick Flick friends; the perception among staffers is that the couple have been scheming their way to 24 Sussex for the last 15 years; she recently extorted husband into appointing SOS patron David Johnston as governor general while sweetening the pot for his wife Sharon with free rides at RCMP stables; she allegedly forced Johnston to host Aga Khan – sponsor of Crown Agents – and promote SOS / Matrix 5 propaganda for the indoctrination of young children between birth and 3 and even prenatal; she allegedly forced Johnston to authorize burning of Russell Williams uniforms and is inferred guilty of spoliation of evidence of a Privy Council pedophile trade through the SOS; she is allegedly party to the spoliation of evidence of the contract killing of two alleged witnesses to the SOS pedophile trade, Jessica Lloyd and Marie-France Comeau; she allegedly used Blackberry/Entrust devices to order RCMP/Military Police to drop crime scene investigations into SOS-generated child and snuff-film pornography on EW pilot Russell Williams .tv computer files.]” 60. Anne Lauvergeon (possibly bred for Matrix 5 through SOS Children’s Villages) “[École Normale Supérieure Agrégation in physics (1978); Corps des Mines vocational courses (1983 Usinor then 1984 Commissariat à l’énergie atomique chemical safety in Europe – Chernobyl saboteur?); l’Inspection générale des carrières (1985-1988); in charge of French President François Mitterrand’s mission for international economy and foreign trade in 1990; 1991 assistant secretary general; “sherpa”, i.e. personal representative (sexual extrtionist?) to the president; charged with preparing international meetings such as the G7 summit; managing partner of Lazard banking (Matrix 1) in 1995; general director of Alcatel 1997 before becoming part of the group’s executive committee; CEO Cogema June 1999, succeeding Jean Syrota, who was extrorted from office by The Greens; merged Cogema, Framatome and other companies to create Areva in July 2001; American magazine Fortune, ranked her as the 2nd most powerful women in Europe in 2006 behind Patricia Russo, future president of Alcatel-Lucent; chaired “national contest of assistance the creation of companies of innovating technologies (Guild of Patented Hits?)” with salary of €305,000, bonus of €122,000 and “golden parachute” of two years’ wages; she, through Areva, encountered or created difficulties with new European [Matrix 2 and 3] Pressurized Reactor at end of 2006; announced an expected delay of eighteen months to three years for its delivery to first of its kind in Finland; President École Nationale Supérieure des Mines de Nancy; director or board member of Suez, Total S.A., Safran S.A. and Vodafone; addressing journalists outside the “Women’s Forum” organised in Deauville on October 16 2009, she declared on France 2 evening news, “To be clear, with same competences, sorry, we will choose the woman or something else [lesbian pedophile – Matrix 4 and 5?] rather than the white male”; 2010 from 3rd to 6th, she was at Bilderberg conference in Sitges, Spain; member of Trilateral Commission; in 2009; ranked by the magazine Forbes as the ninth-most powerful woman in the world.]”
60. Anne Lauvergeon (possibly bred for Matrix 5 through SOS Children’s Villages) “[École Normale Supérieure Agrégation in physics (1978); Corps des Mines vocational courses (1983 Usinor then 1984 Commissariat à l’énergie atomique chemical safety in Europe – Chernobyl saboteur?); l’Inspection générale des carrières (1985-1988); in charge of French President François Mitterrand’s mission for international economy and foreign trade in 1990; 1991 assistant secretary general; “sherpa”, i.e. personal representative (sexual extrtionist?) to the president; charged with preparing international meetings such as the G7 summit; managing partner of Lazard banking (Matrix 1) in 1995; general director of Alcatel 1997 before becoming part of the group’s executive committee; CEO Cogema June 1999, succeeding Jean Syrota, who was extrorted from office by The Greens; merged Cogema, Framatome and other companies to create Areva in July 2001; American magazine Fortune, ranked her as the 2nd most powerful women in Europe in 2006 behind Patricia Russo, future president of Alcatel-Lucent; chaired “national contest of assistance the creation of companies of innovating technologies (Guild of Patented Hits?)” with salary of €305,000, bonus of €122,000 and “golden parachute” of two years’ wages; she, through Areva, encountered or created difficulties with new European [Matrix 2 and 3] Pressurized Reactor at end of 2006; announced an expected delay of eighteen months to three years for its delivery to first of its kind in Finland; President École Nationale Supérieure des Mines de Nancy; director or board member of Suez, Total S.A., Safran S.A. and Vodafone; addressing journalists outside the “Women’s Forum” organised in Deauville on October 16 2009, she declared on France 2 evening news, “To be clear, with same competences, sorry, we will choose the woman or something else [lesbian pedophile – Matrix 4 and 5?] rather than the white male”; 2010 from 3rd to 6th, she was at Bilderberg conference in Sitges, Spain; member of Trilateral Commission; in 2009; ranked by the magazine Forbes as the ninth-most powerful woman in the world.]”
 61. Sheikha Mozah bint Nasser Al Missned (nee Missned 1959) “[Allegedly recruited in 1984 – 1986 while studying Sociology at Qatar University, for a career as a Matrix 5 sextortionist by Henry Bienen, a CIA handler and future president of Northwestern University; she was recruited in a period when the CIA has enough professors under Agency contract to staff a large university; she is the second of the three wives of Sheikh Hamad bin Khalifa Al Thani, an allegedly-extorted man-in-the-middle and Emir of the State of Qatar; daughter of the late Nasser bin Abdullah Al Missned, an opponent of Sheikh Khalifa bin Hamad bin Abdallah Al Thani, father of the current Emir; her family lived in exile in Egypt and Kuwait, but returned to Qatar for the Sheikha’s marriage; she married the Emir (at the time Heir Apparent) in 1977 at the age of 18, while she was attending Qatar University; she is Chairperson of the Qatar Foundation for Education, Science and Community Development since 1995; Chairperson of Silatech since 2008; Chairperson of the Arab Democracy Foundation; President of the Supreme Council for Family Affairs since 1998; Vice-President of the Supreme Education Council since 2002; she was UNESCO’s Special Envoy for Basic and Higher Education in 2003; member of the Board of Overseers for Weill Cornell Medical College; currently Chair of Sidra Medical and Research Center in Doha and the organisation “Your Link”; she is the de facto boss of Education City and Al Jazeera Children’s Channel with access to the Entrust public keys needed to inject Matrix 5 propaganda into .tv broadcasts by Aljazeera, al Qaeda and the BBC; she allegedly recruited Khalid Sheikh Mohammed “the principal architect of the 9/11 attacks” and many of the most significant terrorist plots over the last twenty years, including the World Trade Center 1993 bombings, the Operation Bojinka plot, an aborted 2002 attack on the U.S. Bank Tower in Los Angeles, the Bali nightclub bombings, the failed bombing of American Airlines Flight 63, the Millennium Plot, and the murder of Daniel Pearl; she allegedly arranged for KSM to attend the North Carolina Agricultural and Technical State University and complete a degree in mechanical engineering in 1986; the following years she sent him to Afghanistan, where he and his brothers (Zahed, Abed, and Aref) fought against the Soviet Union during the Soviet invasion of Afghanistan; she introduced KSM to Abdul Rasul Sayyaf, of the Islamic Union Party who although officially a member of the Northern Alliance, assisted the assassins posing as journalists that killed anti-Taliban leader Ahmad Shah Massoud by detonating a bomb hidden in their video camera; she sent KSM to Bosnia in September 1995 to work there, under an assumed name, for Egyptian Relief, as a humanitarian aid worker; she obtained Bosnian citizenship for KSM in November 1995; she arranged for Sheikh Abdullah Bin Khalid Al-Thani, then Qatari Minister of Religious Affairs, to shelter KSM before sending him to Pakistan in 1996 to avoid capture by legitimate U.S. authorities; she allegedly arranged with Bienen and Michelle Obama that KSM, captured in Rawalpindi, Pakistan, on March 1, 2003, be kept incommunicado at Guantanamo Bay to protect the Matrix 5 conspirators]”
61. Sheikha Mozah bint Nasser Al Missned (nee Missned 1959) “[Allegedly recruited in 1984 – 1986 while studying Sociology at Qatar University, for a career as a Matrix 5 sextortionist by Henry Bienen, a CIA handler and future president of Northwestern University; she was recruited in a period when the CIA has enough professors under Agency contract to staff a large university; she is the second of the three wives of Sheikh Hamad bin Khalifa Al Thani, an allegedly-extorted man-in-the-middle and Emir of the State of Qatar; daughter of the late Nasser bin Abdullah Al Missned, an opponent of Sheikh Khalifa bin Hamad bin Abdallah Al Thani, father of the current Emir; her family lived in exile in Egypt and Kuwait, but returned to Qatar for the Sheikha’s marriage; she married the Emir (at the time Heir Apparent) in 1977 at the age of 18, while she was attending Qatar University; she is Chairperson of the Qatar Foundation for Education, Science and Community Development since 1995; Chairperson of Silatech since 2008; Chairperson of the Arab Democracy Foundation; President of the Supreme Council for Family Affairs since 1998; Vice-President of the Supreme Education Council since 2002; she was UNESCO’s Special Envoy for Basic and Higher Education in 2003; member of the Board of Overseers for Weill Cornell Medical College; currently Chair of Sidra Medical and Research Center in Doha and the organisation “Your Link”; she is the de facto boss of Education City and Al Jazeera Children’s Channel with access to the Entrust public keys needed to inject Matrix 5 propaganda into .tv broadcasts by Aljazeera, al Qaeda and the BBC; she allegedly recruited Khalid Sheikh Mohammed “the principal architect of the 9/11 attacks” and many of the most significant terrorist plots over the last twenty years, including the World Trade Center 1993 bombings, the Operation Bojinka plot, an aborted 2002 attack on the U.S. Bank Tower in Los Angeles, the Bali nightclub bombings, the failed bombing of American Airlines Flight 63, the Millennium Plot, and the murder of Daniel Pearl; she allegedly arranged for KSM to attend the North Carolina Agricultural and Technical State University and complete a degree in mechanical engineering in 1986; the following years she sent him to Afghanistan, where he and his brothers (Zahed, Abed, and Aref) fought against the Soviet Union during the Soviet invasion of Afghanistan; she introduced KSM to Abdul Rasul Sayyaf, of the Islamic Union Party who although officially a member of the Northern Alliance, assisted the assassins posing as journalists that killed anti-Taliban leader Ahmad Shah Massoud by detonating a bomb hidden in their video camera; she sent KSM to Bosnia in September 1995 to work there, under an assumed name, for Egyptian Relief, as a humanitarian aid worker; she obtained Bosnian citizenship for KSM in November 1995; she arranged for Sheikh Abdullah Bin Khalid Al-Thani, then Qatari Minister of Religious Affairs, to shelter KSM before sending him to Pakistan in 1996 to avoid capture by legitimate U.S. authorities; she allegedly arranged with Bienen and Michelle Obama that KSM, captured in Rawalpindi, Pakistan, on March 1, 2003, be kept incommunicado at Guantanamo Bay to protect the Matrix 5 conspirators]” 62. Carole Taylor (nee Carol Goss) “[Matrix 5 wife of allegedly extorted man-in-the-middle husband Art Phillips; she was an Independent member of Vancouver City Council from 1986 to 1990; wife and husband allegedly worked with Linda and David Pickton on the pig-farm development when the women began to disappear from the Downtown Eastside; in that same period Gordon Campbell, the husband of Matrix 5 wife Nancy Campbell, was mayor and police board chair in Vancouver in the same position as that held by Taylor’s husband from 1973 to 1977; the alleged pig-farm conspirators were extorting Port Coquitlam city councilors to allow them to develop the farmland as part of the larger Riverwood community and get their property removed from the Agricultural Land Reserve to make huge profits for the pig-farm pension-fund insiders; the proposal was finally approved in 1986; Taylor was pushing her husband to file applications for rezoning for subdivision on the land that was being examined when Willie Pickton was arrested in February 2002, allegedly as a cutout for Matrix 5 community groups; since June 17, 2011, Taylor has served as the Chancellor of Simon Fraser University where she has allegedly corrupted faculty into supporting the pig-farm pension carbon scam; she was B.C. Minister of Finance from 2005 until 2008 in the government of Liberal premier Gordon Campbell; she graduated from Weston Collegiate in 1964; she graduated from Victoria College at the University of Toronto with a BA in English; she was Miss Toronto 1964; she was co-host of CFTO-TV’s After Four, a show for teenagers; she appeared on several other CFTO shows, including Toronto Today, Topic, and her own Carole Taylor Show; she and Percy Saltzman were the first co-hosts of Canada AM when the show premiered on CTV in 1972; CTV would in 2010 broadcast a documentary “The Pig Farm” making Willie the cutout for Matrix 5 murder for hire; she was a former host of W-FIVE and Pacific Report; her career in journalism lasted for over 20 years; she and Nancy Campbell and Linda Pickton allegedly ensured that there was no money to pay Willie’s legal fees forcing the government to borrow from the pig farm pension fund (bcIMC) and thereby compromise its unwitting members including the police; she served as chair of the Vancouver Board of Trade from 2001 to 2002 through 911; she was chair of the Canadian Broadcasting Corporation from July 16, 2001, until March 14, 2005 and therefore she was the fiduciary responsible for the .tv broadcasts of man-in-the-middle propaganda of the 911 attack on America; she resigned from the CBC in order to seek the nomination of the British Columbia Liberal Party in the province’s 2005 election; on May 17, 2005, she was elected to Legislative Assembly of British Columbia as the member representing Vancouver-Langara; on June 16, 2005, she was named Minister of Finance; she signed up 100% of all BC public sector contracts before they were set to expire by offering potential strikers a share in the revenues collected through the pig farm pension plan from the first carbon tax to be applied anywhere in North America; as Finance Minister, she ended the corporate capital tax on banks and then joined Frank McKenna on the TD Bank board’ McKenna is a CAI Private Equity investor in MDA’s MindBox debt-recovery service and the ex-chair of CanWest Global Communications; he helped put Conrad Black into jail and thereby silence a prospective whistleblower who threatened to expose Taylor’s role in the Pig Farm Pension Carbon scam; on December 18, 2008, Taylor announced her resignation from the Legislative Assembly after accepting an appointment to a federal Ministry of Finance advisory panel where she allegedly is trying to accelerate kickbacks into pig-farm pension schemes across Canada from the $71 trillion CDP; she allegedly sponsored CTV .tv documentary “The Pig Farm” in 2010 as a limited hangout to maintain Willie as cutout; she now protects Matrix 5 banking, anglophone, francophone, lesbian and pedophile communities and the snuff films which record oaths of loyalty (?) to the Carbon Disclosure Project]”
62. Carole Taylor (nee Carol Goss) “[Matrix 5 wife of allegedly extorted man-in-the-middle husband Art Phillips; she was an Independent member of Vancouver City Council from 1986 to 1990; wife and husband allegedly worked with Linda and David Pickton on the pig-farm development when the women began to disappear from the Downtown Eastside; in that same period Gordon Campbell, the husband of Matrix 5 wife Nancy Campbell, was mayor and police board chair in Vancouver in the same position as that held by Taylor’s husband from 1973 to 1977; the alleged pig-farm conspirators were extorting Port Coquitlam city councilors to allow them to develop the farmland as part of the larger Riverwood community and get their property removed from the Agricultural Land Reserve to make huge profits for the pig-farm pension-fund insiders; the proposal was finally approved in 1986; Taylor was pushing her husband to file applications for rezoning for subdivision on the land that was being examined when Willie Pickton was arrested in February 2002, allegedly as a cutout for Matrix 5 community groups; since June 17, 2011, Taylor has served as the Chancellor of Simon Fraser University where she has allegedly corrupted faculty into supporting the pig-farm pension carbon scam; she was B.C. Minister of Finance from 2005 until 2008 in the government of Liberal premier Gordon Campbell; she graduated from Weston Collegiate in 1964; she graduated from Victoria College at the University of Toronto with a BA in English; she was Miss Toronto 1964; she was co-host of CFTO-TV’s After Four, a show for teenagers; she appeared on several other CFTO shows, including Toronto Today, Topic, and her own Carole Taylor Show; she and Percy Saltzman were the first co-hosts of Canada AM when the show premiered on CTV in 1972; CTV would in 2010 broadcast a documentary “The Pig Farm” making Willie the cutout for Matrix 5 murder for hire; she was a former host of W-FIVE and Pacific Report; her career in journalism lasted for over 20 years; she and Nancy Campbell and Linda Pickton allegedly ensured that there was no money to pay Willie’s legal fees forcing the government to borrow from the pig farm pension fund (bcIMC) and thereby compromise its unwitting members including the police; she served as chair of the Vancouver Board of Trade from 2001 to 2002 through 911; she was chair of the Canadian Broadcasting Corporation from July 16, 2001, until March 14, 2005 and therefore she was the fiduciary responsible for the .tv broadcasts of man-in-the-middle propaganda of the 911 attack on America; she resigned from the CBC in order to seek the nomination of the British Columbia Liberal Party in the province’s 2005 election; on May 17, 2005, she was elected to Legislative Assembly of British Columbia as the member representing Vancouver-Langara; on June 16, 2005, she was named Minister of Finance; she signed up 100% of all BC public sector contracts before they were set to expire by offering potential strikers a share in the revenues collected through the pig farm pension plan from the first carbon tax to be applied anywhere in North America; as Finance Minister, she ended the corporate capital tax on banks and then joined Frank McKenna on the TD Bank board’ McKenna is a CAI Private Equity investor in MDA’s MindBox debt-recovery service and the ex-chair of CanWest Global Communications; he helped put Conrad Black into jail and thereby silence a prospective whistleblower who threatened to expose Taylor’s role in the Pig Farm Pension Carbon scam; on December 18, 2008, Taylor announced her resignation from the Legislative Assembly after accepting an appointment to a federal Ministry of Finance advisory panel where she allegedly is trying to accelerate kickbacks into pig-farm pension schemes across Canada from the $71 trillion CDP; she allegedly sponsored CTV .tv documentary “The Pig Farm” in 2010 as a limited hangout to maintain Willie as cutout; she now protects Matrix 5 banking, anglophone, francophone, lesbian and pedophile communities and the snuff films which record oaths of loyalty (?) to the Carbon Disclosure Project]” 63. Nancy Campbell (nee Chipperfield) “[Revised March 7, 2013. Matrix 5 wife of allegedly extorted man-in-the-middle Gordon Campbell, the 34th Premier of British Columbia from 2001 to 2011 who currently serves as Canadian High Commissioner to the United Kingdom of Great Britain and Northern Ireland; she allegedly procured a Macdonald Dettwiler mobile-radio system through her husband, to support Matrix 5 man-in-the-middle propaganda attacks on the Nortel public key infrastructure (PKI) communications systems used by RCMP / Vancouver officers to track snuff-film victims through the Pickton pig farm; she allegedly directed her associates in the B.C. Teachers pension plan – now merged into bcIMC – to sponsor a pig farm mortgage through the Treasury Solicitor’s Bona Vacantia (‘ownerless goods’) account; she allegedly had bcIMC trustees take a position in MDA to control the pig farm mortgage through BC OnLine and Serco U.K., operator of the stratum 0 spot fixing clock used to time stamp snuff-film images; she allegedly used the mortgage to helped to finance the construction of Piggy’s Palace Good Times Society post-production studio; she allegedly used the Piggy’s Palace studio to procure VideoGuard-encrypted content for Matrix 5 propaganda and pay-per-view snuff-film trades; she allegedly arranged a profit-sharing agreement for the trades with fellow members of her ‘pig farm’ pension fund; she allegedly directed the bcIMC pension fund to move asset management into the TSol Carbon Disclosure Project and invest in A&E, News Corp, BCE etc. which use VideoGuard in pay per view encryption; she graduated from Sir Winston Churchill school; she was a former French teacher at Queen Mary elementary and Lord Byng secondary schools; she was a former vice principal at Sir Winston Churchill school where Justin Trudeau, eldest son of the late Pierre Trudeau formerly taught French & social studies; Justin is the alleged half brother of Lena Trudeau who set up the Pig Farm Piggy’s Palace Good Times Society to entrap Canadian Privy Council at cannibal oath ceremonies; Nancy Campbell’s Churchill is one of two International Baccalaureate schools and one of three French Immersion secondary schools in Vancouver; she was a vice principal at Templeton secondary school; she retired as principal at Howe Sound Secondary School in Squamish in 2009; after she graduated from UBC in 1969 and Gordon Campbell graduated from Dartmouth College, they were married in New Westminster on July 4, 1970; the couple went to Nigeria to teach under the Canadian University Service Oversea; this program was allegedly structured with SOS Children’s Villages by the de-populationist Maurice Strong allegedly to entrap young Canadians in filmed pedophile-oath taking ceremonies with images that could be used later to extort them in subsequent careers; we note that the Lagos State Government provided a piece of land in Isolo, a suburb of Lagos to construct the first SOS Children’s Village in Nigeria which was started in 1970; on return from Nigeria, the allegedly compromised Nancy Campbell completed her education degree at UBC while he entered the UBC law school; he became a realty development manager and a small businessman; he then worked as an executive assistant to Vancouver Mayor Art Phillips from 1973 to 1976; she allegedly used her teachers’ pig-farm union connections to place her husband as a Vancouver city councilor from 1984 to 1986; she used the same leverage to control him during his stint as mayor and police board chair from 1986 to 1993, around the time that women began disappearing from the Downtown Eastside; she continued to leverage the teachers union to place him as Leader of the BC Liberals in 1993; she leveraged his leadership of the BC Liberals to a massive victory in the 2001 BC provincial election when he was sworn in as Premier of British Columbia prior to the 911 attack; the attackers of 911, allegedly used bcIMC pig-farm pension fund investment in Macdonald Dettwiler’s MindBox to trigger distressed debt recovery on property in New York and enrich fellow pig farm investors in the Carbon Disclosure Projects; she helped her husband to lead the BC Liberals to two more majority governments in the 2005 BC provincial election and the 2009 BC provincial election; she drove her husband to establish the British Columbia Investment Management Corporation (bcIMC) under the authority of the Public Sector Pension Plans Act passed by the British Columbia Legislature on July 15, 1999; she ensured that KPMG was appointed to audit bcIMC knowing it was involved in abusive tax shelters in the United States; she drove her husband to appoint as bcIMC custodian RBC Dexia Investor Services Trust which has allegedly fraudulently converted the assets of the fund into ‘bona vacantia’ with TSol allowing their use in contract hits; with bcIMC assets under administration of $79.7 billion as of March 31, 2010, she has allegedly helped leaders of the Vancouver Settlement Movement to extort control of the retirement benefits of more than 440,000 residents of British Columbia, including compromised police officers, teachers, the staff and faculty at the University of Victoria and erstwhile members of the B.C. Legislative Assembly; she is allegedly a Matrix 5 principal in the racketeering use by Settlement leaders of bcIMC cestui que, pig-farm pension and life insurance funds which cover two million voters and 197,000 employers in B.C.]”
63. Nancy Campbell (nee Chipperfield) “[Revised March 7, 2013. Matrix 5 wife of allegedly extorted man-in-the-middle Gordon Campbell, the 34th Premier of British Columbia from 2001 to 2011 who currently serves as Canadian High Commissioner to the United Kingdom of Great Britain and Northern Ireland; she allegedly procured a Macdonald Dettwiler mobile-radio system through her husband, to support Matrix 5 man-in-the-middle propaganda attacks on the Nortel public key infrastructure (PKI) communications systems used by RCMP / Vancouver officers to track snuff-film victims through the Pickton pig farm; she allegedly directed her associates in the B.C. Teachers pension plan – now merged into bcIMC – to sponsor a pig farm mortgage through the Treasury Solicitor’s Bona Vacantia (‘ownerless goods’) account; she allegedly had bcIMC trustees take a position in MDA to control the pig farm mortgage through BC OnLine and Serco U.K., operator of the stratum 0 spot fixing clock used to time stamp snuff-film images; she allegedly used the mortgage to helped to finance the construction of Piggy’s Palace Good Times Society post-production studio; she allegedly used the Piggy’s Palace studio to procure VideoGuard-encrypted content for Matrix 5 propaganda and pay-per-view snuff-film trades; she allegedly arranged a profit-sharing agreement for the trades with fellow members of her ‘pig farm’ pension fund; she allegedly directed the bcIMC pension fund to move asset management into the TSol Carbon Disclosure Project and invest in A&E, News Corp, BCE etc. which use VideoGuard in pay per view encryption; she graduated from Sir Winston Churchill school; she was a former French teacher at Queen Mary elementary and Lord Byng secondary schools; she was a former vice principal at Sir Winston Churchill school where Justin Trudeau, eldest son of the late Pierre Trudeau formerly taught French & social studies; Justin is the alleged half brother of Lena Trudeau who set up the Pig Farm Piggy’s Palace Good Times Society to entrap Canadian Privy Council at cannibal oath ceremonies; Nancy Campbell’s Churchill is one of two International Baccalaureate schools and one of three French Immersion secondary schools in Vancouver; she was a vice principal at Templeton secondary school; she retired as principal at Howe Sound Secondary School in Squamish in 2009; after she graduated from UBC in 1969 and Gordon Campbell graduated from Dartmouth College, they were married in New Westminster on July 4, 1970; the couple went to Nigeria to teach under the Canadian University Service Oversea; this program was allegedly structured with SOS Children’s Villages by the de-populationist Maurice Strong allegedly to entrap young Canadians in filmed pedophile-oath taking ceremonies with images that could be used later to extort them in subsequent careers; we note that the Lagos State Government provided a piece of land in Isolo, a suburb of Lagos to construct the first SOS Children’s Village in Nigeria which was started in 1970; on return from Nigeria, the allegedly compromised Nancy Campbell completed her education degree at UBC while he entered the UBC law school; he became a realty development manager and a small businessman; he then worked as an executive assistant to Vancouver Mayor Art Phillips from 1973 to 1976; she allegedly used her teachers’ pig-farm union connections to place her husband as a Vancouver city councilor from 1984 to 1986; she used the same leverage to control him during his stint as mayor and police board chair from 1986 to 1993, around the time that women began disappearing from the Downtown Eastside; she continued to leverage the teachers union to place him as Leader of the BC Liberals in 1993; she leveraged his leadership of the BC Liberals to a massive victory in the 2001 BC provincial election when he was sworn in as Premier of British Columbia prior to the 911 attack; the attackers of 911, allegedly used bcIMC pig-farm pension fund investment in Macdonald Dettwiler’s MindBox to trigger distressed debt recovery on property in New York and enrich fellow pig farm investors in the Carbon Disclosure Projects; she helped her husband to lead the BC Liberals to two more majority governments in the 2005 BC provincial election and the 2009 BC provincial election; she drove her husband to establish the British Columbia Investment Management Corporation (bcIMC) under the authority of the Public Sector Pension Plans Act passed by the British Columbia Legislature on July 15, 1999; she ensured that KPMG was appointed to audit bcIMC knowing it was involved in abusive tax shelters in the United States; she drove her husband to appoint as bcIMC custodian RBC Dexia Investor Services Trust which has allegedly fraudulently converted the assets of the fund into ‘bona vacantia’ with TSol allowing their use in contract hits; with bcIMC assets under administration of $79.7 billion as of March 31, 2010, she has allegedly helped leaders of the Vancouver Settlement Movement to extort control of the retirement benefits of more than 440,000 residents of British Columbia, including compromised police officers, teachers, the staff and faculty at the University of Victoria and erstwhile members of the B.C. Legislative Assembly; she is allegedly a Matrix 5 principal in the racketeering use by Settlement leaders of bcIMC cestui que, pig-farm pension and life insurance funds which cover two million voters and 197,000 employers in B.C.]”
 64. Elisabeth Freud (nee Murdoch) “[Revised April 29, 2012. She is a Matrix 5 principal and wife of the allegedly extorted man-in-the-middle Matthew Freud whom she married on 18 August 2001 at Blenheim Palace; she allegedly assembled a Wells Fargo-led financial consortium (codenamed Janus) to procure NATO AWACS aircraft to camouflage the pay-per-view story of al-Qaeda 9/11; she allegedly used Janus to acquire OpenBet Technology (formerly Orbis Technology) in December 2000 on behalf of NDS in support of news-driven spread bets; she allegedly used Fox News pay-per-view to place spread bets on the Twin Towers and WTC#7 demolition and profit from the “first live broadcast mass snuff film in human history”; she allegedly procured the public key used by Canadian Navy spies to execute a domain hack through a .tv antenna on the MS Costa Concordia and ground the vessel in an attempted insurance fraud on Lloyd’s of London on January 13, 2012; she attended exclusive schools in New York City and allegedly set up a dual use on-campus television station at Vassar College to entrap students in Greek Life oath ceremonies; she allegedly used her husband – millionaire head of Freud Communications – to manipulate public perception of Matrix 5 propaganda through setting up decoys on 911; she allegedly used her husband to set up a decoy planning base for the ‘Osama bin Laden’ attack through In-Flight Network and Freud Communications USA, based in New York City; she allegedly used her husband to manage decoys associated with the abduction of Madeleine McCann through Clarence Mitchell who joined Freud Communications as a consultant in 2008; she allegedly used her husband to manage decoys built through Mitchell’s phony advice to the parents of teenager Scarlet MacKeown who was murdered in Goa, the parents of murdered teenager Jimmy Mizen and the parents of missing teenager Amy Fitzpatrick; she allegedly used her husband and Rebekah Brooks to manage VideoGuard decoys built for the Treasury Solicitor in re the death of Princess Diana; she is the daughter of the allegedly extorted man-in-the-middle, Rupert Murdoch; she is the Matrix 5 former wife of allegedly extorted man-in-the-middle Elkin Kwesi Pianim whom she divorced in 1998; Pianin is a fellow Vassar graduate who allegedly helped her to develop a film archive of Greek Life cannibal oath ceremonies for the extortion of alumni and was an associate in the corporate finance department of New York investment bank Rothschild Inc.; she is the Chairwoman and CEO of Shine Limited, a television production company with offices in London and Manchester; she founded Shine in March 2001 with 80 percent equity owned by her, 15 percent by Lord Alli, and 5 percent by BSkyB, who signed a deal guaranteeing to buy an agreed amount of Shine programming for two years; she is the Matrix 5 business partner of allegedly extorted man-in-the-middle Waheed Alli, born 16 November 1964; she allegedly extorted Alli to produce content on 911 described as `the first live broadcast mass snuff film in human history’ for BBC, Five, Channel 4, HBO and the RTL Group; her business partner Alli merged Planet 24 – a television production company with an animation division Impossible TV, founded by Bob Geldof and Tony Boland (Television producer); Impossible TV allegedly produced the special effects of Ballistic 911 and 7/7 in a .tv joint venture with 24 Hour Productions headed by Charlie Parsons and Waheed, later Lord Alli; they sold it to Carlton Communications in 1999 and eventually merged with Carlton Productions, of which Lord Alli became managing director; her business partner Alli allegedly deployed David Cameron in Carlton Communications as a scout for 911.]”
64. Elisabeth Freud (nee Murdoch) “[Revised April 29, 2012. She is a Matrix 5 principal and wife of the allegedly extorted man-in-the-middle Matthew Freud whom she married on 18 August 2001 at Blenheim Palace; she allegedly assembled a Wells Fargo-led financial consortium (codenamed Janus) to procure NATO AWACS aircraft to camouflage the pay-per-view story of al-Qaeda 9/11; she allegedly used Janus to acquire OpenBet Technology (formerly Orbis Technology) in December 2000 on behalf of NDS in support of news-driven spread bets; she allegedly used Fox News pay-per-view to place spread bets on the Twin Towers and WTC#7 demolition and profit from the “first live broadcast mass snuff film in human history”; she allegedly procured the public key used by Canadian Navy spies to execute a domain hack through a .tv antenna on the MS Costa Concordia and ground the vessel in an attempted insurance fraud on Lloyd’s of London on January 13, 2012; she attended exclusive schools in New York City and allegedly set up a dual use on-campus television station at Vassar College to entrap students in Greek Life oath ceremonies; she allegedly used her husband – millionaire head of Freud Communications – to manipulate public perception of Matrix 5 propaganda through setting up decoys on 911; she allegedly used her husband to set up a decoy planning base for the ‘Osama bin Laden’ attack through In-Flight Network and Freud Communications USA, based in New York City; she allegedly used her husband to manage decoys associated with the abduction of Madeleine McCann through Clarence Mitchell who joined Freud Communications as a consultant in 2008; she allegedly used her husband to manage decoys built through Mitchell’s phony advice to the parents of teenager Scarlet MacKeown who was murdered in Goa, the parents of murdered teenager Jimmy Mizen and the parents of missing teenager Amy Fitzpatrick; she allegedly used her husband and Rebekah Brooks to manage VideoGuard decoys built for the Treasury Solicitor in re the death of Princess Diana; she is the daughter of the allegedly extorted man-in-the-middle, Rupert Murdoch; she is the Matrix 5 former wife of allegedly extorted man-in-the-middle Elkin Kwesi Pianim whom she divorced in 1998; Pianin is a fellow Vassar graduate who allegedly helped her to develop a film archive of Greek Life cannibal oath ceremonies for the extortion of alumni and was an associate in the corporate finance department of New York investment bank Rothschild Inc.; she is the Chairwoman and CEO of Shine Limited, a television production company with offices in London and Manchester; she founded Shine in March 2001 with 80 percent equity owned by her, 15 percent by Lord Alli, and 5 percent by BSkyB, who signed a deal guaranteeing to buy an agreed amount of Shine programming for two years; she is the Matrix 5 business partner of allegedly extorted man-in-the-middle Waheed Alli, born 16 November 1964; she allegedly extorted Alli to produce content on 911 described as `the first live broadcast mass snuff film in human history’ for BBC, Five, Channel 4, HBO and the RTL Group; her business partner Alli merged Planet 24 – a television production company with an animation division Impossible TV, founded by Bob Geldof and Tony Boland (Television producer); Impossible TV allegedly produced the special effects of Ballistic 911 and 7/7 in a .tv joint venture with 24 Hour Productions headed by Charlie Parsons and Waheed, later Lord Alli; they sold it to Carlton Communications in 1999 and eventually merged with Carlton Productions, of which Lord Alli became managing director; her business partner Alli allegedly deployed David Cameron in Carlton Communications as a scout for 911.]”
 65. Rebekah Brooks (née Rebekah Mary Wade; born 27 May 1968) “[Revised June 13, 2012. Matrix 5 aide to allegedly extorted men-in-the-middle, Rupert Murdoch and his two sons; she allegedly worked with Romney’s Bain and Common Purpose partners to develop VideoGuard pay-per-view encryption codes to conceal child pornography and snuff-film trades; she allegedly worked with Common Purpose graduate Adele Blakebrough to archive encrypted snuff films with Clifford Chance clients at Canary Wharf (Citi); she is the Matrix 5 former wife of Ross Kemp, the ex-EastEnders actor who once described her as a ‘homophobic cow’; she is the Matrix 5 associate of allegedly extorted men-in-the-middle alumni of the Bullingdon Club and their relatives, including Mayor of London Boris Johnson’s Middle Templar wife, Marina (see # 66) ; Matrix 5 former boss of NOTW staff who appeared elated when she sacked them and shut down the paper – allegedly creating a decoy to protect the Middle Temple pedophile trade; alleged expert user of PwC’s beTrusted and Entrust public key infrastructure to decoy crime scenes such as those associated with Holly Wells, Jessica Chapman, Maddy McCann and Gareth Williams; alleged expert user of PwC’s beTrusted and Entrust public key infrastructure to divert investigators from Matrix 5 man-in-the-middle attacks and a centuries-old Middle Temple pedophile entrapment trade; allegedly recruited into the Matrix 5 extortion racket in the mid’ 80s in Paris by agents of the late Jeanne Sauve, then-Governor General of Canada and patron of SOS Children’s Villages – an alleged, supranational network of pedophile entrapment and oath-taking centers funded by D2 Banking and HSBC out of Canada Square, Canary Wharf; allegedly set up ‘off-campus’ pedophile entrapment centers for alumni, faculty and students at the Sorbonne in Paris; allegedly procured Sun-Mozilla PKI – public key infrastructure – ‘hides’ for clients of Canary Wharf-based PKI Services, including NATO, United Nations and News International cutouts in the FBI, U.S. Marshals Service, Interpol and the Metropolitan Police to operate dual-use cells as virtual private networks for sabotage, assassination and deception; allegedly set up NATO ‘Skyhackers’ with public key infrastructure used at News International to stage the Matrix 5 ambush of U.S. Navy Seals who threatened to expose Barack Obama’s use of the same technology to kill an Osama bin Laden doppelganger on May Day; allegedly procured PKI where News International can assign journalists or criminals authorized by Crown Agents’ Sisters to track and expose pedophiles, or to entrap and extort them; Wade grew up in Daresbury; she decided she wanted to be a journalist from the age of fourteen; she attended Appleton Hall County Grammar School in Warrington; she worked for French magazine L’architecture d’aujourd’hui in Paris; she returned to Britain to work for Eddy Shah’s Messenger Group; she allegedly infiltrated PKI hides into the management of the Sunday newspaper News of the World where she was hired in 1989 as a secretary before being promoted to feature writer and eventually the paper’s deputy editor; she allegedly procured PKI ‘hides’ to authorize the NOTW’s routine practice of intercepting mobile phone messages of celebrities, politicians and other public figures; allegedly procured PKI ‘hides’ to entrap James Hewitt, a paramour of Princess Diana, by reserving a hotel suite for an ‘interview’ and “kitting it out with secret tape devices in various flowerpots and cupboards”; allegedly procured PKI ‘hides’ for the News of the World when she returned in 2000 as editor; allegedly procured PKI ‘hides’ to launch a NOTW campaign of “naming and shaming” convicted child sex offenders; allegedly procured PKI ‘hides’ to monitor the murder of Sarah Payne; allegedly procured PKI ‘hides’ to incite mob attacks on suspected pedophiles; allegedly procured PKI ‘hides’ to release information on the basis that it is “only right that the public have controlled access” to information on sex offenders; allegedly procured PKI ‘hides’ in January 2003 after she returned to The Sun, replacing her former boss David Yelland, to become its first female editor; allegedly procured PKI ‘hides’ to generate the “Bonkers Bruno Locked Up” story concerning the mental health problems of former heavyweight boxing champion Frank Bruno; allegedly procured PKI ‘hides’ to monitor Women in Journalism where she once served as chairman; allegedly procured PKI ‘hides’ to monitor “Guardian Student Media Awards” where she served as a judge in November 2003; allegedly procured PKI ‘hides’ to monitor tenth annual Police Bravery Awards sponsored by The Sun where she served as a judge in July 2005; allegedly procured PKI ‘hides’ to infiltrate News International management systems after she left The Sun in September 2009 to become chief executive of the newspaper’s parent company; allegedly procured PKI ‘hides’ to authorize NOTW reporter, Clive Goodman, and Glenn Mulcaire, a hired investigator, to intercept the phone messages of members of the royal family; allegedly procured PKI ‘hides’ to authorize payments by her journalists to “… police for information in the past”; allegedly procured PKI ‘hides’ to hack the voicemail of missing schoolgirl Milly Dowler (later found to be murdered) and access or delete messages left by her parents; allegedly procured PKI ‘hides’ to monitor and control leading politicians; allegedly procured PKI ‘hides’ to monitor sex habits (?) of her ‘friends’ Tony and Cherie Blair; allegedly procured PKI ‘hides’ to monitor sex habits (?) of then Prime Minister Gordon Brown, and current Prime Minister David Cameron both of whom attended her 2009 wedding; allegedly procured PKI ‘hides’ to monitor sex habits (?) of Samantha and David Cameron who live near her home in Oxfordshire where they often go horse riding together and have had dinner at each others’ homes; she was engaged to actor Ross Kemp (best known as Grant Mitchell in EastEnders) in 1996, and married him in June 2002 in Las Vegas; she did not take Kemp’s surname and she was arrested on 3 November 2005, following an alleged assault on her husband; she was later released without charge and the police took no further action; she is referred to in Private Eye as “the slapper” (a pejorative word for a woman of loose morals in Britain, and a pun on the act of slapping); the couple had spent the previous evening in the company of the former Cabinet Minister David Blunkett, who had resigned for the second time on that day; she allegedly procured PKI ‘hides’ to monitor citizens through ID cards originally sponsored by Blunkett, who pioneered the UK government’s proposal; she allegedly procured PKI ‘hides’ with Blunkett through Entrust, the Nortel/Ottawa security company which allegedly provided certificate authorities for the 911 attacks and the sabotage of the Deepwater Horizon; allegedly procured PKI ‘hides’ to bug Blunkett who named his budgerigar “Bimbo” to remind him of the secret unlock code for the information on his I.D card; allegedly procured PKI ‘hides’ to monitor and extort the Prince of Wales into support for the global warming scam and the contract killing of deniers on behalf of the NATO Parliamentary Assembly and the Alliance of Small Island States; she repeatedly chose not to attend to give evidence to a cross-party media committee investigating News of the World’s phone-hacking; her refusal to attend resulted in four members of the committee “considering asking the serjeant at arms to issue a warrant forcing Brooks to attend”; allegedly procured PKI ‘hides’ to monitor sex life of James Whittingdale, her Facebook friend al least until the week ending 10/7/2011, and control him as the chairman of the Culture, Media and Sport Committee, during the trial (?) of the Murdoch males; allegedly procured PKI ‘hides’ to extort Whittingdale into warning members of the committee not to compel her to testify due to the risk that their personal lives would be investigated in revenge; allegedly procured PKI ‘hides’ to monitor Whittingdale when he worked on international privatisation at NM Rothschild in 1987 and, in January 1988, when he became Political Secretary to Margaret Thatcher through to the time of his election to Parliament in 1992; allegedly procured PKI ‘hides’ to extort support from Dr Thérèse Coffey, a member of the Culture, Media and Sport Committee in the upcoming show trial of the Murdoch males, who has already complained of a “witch hunt” against Wade on the basis that simply to say she was editor at the time is not enough evidence; allegedly procured PKI ‘hides’ to feed bogus information to Coffey that Wade’s own phone is thought to have been tapped and the problems were not “unique to one news group”; allegedly procured PKI ‘hides’ to extort support from Louise Daphne Mensch, a member of the Culture, Media and Sport Committee, in the upcoming show trial of the Murdoch males; allegedly procured PKI ‘hides’ to extort Mensch into the secret June 2011 marriage with Peter Mensch, 19 years her senior who was co-manager of Def Leppard rock group; she allegedly procured Matrix 5 PKI ‘hides’ to extort Peter Mensch and contemporary media leaders into transforming the radical lesbian (les lesbiennes radicales) cult and‘culture’ associated with Pyromania, France and Quebec of the ‘80s into the ‘first live broadcast mass snuff film in human history’ on 911.]”
65. Rebekah Brooks (née Rebekah Mary Wade; born 27 May 1968) “[Revised June 13, 2012. Matrix 5 aide to allegedly extorted men-in-the-middle, Rupert Murdoch and his two sons; she allegedly worked with Romney’s Bain and Common Purpose partners to develop VideoGuard pay-per-view encryption codes to conceal child pornography and snuff-film trades; she allegedly worked with Common Purpose graduate Adele Blakebrough to archive encrypted snuff films with Clifford Chance clients at Canary Wharf (Citi); she is the Matrix 5 former wife of Ross Kemp, the ex-EastEnders actor who once described her as a ‘homophobic cow’; she is the Matrix 5 associate of allegedly extorted men-in-the-middle alumni of the Bullingdon Club and their relatives, including Mayor of London Boris Johnson’s Middle Templar wife, Marina (see # 66) ; Matrix 5 former boss of NOTW staff who appeared elated when she sacked them and shut down the paper – allegedly creating a decoy to protect the Middle Temple pedophile trade; alleged expert user of PwC’s beTrusted and Entrust public key infrastructure to decoy crime scenes such as those associated with Holly Wells, Jessica Chapman, Maddy McCann and Gareth Williams; alleged expert user of PwC’s beTrusted and Entrust public key infrastructure to divert investigators from Matrix 5 man-in-the-middle attacks and a centuries-old Middle Temple pedophile entrapment trade; allegedly recruited into the Matrix 5 extortion racket in the mid’ 80s in Paris by agents of the late Jeanne Sauve, then-Governor General of Canada and patron of SOS Children’s Villages – an alleged, supranational network of pedophile entrapment and oath-taking centers funded by D2 Banking and HSBC out of Canada Square, Canary Wharf; allegedly set up ‘off-campus’ pedophile entrapment centers for alumni, faculty and students at the Sorbonne in Paris; allegedly procured Sun-Mozilla PKI – public key infrastructure – ‘hides’ for clients of Canary Wharf-based PKI Services, including NATO, United Nations and News International cutouts in the FBI, U.S. Marshals Service, Interpol and the Metropolitan Police to operate dual-use cells as virtual private networks for sabotage, assassination and deception; allegedly set up NATO ‘Skyhackers’ with public key infrastructure used at News International to stage the Matrix 5 ambush of U.S. Navy Seals who threatened to expose Barack Obama’s use of the same technology to kill an Osama bin Laden doppelganger on May Day; allegedly procured PKI where News International can assign journalists or criminals authorized by Crown Agents’ Sisters to track and expose pedophiles, or to entrap and extort them; Wade grew up in Daresbury; she decided she wanted to be a journalist from the age of fourteen; she attended Appleton Hall County Grammar School in Warrington; she worked for French magazine L’architecture d’aujourd’hui in Paris; she returned to Britain to work for Eddy Shah’s Messenger Group; she allegedly infiltrated PKI hides into the management of the Sunday newspaper News of the World where she was hired in 1989 as a secretary before being promoted to feature writer and eventually the paper’s deputy editor; she allegedly procured PKI ‘hides’ to authorize the NOTW’s routine practice of intercepting mobile phone messages of celebrities, politicians and other public figures; allegedly procured PKI ‘hides’ to entrap James Hewitt, a paramour of Princess Diana, by reserving a hotel suite for an ‘interview’ and “kitting it out with secret tape devices in various flowerpots and cupboards”; allegedly procured PKI ‘hides’ for the News of the World when she returned in 2000 as editor; allegedly procured PKI ‘hides’ to launch a NOTW campaign of “naming and shaming” convicted child sex offenders; allegedly procured PKI ‘hides’ to monitor the murder of Sarah Payne; allegedly procured PKI ‘hides’ to incite mob attacks on suspected pedophiles; allegedly procured PKI ‘hides’ to release information on the basis that it is “only right that the public have controlled access” to information on sex offenders; allegedly procured PKI ‘hides’ in January 2003 after she returned to The Sun, replacing her former boss David Yelland, to become its first female editor; allegedly procured PKI ‘hides’ to generate the “Bonkers Bruno Locked Up” story concerning the mental health problems of former heavyweight boxing champion Frank Bruno; allegedly procured PKI ‘hides’ to monitor Women in Journalism where she once served as chairman; allegedly procured PKI ‘hides’ to monitor “Guardian Student Media Awards” where she served as a judge in November 2003; allegedly procured PKI ‘hides’ to monitor tenth annual Police Bravery Awards sponsored by The Sun where she served as a judge in July 2005; allegedly procured PKI ‘hides’ to infiltrate News International management systems after she left The Sun in September 2009 to become chief executive of the newspaper’s parent company; allegedly procured PKI ‘hides’ to authorize NOTW reporter, Clive Goodman, and Glenn Mulcaire, a hired investigator, to intercept the phone messages of members of the royal family; allegedly procured PKI ‘hides’ to authorize payments by her journalists to “… police for information in the past”; allegedly procured PKI ‘hides’ to hack the voicemail of missing schoolgirl Milly Dowler (later found to be murdered) and access or delete messages left by her parents; allegedly procured PKI ‘hides’ to monitor and control leading politicians; allegedly procured PKI ‘hides’ to monitor sex habits (?) of her ‘friends’ Tony and Cherie Blair; allegedly procured PKI ‘hides’ to monitor sex habits (?) of then Prime Minister Gordon Brown, and current Prime Minister David Cameron both of whom attended her 2009 wedding; allegedly procured PKI ‘hides’ to monitor sex habits (?) of Samantha and David Cameron who live near her home in Oxfordshire where they often go horse riding together and have had dinner at each others’ homes; she was engaged to actor Ross Kemp (best known as Grant Mitchell in EastEnders) in 1996, and married him in June 2002 in Las Vegas; she did not take Kemp’s surname and she was arrested on 3 November 2005, following an alleged assault on her husband; she was later released without charge and the police took no further action; she is referred to in Private Eye as “the slapper” (a pejorative word for a woman of loose morals in Britain, and a pun on the act of slapping); the couple had spent the previous evening in the company of the former Cabinet Minister David Blunkett, who had resigned for the second time on that day; she allegedly procured PKI ‘hides’ to monitor citizens through ID cards originally sponsored by Blunkett, who pioneered the UK government’s proposal; she allegedly procured PKI ‘hides’ with Blunkett through Entrust, the Nortel/Ottawa security company which allegedly provided certificate authorities for the 911 attacks and the sabotage of the Deepwater Horizon; allegedly procured PKI ‘hides’ to bug Blunkett who named his budgerigar “Bimbo” to remind him of the secret unlock code for the information on his I.D card; allegedly procured PKI ‘hides’ to monitor and extort the Prince of Wales into support for the global warming scam and the contract killing of deniers on behalf of the NATO Parliamentary Assembly and the Alliance of Small Island States; she repeatedly chose not to attend to give evidence to a cross-party media committee investigating News of the World’s phone-hacking; her refusal to attend resulted in four members of the committee “considering asking the serjeant at arms to issue a warrant forcing Brooks to attend”; allegedly procured PKI ‘hides’ to monitor sex life of James Whittingdale, her Facebook friend al least until the week ending 10/7/2011, and control him as the chairman of the Culture, Media and Sport Committee, during the trial (?) of the Murdoch males; allegedly procured PKI ‘hides’ to extort Whittingdale into warning members of the committee not to compel her to testify due to the risk that their personal lives would be investigated in revenge; allegedly procured PKI ‘hides’ to monitor Whittingdale when he worked on international privatisation at NM Rothschild in 1987 and, in January 1988, when he became Political Secretary to Margaret Thatcher through to the time of his election to Parliament in 1992; allegedly procured PKI ‘hides’ to extort support from Dr Thérèse Coffey, a member of the Culture, Media and Sport Committee in the upcoming show trial of the Murdoch males, who has already complained of a “witch hunt” against Wade on the basis that simply to say she was editor at the time is not enough evidence; allegedly procured PKI ‘hides’ to feed bogus information to Coffey that Wade’s own phone is thought to have been tapped and the problems were not “unique to one news group”; allegedly procured PKI ‘hides’ to extort support from Louise Daphne Mensch, a member of the Culture, Media and Sport Committee, in the upcoming show trial of the Murdoch males; allegedly procured PKI ‘hides’ to extort Mensch into the secret June 2011 marriage with Peter Mensch, 19 years her senior who was co-manager of Def Leppard rock group; she allegedly procured Matrix 5 PKI ‘hides’ to extort Peter Mensch and contemporary media leaders into transforming the radical lesbian (les lesbiennes radicales) cult and‘culture’ associated with Pyromania, France and Quebec of the ‘80s into the ‘first live broadcast mass snuff film in human history’ on 911.]”
 66. Marina Johnson (nee Wheeler) “[Revised August 3, 2011. Matrix 5 principal and second wife of allegedly extorted man-in-the-middle Mayor of London, Boris Johnson; she was called to the Middle Temple Bar in 1987 and now practices from chambers in London at One Crown Office Row; she allegedly worked with Kristine Marcy, Miriam Clegg and insiders of the U.K. Home Office, the MOD, the Foreign and Commonwealth Office on the recruitment of saboteurs, assassins and double agents to support murder-for-hire service; allegedly conspired with Kristine Marcy, Miriam Clegg and insiders of the U.K. Home Office, the MOD, the Foreign and Commonwealth Office to develop a post-WWII Operation Paperclip and overthrow the United States government through traitors inside the gates; allegedly conspired with Middle Temple associates to secure an electronic passport for Barry Soetoro which allowed him to conceal his status as a citizen of the United Kingdom and Colonies and run as Barack Obama during the U.S. Presidential election campaign of 2008; she and her fellow Crown Office extortionists have allegedly invented the crime of ecocide; they have equated a failure or refusal to reduce greenhouse gas emissions – fraudulently claimed as a principal cause of catastrophic climate change – to the mens rea of a homicide; her fellow Middle Temple Crown Office extortionists are promoting the use of odious debt and predatory credit-default swaps to legitimize the execution of borrower-violators as on 911; her fellow Middle Temple Crown Office extortionists are allegedly using blip.tv to transmit digital images of torture, bombings and murder to secure the obedience of Matrix 5 agents and the silence of prospective whistleblowers; she is the sister-in-law of allegedly-extorted man-in-the-middle partner at PricewaterhouseCoopers, Leo Johnson, the snuff (?) film-maker who plans to replace government with PwC Ecocide PKI regulators who claim rights such as, “I will sabotage your plant if you are killing my fish, I will remove insurance, I will picket your product”; she allegedly forced Leo Johnson to issue PwC PKI security certificates and root authority for Stuxnet attack on Air France Flight 447 on June 1, 2009; she allegedly forced Leo Johnson to issue PwC PKI security certificates to an ‘Andrew Berwick London’ account at D2 Banking allowing a virtual identity to finance the Ecocide / Unabomb attack on Norway’s oil and energy ministries; she is the sister-in-law of allegedly extorted woman-in-the-middle Rachel Johnson who was educated at the European School in Brussels and read Classics (Literae Humaniores) at New College, Oxford in the mid-‘80s; Marina’s husband Boris Johnson and sister-in-law Rachel Johnson have sufficient fluency in written Latin to qualify as suspect adopters of phrases used by the PKI identity, Andrew Berwick, “Pauperes commilitones Christi Templique Solomonici” and “De Laude Novae Militiae”; she allegedly used Rachel Johnson’s position in the BBC in 1994 and as a freelance columnist in Washington DC to help PwC, RSA, Verisign and Entrust set up PKI Ecocide accounts for Matrix 5 insiders and prepare the 911 attacks on America; she allegedly forced Boris Johnson to employ Andrew Gordon, Head of Investigations in the PwC Forensic Services group, in a Forensic Audit Panel to whitewash financial and PKI identity frauds by insiders of the London Development Agency; she is the sister-in-law of allegedly extorted man-in-the-middle Jo Johnson, former editor of the Lex Column on the Financial Times and MP for Orpington who allegedly uses PwC PKI certificates to manipulate the U.K. public accounts committee with its chairman and the former PwC consultant Margaret Hodge MP; she has forensic skills of a Middle Temple barrister to deal with bogus discrimination claims but lacks basic skills in spoliation CSI to properly conceal the PKI identities behind the bombings in Oslo and the shootings in Utoya; she is half English and half Indian; she is the daughter of BBC correspondent Sir Charles Wheeler and his second wife Dip Singh; she was educated at the European School of Brussels; in the early 1980s, she studied at the University of Cambridge where she wrote for the student magazine; after Cambridge, she returned to Brussels and worked there for four years; at the European School, she became a friend of Boris Johnson, the future Mayor of London; her sister is Shirin Wheeler, now the BBC’s Brussels correspondent; she specialises in mental health matters and discrimination claims; January 2004 she was appointed to the B-Panel of Junior Counsel to the Crown; In 2009, she joined the Bar Disciplinary Tribunal as a barrister member; works in discrimination law while recognizing more than 60 per cent of claims are bogus; she married her childhood friend, Boris Johnson in 1993 after they met again in Brussels, where he was covering the European Parliament for The Daily Telegraph; while promoting one-child policy for the peasants, they have four children, Lara Lettice, Milo Arthur, Cassia Peaches and Theodore Apollo; he worked for a short while for L.E.K. which now advises the UK government on the 100% carbon neutral and has developed a tested methodology for carbon; she is trying to engineer her husband to take over from David Cameron as prime minister; she allegedly forced Boris to set up the resignation of Paul Stephenson, Metropolitan Police Commissioner because his force had hired someone who used to work for the News of the World, when David Cameron, who had hired Andy Coulson, was still in his job; she appears to have set up a phone hack on her husband in re the story of the psychopathic Darius Guppy needing some addresses to break a rib or two and intimidate the media; she allegedly had him force Sir Ian Blair out of Met; she allegedly had him force resignation of Sir Paul Stephenson by exploiting the crossed wires of PKI accountability that connect the Metropolitan Police Commissioner both to him and to the Home Office; she allegedly had him force resignation of John Yates, Met’s assistant commissioner using PKI inside information in re Yates’s relationship with Neil Wallis, the former deputy editor of the News of the World, known as “Wolfman”, who had been hired by the Met as a locum spin-doctor; she allegedly had him sabotage Met’s counter-terrorism operations in the year before the Olympics by replacing Yates with Cressida Dick, the Gold Room commander and PwC PKI user who allegedly authorized the killing of Jean Charles de Menezes on 8/7; she frames her husband as a harmless bombastic buffoon who talks of Kosovo-style social cleansing; she is the daughter-in-law of the allegedly-extorted man-in-the-middle Stanley Johnson, an Ecocide sponsor, who worked at the European Commission, served as a Tory MEP from 1979 to 1984, and stood as Tory parliamentary candidate for Teignbridge in Devon; she is the daughter-in-law of the allegedly-extorted woman-in-the-middle Charlotte Wahl whose father Sir James Fawcett was a barrister and president of the European Commission of Human Rights and whose ancestry includes the early feminist and suffragette Millicent Garrett Fawcett. Abel Danger has concluded that PwC’s Ecocidal PKI lesbians and Boris Johnson’s Femme Comp wife Marina, know how to operate a Matrix 5 MitM propaganda attack with actors and patents but not how to defend against one and they view the OODA loop as a redundant form of heterosexual contraception.]”
66. Marina Johnson (nee Wheeler) “[Revised August 3, 2011. Matrix 5 principal and second wife of allegedly extorted man-in-the-middle Mayor of London, Boris Johnson; she was called to the Middle Temple Bar in 1987 and now practices from chambers in London at One Crown Office Row; she allegedly worked with Kristine Marcy, Miriam Clegg and insiders of the U.K. Home Office, the MOD, the Foreign and Commonwealth Office on the recruitment of saboteurs, assassins and double agents to support murder-for-hire service; allegedly conspired with Kristine Marcy, Miriam Clegg and insiders of the U.K. Home Office, the MOD, the Foreign and Commonwealth Office to develop a post-WWII Operation Paperclip and overthrow the United States government through traitors inside the gates; allegedly conspired with Middle Temple associates to secure an electronic passport for Barry Soetoro which allowed him to conceal his status as a citizen of the United Kingdom and Colonies and run as Barack Obama during the U.S. Presidential election campaign of 2008; she and her fellow Crown Office extortionists have allegedly invented the crime of ecocide; they have equated a failure or refusal to reduce greenhouse gas emissions – fraudulently claimed as a principal cause of catastrophic climate change – to the mens rea of a homicide; her fellow Middle Temple Crown Office extortionists are promoting the use of odious debt and predatory credit-default swaps to legitimize the execution of borrower-violators as on 911; her fellow Middle Temple Crown Office extortionists are allegedly using blip.tv to transmit digital images of torture, bombings and murder to secure the obedience of Matrix 5 agents and the silence of prospective whistleblowers; she is the sister-in-law of allegedly-extorted man-in-the-middle partner at PricewaterhouseCoopers, Leo Johnson, the snuff (?) film-maker who plans to replace government with PwC Ecocide PKI regulators who claim rights such as, “I will sabotage your plant if you are killing my fish, I will remove insurance, I will picket your product”; she allegedly forced Leo Johnson to issue PwC PKI security certificates and root authority for Stuxnet attack on Air France Flight 447 on June 1, 2009; she allegedly forced Leo Johnson to issue PwC PKI security certificates to an ‘Andrew Berwick London’ account at D2 Banking allowing a virtual identity to finance the Ecocide / Unabomb attack on Norway’s oil and energy ministries; she is the sister-in-law of allegedly extorted woman-in-the-middle Rachel Johnson who was educated at the European School in Brussels and read Classics (Literae Humaniores) at New College, Oxford in the mid-‘80s; Marina’s husband Boris Johnson and sister-in-law Rachel Johnson have sufficient fluency in written Latin to qualify as suspect adopters of phrases used by the PKI identity, Andrew Berwick, “Pauperes commilitones Christi Templique Solomonici” and “De Laude Novae Militiae”; she allegedly used Rachel Johnson’s position in the BBC in 1994 and as a freelance columnist in Washington DC to help PwC, RSA, Verisign and Entrust set up PKI Ecocide accounts for Matrix 5 insiders and prepare the 911 attacks on America; she allegedly forced Boris Johnson to employ Andrew Gordon, Head of Investigations in the PwC Forensic Services group, in a Forensic Audit Panel to whitewash financial and PKI identity frauds by insiders of the London Development Agency; she is the sister-in-law of allegedly extorted man-in-the-middle Jo Johnson, former editor of the Lex Column on the Financial Times and MP for Orpington who allegedly uses PwC PKI certificates to manipulate the U.K. public accounts committee with its chairman and the former PwC consultant Margaret Hodge MP; she has forensic skills of a Middle Temple barrister to deal with bogus discrimination claims but lacks basic skills in spoliation CSI to properly conceal the PKI identities behind the bombings in Oslo and the shootings in Utoya; she is half English and half Indian; she is the daughter of BBC correspondent Sir Charles Wheeler and his second wife Dip Singh; she was educated at the European School of Brussels; in the early 1980s, she studied at the University of Cambridge where she wrote for the student magazine; after Cambridge, she returned to Brussels and worked there for four years; at the European School, she became a friend of Boris Johnson, the future Mayor of London; her sister is Shirin Wheeler, now the BBC’s Brussels correspondent; she specialises in mental health matters and discrimination claims; January 2004 she was appointed to the B-Panel of Junior Counsel to the Crown; In 2009, she joined the Bar Disciplinary Tribunal as a barrister member; works in discrimination law while recognizing more than 60 per cent of claims are bogus; she married her childhood friend, Boris Johnson in 1993 after they met again in Brussels, where he was covering the European Parliament for The Daily Telegraph; while promoting one-child policy for the peasants, they have four children, Lara Lettice, Milo Arthur, Cassia Peaches and Theodore Apollo; he worked for a short while for L.E.K. which now advises the UK government on the 100% carbon neutral and has developed a tested methodology for carbon; she is trying to engineer her husband to take over from David Cameron as prime minister; she allegedly forced Boris to set up the resignation of Paul Stephenson, Metropolitan Police Commissioner because his force had hired someone who used to work for the News of the World, when David Cameron, who had hired Andy Coulson, was still in his job; she appears to have set up a phone hack on her husband in re the story of the psychopathic Darius Guppy needing some addresses to break a rib or two and intimidate the media; she allegedly had him force Sir Ian Blair out of Met; she allegedly had him force resignation of Sir Paul Stephenson by exploiting the crossed wires of PKI accountability that connect the Metropolitan Police Commissioner both to him and to the Home Office; she allegedly had him force resignation of John Yates, Met’s assistant commissioner using PKI inside information in re Yates’s relationship with Neil Wallis, the former deputy editor of the News of the World, known as “Wolfman”, who had been hired by the Met as a locum spin-doctor; she allegedly had him sabotage Met’s counter-terrorism operations in the year before the Olympics by replacing Yates with Cressida Dick, the Gold Room commander and PwC PKI user who allegedly authorized the killing of Jean Charles de Menezes on 8/7; she frames her husband as a harmless bombastic buffoon who talks of Kosovo-style social cleansing; she is the daughter-in-law of the allegedly-extorted man-in-the-middle Stanley Johnson, an Ecocide sponsor, who worked at the European Commission, served as a Tory MEP from 1979 to 1984, and stood as Tory parliamentary candidate for Teignbridge in Devon; she is the daughter-in-law of the allegedly-extorted woman-in-the-middle Charlotte Wahl whose father Sir James Fawcett was a barrister and president of the European Commission of Human Rights and whose ancestry includes the early feminist and suffragette Millicent Garrett Fawcett. Abel Danger has concluded that PwC’s Ecocidal PKI lesbians and Boris Johnson’s Femme Comp wife Marina, know how to operate a Matrix 5 MitM propaganda attack with actors and patents but not how to defend against one and they view the OODA loop as a redundant form of heterosexual contraception.]”
 67. Kathy Robertson (nee Lette) “[Matrix 5 principal and former wife of allegedly extorted Kim Williams, now Chief executive officer of Foxtel and former CEO of the Australian Film Commission with offices in Brisbane, Melbourne, Canberra and Sydney; allegedly extorted Williams into assisting Assange’s Mad Cow mother in production of pedophile content for Film Australia– previously known as the Commonwealth Film Unit; allegedly hired Assange in 1987 to hack PKI under the name “Mendax” (derived from a phrase of Horace “splendide mendax”, or “nobly untruthful”) within a group named International Subversives which altered logs to cover their tracks; infiltrated Australian Federal Police to sabotage “Operation Weather” investigation; allegedly had Williams pay Assange in September 1991 to hack Melbourne master terminal of Nortel, the Canadian telecommunications company, which was then developing Entrust PKI; allegedly had Williams sabotage Australian Federal Police’s tap on Assanges’ phoneline and spoliate evidence collected from the raid on Assanges’ Melbourne home in 1991; allegedly had Williams pay Assange to hack computers belonging to an Australian university and the USAF 7th Command Group in the Pentagon and other organisations, via FC-Ku modem; allegedly had Williams pay corrupt Australian [Middle Templar?] court officials to stage 31 counts of hacking and related crimes against Assange where victim Nortel said his incursions cost them more than $100,000; allegedly had Williams tell Assange to plead guilty to 25 charges of hacking and have him released on bond for good conduct after being fined A$2,100; allegedly had Williams corrupt the judge who dismissed Assange’s breach of Australia’s national security in history as “there is just no evidence that there was anything other than sort of intelligent inquisitiveness and the pleasure of being able to—what’s the expression—surf through these various computers” and state that Assange would have gone to jail for up to 10 years if he had not had such a disrupted [abused?] childhood; allegedly had Williams pay Assange in 1993 to hack the Victoria Police Child Exploitation Unit and identify targets for pedophile entrapment and extortion; allegedly had Williams pay Assange and his Mad Cow mother to form Parent Inquiry Into Child Protection with a “central databank” for legal records [snuff films?]; allegedly had Williams procure an Assange database which gave pedophiles direct access to the children’s court and targeted children who could be disappeared; allegedly had Williams pay Assange to start one of the first public internet service providers in Australia, Suburbia Public Access Network in 1993; allegedly had Williams pay Assange to move to Melbourne as a programmer and a developer of free software over FC-Ku links to Pentagon; allegedly had Williams pay Assange in 1995 to write Strobe, the first free and open source port scanner and contribute patches to the PostgreSQL project in 1996; allegedly had Williams pay Assange to co-author ‘Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier (1997)’ and expand the matrix of International Subversives; allegedly had Williams pay Assange through 1997 to develop Rubberhose deniable encryption system as a software package for Linux to provide Mad Cows with plausible deniability against rubber-hose cryptanalysis; allegedly had Williams pay Assange to set up an Amazon / Verisign PKI service for IMDb snuff-film database linked to D2 Banking in HSBC headquarters at Canary Wharf; allegedly had Williams pay Assange to develop other free software including Usenet caching software NNTPCache and Surfraw, a command-line interface for web-based search engines; allegedly had Williams pay Assange to work with FCI – Femme Comp Inc – a Mad Cow-owned small business which provides Command and Control (C2) support for man-in-the-middle contract hits with Pentagon insiders having plausible denial at FC-Ku crime scenes over more than 30 years; she allegedly had Williams pay Assange to hack Foxtel, Australia’s largest subscription satellite TV service, to inject real/simulated snuff-film images into BBC World, CNN, Discovery and History Channel; she allegedly had Williams pay Assange to build Foxtel compatibility with Ku-band marine systems – Kurtz-under band is primarily used for satellite communications, particularly for editing and broadcasting satellite television with the first commercial television network to extensively utilize Ku Band being NBC back in 1983; she allegedly had Williams pay Assange to build PKI/Onion Router encryption to move snuff film digital images through Telstra Ku band networks for video-publishing website of pornographic and snuff-film videos; allegedly had Williams pay Assange to attend the University of Melbourne from 2003-2006 to monitor fellow students’ research for Pentagon’s DARPA; allegedly had Williams pay Assange to hack U.S. Navy developments of Onion Router patented devices to conceal alleged pedophile snuff-film trade for Middle Templars; allegedly had Williams pay Assange to hack Internet Movie Database operated with Verisign PKI to conceal pedophile snuff films; Kathy is coauthor with her friend Gabrielle Carey of Puberty Blues where she explains how underage girls can be used to set sex traps for a hypothetical “Greenhill gang” of surfers; she became a newspaper columnist and sitcom writer; she wrote Girls’ Night Out in 1988 and Foetal Attraction and Mad Cows in 1996; she wrote Dead Sexy; she wrote ‘ How to Kill your Husband (and other handy household hints)’ in 2007; she wrote ‘To Love, Honour & Betray (Till Divorce Us Do Part)’ in 2008 as a serial sneer at the institution of marriage; she edited an anthology by prominent women writers of erotic short-stories, In Bed with… (2009) where each ‘Mad Cow’ friend published under a pseudonym; she despises English heterosexual men and women and accuses them of being condescending and unfriendly; she is married to the allegedly-extorted man-in-the-middle Geoffrey Robertson, a fellow Australian expatriate, whom she met in 1988 during the filming of a Hypothetical episode for ABC Television and married in 1990; her husband Robertson was called to Middle Temple bar in 1973; her husband Robertson was a Rhodes Scholar in 1979 – two years after Bill Clinton; her husband Robertson has dual Australian and British citizenship; her husband Robertson is the founder and head of Doughty Street Chambers; her husband Robertson is Master of the Bench at the Middle Temple; her husband Robertson was defence counsel in the criminal trials of Oz, Gay News, the ABC Trial, the Brighton bombing and Matrix Churchill – an alleged cut out case for Middle Temple contracts with Crown Agents and Saddam Hussein to kill Iranians; she allegedly has Robertson appearing in cases before the European Court of Human Rights and in other courts across the world; she allegedly had Robertson author a defence of Michael X in Trinidad; she allegedly has had Robertson fronting for phony human rights missions in Mozambique, Venda, Czechoslovakia, Malawi, Vietnam and South Africa where HSBC is allegedly financing the development of SOS Children’s Villages for the Middle Templar pedophile trade; she allegedly had Robertson sitting as an appeal judge at the UN Special Court for Sierra Leone; she allegedly has Robertson defending the head of Wikileaks, Julian Assange, in extradition proceedings in the UK; she allegedly has Robertson using Sky News Assange’s release of secret diplomatic cables and other materials; she allegedly has Robertson setting up a cutout case for Assange to fight extradition to Sweden, where he is accused of sex crimes with a couple of ‘Mad Consensual Cow’ lesbians for failing to use a condom; she allegedly has Robertson claiming Assange could face execution in the US if he is extradited from Sweden where the accuser-lesbians hang their hats; she allegedly has Robertson claiming that Assange’s possible extradition to Sweden could breach Article 3 of the European Convention on Human Rights (ECHR), which bans torture but condones the Middle Temple pedophile trade; she allegedly has Robertson spinning Matrix 5 propaganda re Assange through ” .. newspaper partners around the world, big and small newspapers and some human rights organisations”; she allegedly had Robertson get Mr Assange freed on £240,000 bail by a High Court judge after spending nine days in Wandsworth Prison; she allegedly had Robertson place Assange with a minder, Vaughan Smith, who is the Frontline Club founder in Paddington, west London, with a manor home on the Norfolk-Suffolk border; she allegedly had Robertson speak at Marxism 2008, an annual festival hosted by the Socialist Worker’s Party; she allegedly had Robertson made a Bencher of the Middle Temple in 1997; she allegedly had Robertson serve as counsel in 1990 to the Royal Commission’s phony investigations into the trafficking of arms and mercenaries to the Columbian drugs cartels; she allegedly has Robertson, as founder of Doughty Street Chambers, defending cases involving homicide, including the killing of children by their parents; she allegedly has Robertson defending cases of serious and sexual violence involving the evidence of vulnerable witnesses, and delicate cultural issues; she allegedly had Robertson help to draft the child rescue declaration for Kate and Gerry McCann in re the abduction of Madeleine McCann; she allegedly had Robertson represent a special needs teacher charged with multiple counts of cruelty to a severely disabled 10 year old child; she allegedly had Robertson defend against child rape charges (involved cross-examining two 8 year old girls) and achieved complete acquittal of the defendant; she allegedly had Robertson defend 29 environmental protestors who raised climate change defence of duress and prevention of crime; she allegedly had Robertson defend people trafficking and rape allegation; she allegedly had Robertson defend a public school housemaster charged with indecent assault on pupils in his care; she allegedly had Robertson defend a people smuggling and rape case; she allegedly had Robertson defend a conspiracy to murder and cruelty to a child in a “Witchcraft” case; she allegedly had Robertson defend a case re £18 million Heathrow bullion robbery; she allegedly had Robertson defend a CCRC referral, rape and indecent assault of children of family; she allegedly had Robertson defend a £12 million conspiracy to defraud with money laundering; she allegedly had Robertson defend a baby murder, causation and “Cannings” defence case; she allegedly had Robertson defend a child cruelty and witchcraft case; she allegedly had Robertson defend a shaken baby murder, causation case; she allegedly had Robertson defend a mobile phone VAT carousel fraud; she allegedly had Robertson defend a multi-handed conspiracy to commit violent disorder cf. the present PwC, PKI and Blackberry-staged riots in London; she allegedly had Robertson defend child neglect case arising from SIDS; she allegedly had Robertson defend an institutional abuse case with multi party action re physical and sexual abuse of boys in children’s homes during the 1970s and 80s; she allegedly had Robertson defend HSBC bank employee charged with defrauding the bank of £11 million; she allegedly had Robertson defend a sexual abuse case in which the defendant was accused of repeatedly abusing a young girl over a number of years and raping a second female who had a significant mental impairment; she allegedly had Robertson defend solicitation to murder of four senior members of the Egyptian Government / Parliament where undercover police officers posed as former SAS contract killers [or the other way round?]; she allegedly had Robertson defend 20 Climate Change protesters during their trial for conspiracy to occupy and shutdown one of the largest coal fired power stations in Britain; she allegedly had Robertson defend 6 climate change activists in the second Ratcliffe On Soar trial submitting arguments on abuse and disclosure leading to the collapse of the prosecution; she allegedly had Robertson work with non-governmental organisations on promotion of lesbian rights; she allegedly had Robertson appear in phony inquests in re deaths of Jean Charles de Menezes, Mikey Powell, Diana, Princess of Wales/Dodi Al Fayed, Harry Stanley and Ruddock and others (the second New Cross Fire inquest); she allegedly had Robertson represent families in several so-called “suicide-by-cop” cases; she allegedly had Robertson represent bereaved families and survivors of the 7th July 2005 bombings; she allegedly had Robertson work with a team of trustees in a UK and Zambia-based charity to move orphans and vulnerable children through the hands of predators in the HIV/AIDS community; she allegedly had Robertson work as a legal adviser to Presiding Judge Patrick Robinson during the phony trial of former Head of State Slobodan Milosevic at the UN International Criminal Tribunal for the former Yugoslavia; she allegedly had Robertson infiltrate Mad Cow agents, equipped with FC-Ku PKI, into Sullivan & Cromwell LLP’s New York office for phony criminal probe into Enron and Arthur Andersen; she allegedly has told Robertson to get Barack Obama made an Honourary Bencher of the Middle Temple like David Cameron and John Major; she allegedly had Robertson work with Sheila Morag Clark Cameron – called to Middle Temple bar in 1957 – and Julian Assange on the transfer of the contents of the Cardiff Internet Movie Database at Cardiff University in the UK into the Internet Movie Database (IMDb) launched on October 17, 1990; she allegedly had Robertson, Cameron and Assange force the sale of IMDb in 1998 to Amazon.com a subsidiary of Amazon where today it allegedly supports a PKI FC-Ku snuff film service, including backhauling, editing, archiving and copyright functions offered by Middle Templars to their Mad Cow clients; she allegedly had Robertson, Assange and Vaughan Smith set up the FC-Ku public key infrastructure required for the Navy Seal mission which led to the snuff-film death of an Osama bin Laden doppelganger on May 1st 2011; she allegedly had Robertson, Assange and Vaughan Smith set up the FC-Ku public key infrastructure required for the subsequent mission with a National Guard Chinook helicopter which led to the snuff film deaths on August 6 of 22 Navy Seals who might otherwise have exposed the Obama Administration fraud in re the claim to have killed Osama bin Laden on May Day. Contact e-mails j.rollinson@doughtystreet.co.uk; g.robertson@doughtystreet.co.uk]”
67. Kathy Robertson (nee Lette) “[Matrix 5 principal and former wife of allegedly extorted Kim Williams, now Chief executive officer of Foxtel and former CEO of the Australian Film Commission with offices in Brisbane, Melbourne, Canberra and Sydney; allegedly extorted Williams into assisting Assange’s Mad Cow mother in production of pedophile content for Film Australia– previously known as the Commonwealth Film Unit; allegedly hired Assange in 1987 to hack PKI under the name “Mendax” (derived from a phrase of Horace “splendide mendax”, or “nobly untruthful”) within a group named International Subversives which altered logs to cover their tracks; infiltrated Australian Federal Police to sabotage “Operation Weather” investigation; allegedly had Williams pay Assange in September 1991 to hack Melbourne master terminal of Nortel, the Canadian telecommunications company, which was then developing Entrust PKI; allegedly had Williams sabotage Australian Federal Police’s tap on Assanges’ phoneline and spoliate evidence collected from the raid on Assanges’ Melbourne home in 1991; allegedly had Williams pay Assange to hack computers belonging to an Australian university and the USAF 7th Command Group in the Pentagon and other organisations, via FC-Ku modem; allegedly had Williams pay corrupt Australian [Middle Templar?] court officials to stage 31 counts of hacking and related crimes against Assange where victim Nortel said his incursions cost them more than $100,000; allegedly had Williams tell Assange to plead guilty to 25 charges of hacking and have him released on bond for good conduct after being fined A$2,100; allegedly had Williams corrupt the judge who dismissed Assange’s breach of Australia’s national security in history as “there is just no evidence that there was anything other than sort of intelligent inquisitiveness and the pleasure of being able to—what’s the expression—surf through these various computers” and state that Assange would have gone to jail for up to 10 years if he had not had such a disrupted [abused?] childhood; allegedly had Williams pay Assange in 1993 to hack the Victoria Police Child Exploitation Unit and identify targets for pedophile entrapment and extortion; allegedly had Williams pay Assange and his Mad Cow mother to form Parent Inquiry Into Child Protection with a “central databank” for legal records [snuff films?]; allegedly had Williams procure an Assange database which gave pedophiles direct access to the children’s court and targeted children who could be disappeared; allegedly had Williams pay Assange to start one of the first public internet service providers in Australia, Suburbia Public Access Network in 1993; allegedly had Williams pay Assange to move to Melbourne as a programmer and a developer of free software over FC-Ku links to Pentagon; allegedly had Williams pay Assange in 1995 to write Strobe, the first free and open source port scanner and contribute patches to the PostgreSQL project in 1996; allegedly had Williams pay Assange to co-author ‘Underground: Tales of Hacking, Madness and Obsession on the Electronic Frontier (1997)’ and expand the matrix of International Subversives; allegedly had Williams pay Assange through 1997 to develop Rubberhose deniable encryption system as a software package for Linux to provide Mad Cows with plausible deniability against rubber-hose cryptanalysis; allegedly had Williams pay Assange to set up an Amazon / Verisign PKI service for IMDb snuff-film database linked to D2 Banking in HSBC headquarters at Canary Wharf; allegedly had Williams pay Assange to develop other free software including Usenet caching software NNTPCache and Surfraw, a command-line interface for web-based search engines; allegedly had Williams pay Assange to work with FCI – Femme Comp Inc – a Mad Cow-owned small business which provides Command and Control (C2) support for man-in-the-middle contract hits with Pentagon insiders having plausible denial at FC-Ku crime scenes over more than 30 years; she allegedly had Williams pay Assange to hack Foxtel, Australia’s largest subscription satellite TV service, to inject real/simulated snuff-film images into BBC World, CNN, Discovery and History Channel; she allegedly had Williams pay Assange to build Foxtel compatibility with Ku-band marine systems – Kurtz-under band is primarily used for satellite communications, particularly for editing and broadcasting satellite television with the first commercial television network to extensively utilize Ku Band being NBC back in 1983; she allegedly had Williams pay Assange to build PKI/Onion Router encryption to move snuff film digital images through Telstra Ku band networks for video-publishing website of pornographic and snuff-film videos; allegedly had Williams pay Assange to attend the University of Melbourne from 2003-2006 to monitor fellow students’ research for Pentagon’s DARPA; allegedly had Williams pay Assange to hack U.S. Navy developments of Onion Router patented devices to conceal alleged pedophile snuff-film trade for Middle Templars; allegedly had Williams pay Assange to hack Internet Movie Database operated with Verisign PKI to conceal pedophile snuff films; Kathy is coauthor with her friend Gabrielle Carey of Puberty Blues where she explains how underage girls can be used to set sex traps for a hypothetical “Greenhill gang” of surfers; she became a newspaper columnist and sitcom writer; she wrote Girls’ Night Out in 1988 and Foetal Attraction and Mad Cows in 1996; she wrote Dead Sexy; she wrote ‘ How to Kill your Husband (and other handy household hints)’ in 2007; she wrote ‘To Love, Honour & Betray (Till Divorce Us Do Part)’ in 2008 as a serial sneer at the institution of marriage; she edited an anthology by prominent women writers of erotic short-stories, In Bed with… (2009) where each ‘Mad Cow’ friend published under a pseudonym; she despises English heterosexual men and women and accuses them of being condescending and unfriendly; she is married to the allegedly-extorted man-in-the-middle Geoffrey Robertson, a fellow Australian expatriate, whom she met in 1988 during the filming of a Hypothetical episode for ABC Television and married in 1990; her husband Robertson was called to Middle Temple bar in 1973; her husband Robertson was a Rhodes Scholar in 1979 – two years after Bill Clinton; her husband Robertson has dual Australian and British citizenship; her husband Robertson is the founder and head of Doughty Street Chambers; her husband Robertson is Master of the Bench at the Middle Temple; her husband Robertson was defence counsel in the criminal trials of Oz, Gay News, the ABC Trial, the Brighton bombing and Matrix Churchill – an alleged cut out case for Middle Temple contracts with Crown Agents and Saddam Hussein to kill Iranians; she allegedly has Robertson appearing in cases before the European Court of Human Rights and in other courts across the world; she allegedly had Robertson author a defence of Michael X in Trinidad; she allegedly has had Robertson fronting for phony human rights missions in Mozambique, Venda, Czechoslovakia, Malawi, Vietnam and South Africa where HSBC is allegedly financing the development of SOS Children’s Villages for the Middle Templar pedophile trade; she allegedly had Robertson sitting as an appeal judge at the UN Special Court for Sierra Leone; she allegedly has Robertson defending the head of Wikileaks, Julian Assange, in extradition proceedings in the UK; she allegedly has Robertson using Sky News Assange’s release of secret diplomatic cables and other materials; she allegedly has Robertson setting up a cutout case for Assange to fight extradition to Sweden, where he is accused of sex crimes with a couple of ‘Mad Consensual Cow’ lesbians for failing to use a condom; she allegedly has Robertson claiming Assange could face execution in the US if he is extradited from Sweden where the accuser-lesbians hang their hats; she allegedly has Robertson claiming that Assange’s possible extradition to Sweden could breach Article 3 of the European Convention on Human Rights (ECHR), which bans torture but condones the Middle Temple pedophile trade; she allegedly has Robertson spinning Matrix 5 propaganda re Assange through ” .. newspaper partners around the world, big and small newspapers and some human rights organisations”; she allegedly had Robertson get Mr Assange freed on £240,000 bail by a High Court judge after spending nine days in Wandsworth Prison; she allegedly had Robertson place Assange with a minder, Vaughan Smith, who is the Frontline Club founder in Paddington, west London, with a manor home on the Norfolk-Suffolk border; she allegedly had Robertson speak at Marxism 2008, an annual festival hosted by the Socialist Worker’s Party; she allegedly had Robertson made a Bencher of the Middle Temple in 1997; she allegedly had Robertson serve as counsel in 1990 to the Royal Commission’s phony investigations into the trafficking of arms and mercenaries to the Columbian drugs cartels; she allegedly has Robertson, as founder of Doughty Street Chambers, defending cases involving homicide, including the killing of children by their parents; she allegedly has Robertson defending cases of serious and sexual violence involving the evidence of vulnerable witnesses, and delicate cultural issues; she allegedly had Robertson help to draft the child rescue declaration for Kate and Gerry McCann in re the abduction of Madeleine McCann; she allegedly had Robertson represent a special needs teacher charged with multiple counts of cruelty to a severely disabled 10 year old child; she allegedly had Robertson defend against child rape charges (involved cross-examining two 8 year old girls) and achieved complete acquittal of the defendant; she allegedly had Robertson defend 29 environmental protestors who raised climate change defence of duress and prevention of crime; she allegedly had Robertson defend people trafficking and rape allegation; she allegedly had Robertson defend a public school housemaster charged with indecent assault on pupils in his care; she allegedly had Robertson defend a people smuggling and rape case; she allegedly had Robertson defend a conspiracy to murder and cruelty to a child in a “Witchcraft” case; she allegedly had Robertson defend a case re £18 million Heathrow bullion robbery; she allegedly had Robertson defend a CCRC referral, rape and indecent assault of children of family; she allegedly had Robertson defend a £12 million conspiracy to defraud with money laundering; she allegedly had Robertson defend a baby murder, causation and “Cannings” defence case; she allegedly had Robertson defend a child cruelty and witchcraft case; she allegedly had Robertson defend a shaken baby murder, causation case; she allegedly had Robertson defend a mobile phone VAT carousel fraud; she allegedly had Robertson defend a multi-handed conspiracy to commit violent disorder cf. the present PwC, PKI and Blackberry-staged riots in London; she allegedly had Robertson defend child neglect case arising from SIDS; she allegedly had Robertson defend an institutional abuse case with multi party action re physical and sexual abuse of boys in children’s homes during the 1970s and 80s; she allegedly had Robertson defend HSBC bank employee charged with defrauding the bank of £11 million; she allegedly had Robertson defend a sexual abuse case in which the defendant was accused of repeatedly abusing a young girl over a number of years and raping a second female who had a significant mental impairment; she allegedly had Robertson defend solicitation to murder of four senior members of the Egyptian Government / Parliament where undercover police officers posed as former SAS contract killers [or the other way round?]; she allegedly had Robertson defend 20 Climate Change protesters during their trial for conspiracy to occupy and shutdown one of the largest coal fired power stations in Britain; she allegedly had Robertson defend 6 climate change activists in the second Ratcliffe On Soar trial submitting arguments on abuse and disclosure leading to the collapse of the prosecution; she allegedly had Robertson work with non-governmental organisations on promotion of lesbian rights; she allegedly had Robertson appear in phony inquests in re deaths of Jean Charles de Menezes, Mikey Powell, Diana, Princess of Wales/Dodi Al Fayed, Harry Stanley and Ruddock and others (the second New Cross Fire inquest); she allegedly had Robertson represent families in several so-called “suicide-by-cop” cases; she allegedly had Robertson represent bereaved families and survivors of the 7th July 2005 bombings; she allegedly had Robertson work with a team of trustees in a UK and Zambia-based charity to move orphans and vulnerable children through the hands of predators in the HIV/AIDS community; she allegedly had Robertson work as a legal adviser to Presiding Judge Patrick Robinson during the phony trial of former Head of State Slobodan Milosevic at the UN International Criminal Tribunal for the former Yugoslavia; she allegedly had Robertson infiltrate Mad Cow agents, equipped with FC-Ku PKI, into Sullivan & Cromwell LLP’s New York office for phony criminal probe into Enron and Arthur Andersen; she allegedly has told Robertson to get Barack Obama made an Honourary Bencher of the Middle Temple like David Cameron and John Major; she allegedly had Robertson work with Sheila Morag Clark Cameron – called to Middle Temple bar in 1957 – and Julian Assange on the transfer of the contents of the Cardiff Internet Movie Database at Cardiff University in the UK into the Internet Movie Database (IMDb) launched on October 17, 1990; she allegedly had Robertson, Cameron and Assange force the sale of IMDb in 1998 to Amazon.com a subsidiary of Amazon where today it allegedly supports a PKI FC-Ku snuff film service, including backhauling, editing, archiving and copyright functions offered by Middle Templars to their Mad Cow clients; she allegedly had Robertson, Assange and Vaughan Smith set up the FC-Ku public key infrastructure required for the Navy Seal mission which led to the snuff-film death of an Osama bin Laden doppelganger on May 1st 2011; she allegedly had Robertson, Assange and Vaughan Smith set up the FC-Ku public key infrastructure required for the subsequent mission with a National Guard Chinook helicopter which led to the snuff film deaths on August 6 of 22 Navy Seals who might otherwise have exposed the Obama Administration fraud in re the claim to have killed Osama bin Laden on May Day. Contact e-mails j.rollinson@doughtystreet.co.uk; g.robertson@doughtystreet.co.uk]”
 68. Heather Anne Mills “[Matrix 5 principal and former wife of allegedly extorted man-in-the-middle Paul McCartney, whose Beatles group and its manager Brian Epstein were targeted by pedophile extortionists acting on the orders of the Kray Twins; she allegedly worked with Krayleigh Enterprises to extort the transfer and control of Beatles IP and affairs to Middle Templar clients in 100+ City & Guilds Livery Companies, including the Worshipful Companies of Musicians, Information Technologists and Stationers and Newspaper Makers; she allegedly had evidence from Kray agents relating to the sexual activities of the Beatles by which they could be entrapped and extorted; she is the former wife of allegedly extorted man-in-the-middle Alfie Karmal (married 6 May 1989 – divorced 1991); she is a former lover of allegedly extorted man-in-the-middle Miloš Pogačar, a ski instructor in Croatia in 1990, whom she allegedly used to trigger events which led to the Croatian War; she allegedly organized weapons shipments to Croatia and used modeling (?) assignments in Austria SOS Children’s Villages to entrap and extort pedophile leaders on both sides into contrived atrocities; she claims she was kidnapped and sexually assaulted by a swimming pool attendant when she was eight years old; her next door neighbour, Margaret Ambler, alleged that Mills’ story was “nothing what she made it out to be”, that Mills was never a victim, and the pool attendant did not commit suicide; she went to live in Paris in 1987, telling Karmal that a cosmetics company had given her a modelling contract; she was the mistress of allegedly extorted man-in-the-middle millionaire Lebanese businessman George Kazan for two years; he claims she was always determined to marry a very rich man but for nearly two years, he rented her a luxurious Parisian apartment, paid some of her bills and helped to fund a fabulous jet- set lifestyle; ‘She twisted me around her little finger; she is very clever and she always knew exactly what she wanted – she wanted to be famous and she wanted money And now Mr McCartney has provided her with everything that she ever wanted.’; she met Kazan through a modelling agency when she was 19 and he was 47 in the Cote D’Azur resort of Cannes; he was then a diplomatic representative of the ruler of Qatar and allegedly persuaded the Emir of Qatar to adopt and adapt the BBC’s Middle East Service to become the al-Jazeera propaganda arm of Matrix 5 through the 911 attack; she participated in photo session for a stills-only German sex education manual called Die Freuden der Liebe (The Joys of Love), in which she was photographed explicitly simulating sex with an equally nude male model, Peter Wilson; in 1995, she got engaged to British media executive Marcus Stapleton, after being together for only 16 days; she was then engaged to documentary filmmaker Chris Terrill in 1999, after only 12 days in Cambodia, where they were making a film about landmines; she allegedly blackmailed Terrill into using the then-new digital technology to become the first front line filmmaker to operate as a self shooting/self recording director in the early 1990s; she allegedly blackmailed Terrill into directing Soho Stories as cover for Kray-style pedophile snuff films; she allegedly blackmailed Terrill into training the Naudet Brothers in a docu-soap style of snuff filmmaking as broadcast live through Onion Router PKI, Sohonet, Tuvalu .tv and IMDb on 911; she ended the relationship with Terrill five days before their planned wedding day; she told friends in the media that she had called the wedding off because Terrill was gay, an MI6 agent, and that his mission was to undermine her anti-landmine work; he told her that he had been interviewed by the intelligence services when he was thinking of a career with the Foreign Office, but later said, “I soon realised that Heather had a somewhat elastic relationship with the truth, which she was able to stretch impressively sometimes”; she was, according to Rebekah ‘Skyhacker’ Wade, the former editor of the News of the World, a principal provider of escort services to Adnan Khashogi, the Saudi billionaire businessman and Kerry Packer, the Australian media tycoon; an affidavit from escort girl Denise Hewitt (who was paid ?50,000 for the story), said Mills provided sexual services and boasted of earning up to ?10,000 in a single night; Hewitt said that Mills often requested to work with two girls at a time “… to do a ‘girlie scene’. By this I knew she meant lesbian sex” said Hewitt “I thought at the time that Heather may have been bisexual”; ‘Skyhacker’ Wade published through The Daily Mail accounts of another escort girl, Petrina Montrose, and from other friends confirming that Mills had worked with them as an escort girl on many occasions. Montrose said that once “when all three of them were in the bedroom, Heather had ‘tried it on’ with [escort girl] Joanna and suggested lesbian sex”; Mills denied through her lawyers, ever having been an escort girl and said she would sue as soon as her divorce was concluded but this has not happened; Rebekah ‘Skyhacker’ Wade questioned Abdul Khoury, who was Khashoggi’s personal secretary from 1977 to 2005, and published Khoury’s affirmation as to the veracity of reports that Mills “had sex with him [Khashoggi] on a number of occasions in return for money. Mr Khashoggi was always very pleased with Heather’s performance. She was very athletic in bed”; she allegedly aided Adnan Khashogi in a joint venture with genocidal, pedophile Canadian Privy councilor and U.N. insider, Maurice Strong, to set up pedophile oath taking centers around the world such as SOS Children’s Villages, where U.N. officials could be entrapped and extorted into supporting the attack on the United States of 911; allegedly, on the eve of 911, Mills was one of the Middle Templars’ Mad Cows best qualified to order extorted pedophiles in the international community to co-operate with the violent transfer of U.S. Congressional authority to the United Nations and a future ‘Ecocide’ where the earth’s population is brought down to 500 million; cf. One Crown Office Row.]”
68. Heather Anne Mills “[Matrix 5 principal and former wife of allegedly extorted man-in-the-middle Paul McCartney, whose Beatles group and its manager Brian Epstein were targeted by pedophile extortionists acting on the orders of the Kray Twins; she allegedly worked with Krayleigh Enterprises to extort the transfer and control of Beatles IP and affairs to Middle Templar clients in 100+ City & Guilds Livery Companies, including the Worshipful Companies of Musicians, Information Technologists and Stationers and Newspaper Makers; she allegedly had evidence from Kray agents relating to the sexual activities of the Beatles by which they could be entrapped and extorted; she is the former wife of allegedly extorted man-in-the-middle Alfie Karmal (married 6 May 1989 – divorced 1991); she is a former lover of allegedly extorted man-in-the-middle Miloš Pogačar, a ski instructor in Croatia in 1990, whom she allegedly used to trigger events which led to the Croatian War; she allegedly organized weapons shipments to Croatia and used modeling (?) assignments in Austria SOS Children’s Villages to entrap and extort pedophile leaders on both sides into contrived atrocities; she claims she was kidnapped and sexually assaulted by a swimming pool attendant when she was eight years old; her next door neighbour, Margaret Ambler, alleged that Mills’ story was “nothing what she made it out to be”, that Mills was never a victim, and the pool attendant did not commit suicide; she went to live in Paris in 1987, telling Karmal that a cosmetics company had given her a modelling contract; she was the mistress of allegedly extorted man-in-the-middle millionaire Lebanese businessman George Kazan for two years; he claims she was always determined to marry a very rich man but for nearly two years, he rented her a luxurious Parisian apartment, paid some of her bills and helped to fund a fabulous jet- set lifestyle; ‘She twisted me around her little finger; she is very clever and she always knew exactly what she wanted – she wanted to be famous and she wanted money And now Mr McCartney has provided her with everything that she ever wanted.’; she met Kazan through a modelling agency when she was 19 and he was 47 in the Cote D’Azur resort of Cannes; he was then a diplomatic representative of the ruler of Qatar and allegedly persuaded the Emir of Qatar to adopt and adapt the BBC’s Middle East Service to become the al-Jazeera propaganda arm of Matrix 5 through the 911 attack; she participated in photo session for a stills-only German sex education manual called Die Freuden der Liebe (The Joys of Love), in which she was photographed explicitly simulating sex with an equally nude male model, Peter Wilson; in 1995, she got engaged to British media executive Marcus Stapleton, after being together for only 16 days; she was then engaged to documentary filmmaker Chris Terrill in 1999, after only 12 days in Cambodia, where they were making a film about landmines; she allegedly blackmailed Terrill into using the then-new digital technology to become the first front line filmmaker to operate as a self shooting/self recording director in the early 1990s; she allegedly blackmailed Terrill into directing Soho Stories as cover for Kray-style pedophile snuff films; she allegedly blackmailed Terrill into training the Naudet Brothers in a docu-soap style of snuff filmmaking as broadcast live through Onion Router PKI, Sohonet, Tuvalu .tv and IMDb on 911; she ended the relationship with Terrill five days before their planned wedding day; she told friends in the media that she had called the wedding off because Terrill was gay, an MI6 agent, and that his mission was to undermine her anti-landmine work; he told her that he had been interviewed by the intelligence services when he was thinking of a career with the Foreign Office, but later said, “I soon realised that Heather had a somewhat elastic relationship with the truth, which she was able to stretch impressively sometimes”; she was, according to Rebekah ‘Skyhacker’ Wade, the former editor of the News of the World, a principal provider of escort services to Adnan Khashogi, the Saudi billionaire businessman and Kerry Packer, the Australian media tycoon; an affidavit from escort girl Denise Hewitt (who was paid ?50,000 for the story), said Mills provided sexual services and boasted of earning up to ?10,000 in a single night; Hewitt said that Mills often requested to work with two girls at a time “… to do a ‘girlie scene’. By this I knew she meant lesbian sex” said Hewitt “I thought at the time that Heather may have been bisexual”; ‘Skyhacker’ Wade published through The Daily Mail accounts of another escort girl, Petrina Montrose, and from other friends confirming that Mills had worked with them as an escort girl on many occasions. Montrose said that once “when all three of them were in the bedroom, Heather had ‘tried it on’ with [escort girl] Joanna and suggested lesbian sex”; Mills denied through her lawyers, ever having been an escort girl and said she would sue as soon as her divorce was concluded but this has not happened; Rebekah ‘Skyhacker’ Wade questioned Abdul Khoury, who was Khashoggi’s personal secretary from 1977 to 2005, and published Khoury’s affirmation as to the veracity of reports that Mills “had sex with him [Khashoggi] on a number of occasions in return for money. Mr Khashoggi was always very pleased with Heather’s performance. She was very athletic in bed”; she allegedly aided Adnan Khashogi in a joint venture with genocidal, pedophile Canadian Privy councilor and U.N. insider, Maurice Strong, to set up pedophile oath taking centers around the world such as SOS Children’s Villages, where U.N. officials could be entrapped and extorted into supporting the attack on the United States of 911; allegedly, on the eve of 911, Mills was one of the Middle Templars’ Mad Cows best qualified to order extorted pedophiles in the international community to co-operate with the violent transfer of U.S. Congressional authority to the United Nations and a future ‘Ecocide’ where the earth’s population is brought down to 500 million; cf. One Crown Office Row.]”
69. Serena, Lady Rothschild (nee Dunn) “[Matrix 5 principal and wife of the allegedly-extorted man-in-the-middle Jacob Rothschild, 4th Baron Rothschild, whom she married in 20 October 1961; she allegedly had her Rothschild husband invest in the development of patent pools for Templar clients in the City & Guilds Livery Companies; on behalf of Templar clients in the Worshipful Company of Spectacle Makers, she allegedly had her Rothschild husband invest in the development of Bell & Howell patent pools to shoot and backhaul over Ku-band, snuff-film images of the assassination of JFK in 1963; she allegedly had her Rothschild husband and his cousin Sir Evelyn de Rothschild, develop bogus continuity of government protocols launched by Victor Rothschild (‘The Fifth Man’) in WW11 for a man-in-the-middle attack on America on 911; she allegedly had her Rothschild husband help to finance Rupert Murdoch’s acquisition in 1992 of NDS Group Plc pay-per-view encryption technology developed by Israeli cryptographer Adi Shamir and scientists of the Weizmann Institute in Rehovot, Israel; she allegedly had her Rothschild husband and Rupert Murdoch integrate NDS pay-per-view technology with Onion Router encryption to support News Corp / Sky News pay per view service of ‘Wag the Dog’ propaganda and FC-Ku snuff-film images; she allegedly conspired with Evelyn de Rothschild’s wife, Lynn Forester, in the use of Luxembourg-based wireless broadband venture FirstMark Communications Europe for MitM attacks during 911; she allegedly conspired with Evelyn de Rothschild’s wife, Lynn Forester in setting up her honeymoon stay in the White House with the Clintons to discuss the plans to overthrow the United States government on 911; her paternal grandfather was the late Canadian financier, Sir James Dunn; she is the mother of allegedly-extorted man-in-the-middle Nathaniel Philip Rothschild; she educated her son at Colet Court ( same year as George ‘Whip Me’ Osborne), Eton College and Wadham College, Oxford; her son was a member of the allegedly pedophile oath-taking Bullingdon Club at the same time as George Osborne, now Chancellor of the Exchequer; she allegedly had her son organize a bogus party to entrap Labour politician Peter Mandelson, Russian businessman Oleg Deripaska and then-Conservative Shadow-Chancellor George Osborne on a yacht moored near Corfu; she allegedly has archived at D2 Banking Canary Wharf, video records of Osborne illicitly trying to solicit donations for the Tory party deputy chairman and chief fundraiser Michael Ashcroft from Deripaska; she allegedly had her son organize a party at the Splendid Hotel in Bečići Montenegro, to entrap the son of Libyan dictator Muammar Gaddafi, Saif al-Islam Muammar al-Gaddafi, Arcelor Mittal CEO Lakshmi Mittal, the gold magnate Peter Munk and Oleg Deripaska; she allegedly had her husband work with Rothschild clients and hedge-fund insiders on the development of Livery Company patent pools to give the following companies an opportunity to eliminate or intimidate ‘interlopers’ and establish monopoly control over global supply chains: Scientific Instrument Makers, Chartered Surveyors, Chartered Accountants in England and Wales, Chartered Secretaries and Administrators, Builders Merchants, Launderers, Marketors, Actuaries, Insurers, Arbitrators, Engineers, Fuellers, Lightmongers, Environmental Cleaners, Chartered Architects, Constructors, Information Technologists, World Traders, Water Conservators, Firefighters, Hackney Carriage Drivers, Management Consultants, International Bankers, Tax Advisers, Security Professionals.]”
 70. Baroness Scotland of Asthal (nee Patricia Janet) “[Matrix 5 principal and former Parliamentary Under-Secretary of State at the Foreign and Commonwealth Office (1999 -2001) for the late and allegedly-extorted man-in-the-middle Robert Finlayson Cook; she allegedly extorted Cook while he served as Foreign Secretary from 1997 to June 8, 2001 to authorize Templar use of VideoGuard for an ‘Al-Qaeda’ 911 dress rehearsal on June 1-2, 2001, cf. Amalgam Virgo; at the Foreign and Commonwealth Office, she was inter alia, responsible for the UK Government’s diplomatic relations with North America, the Caribbean, Overseas Territories, Consular Division, British Council, administration and all Parliamentary business in the House of Lords; she was a party to the alleged use by Kristine Marcy of VideoGuard to the role of SBA 8(a) companies whose owners are affiliated to the Alliance of Small Island States, in the protégé attack on U.S. mentor companies on 911; she allegedly authorized the use of VideoGuard to conceal the snuff-film murder of Cook on 6 August 2005 after he had threatened to expose the Al-Qaeda Men Who Never Were on 911; she was fined £5,000 for hiring an illegal immigrant from Tonga who served as her housekeeper but was allegedly employed to help her develop the NATO-enforced protection racket which is presently enriching insiders of the Alliance of Small Island States; she was born in the Commonwealth of Dominica – another member of the NATO-enforced protection racket for insiders of the Alliance of Small Island States – as the tenth child of twelve; she pursued a London University (LLB) law degree in 1976 (in association with University College London [where Templars allegedly recruited the Christmas crotch bomber]); she was called to the bar at the Middle Temple in 1977, specialising in family and children’s law which would have given her inside information on the alleged Templar pedophile entrapment and extortion trade; she become the first black woman to be appointed a Queen’s Counsel in 1991 where she allegedly began extorting her colleagues; she founded 1 Gray’s Inn Square barristers chambers, allegedly working with Kristine Marcy to move saboteurs, assassins and deception experts into the united States, cf. Barrack Obama CUKC status as illegal alien; she was elected as a Bencher of the Middle Temple in 1997 she was named as a Millennium Commissioner on 17 February 1994, allegedly to help Templars and their clients to prepare an attempted Y2K coup d’etat; she was a member of the Commission for Racial Equality and allegedly used Matrix 5 community organization techniques to ‘rub raw the sores of discontent’; she received a life peerage on a Labour Party list of working peers in 1997; she served as Attorney General for England and Wales and Advocate General for Northern Ireland; she would have superintended the Treasury Solicitors, the Director of the Serious Fraud Office, and the Revenue and Customs Prosecution Office; she introduced the International Criminal Court Bill which sought to ratify the jurisdiction of the International Criminal Court into UK law and eliminate presumption of innocence and any hope of Grand Jury remedies to government corruption; she established Pro Bono Lawyers Panel to release nationals imprisoned in foreign countries; she created an Overseas Territories Council for the Caribbean and reformed and restructured the Foreign and Commonwealth Office’s Consular Division to eliminate or thwart criminal investigations into the VideoGuard enabled September 11 attacks; she claims loneliness of priests leads to pedophilia and she thereby equates the crime of paedophilia with the social condition of the pedophile; she allegedly extorted Foreign Office through Matrix 5 lesbian and DOJ Pride community to arrange a plea bargain for the ‘NatWest Three’ under which they pleaded guilty to a single count of wire fraud in the United States.]”
70. Baroness Scotland of Asthal (nee Patricia Janet) “[Matrix 5 principal and former Parliamentary Under-Secretary of State at the Foreign and Commonwealth Office (1999 -2001) for the late and allegedly-extorted man-in-the-middle Robert Finlayson Cook; she allegedly extorted Cook while he served as Foreign Secretary from 1997 to June 8, 2001 to authorize Templar use of VideoGuard for an ‘Al-Qaeda’ 911 dress rehearsal on June 1-2, 2001, cf. Amalgam Virgo; at the Foreign and Commonwealth Office, she was inter alia, responsible for the UK Government’s diplomatic relations with North America, the Caribbean, Overseas Territories, Consular Division, British Council, administration and all Parliamentary business in the House of Lords; she was a party to the alleged use by Kristine Marcy of VideoGuard to the role of SBA 8(a) companies whose owners are affiliated to the Alliance of Small Island States, in the protégé attack on U.S. mentor companies on 911; she allegedly authorized the use of VideoGuard to conceal the snuff-film murder of Cook on 6 August 2005 after he had threatened to expose the Al-Qaeda Men Who Never Were on 911; she was fined £5,000 for hiring an illegal immigrant from Tonga who served as her housekeeper but was allegedly employed to help her develop the NATO-enforced protection racket which is presently enriching insiders of the Alliance of Small Island States; she was born in the Commonwealth of Dominica – another member of the NATO-enforced protection racket for insiders of the Alliance of Small Island States – as the tenth child of twelve; she pursued a London University (LLB) law degree in 1976 (in association with University College London [where Templars allegedly recruited the Christmas crotch bomber]); she was called to the bar at the Middle Temple in 1977, specialising in family and children’s law which would have given her inside information on the alleged Templar pedophile entrapment and extortion trade; she become the first black woman to be appointed a Queen’s Counsel in 1991 where she allegedly began extorting her colleagues; she founded 1 Gray’s Inn Square barristers chambers, allegedly working with Kristine Marcy to move saboteurs, assassins and deception experts into the united States, cf. Barrack Obama CUKC status as illegal alien; she was elected as a Bencher of the Middle Temple in 1997 she was named as a Millennium Commissioner on 17 February 1994, allegedly to help Templars and their clients to prepare an attempted Y2K coup d’etat; she was a member of the Commission for Racial Equality and allegedly used Matrix 5 community organization techniques to ‘rub raw the sores of discontent’; she received a life peerage on a Labour Party list of working peers in 1997; she served as Attorney General for England and Wales and Advocate General for Northern Ireland; she would have superintended the Treasury Solicitors, the Director of the Serious Fraud Office, and the Revenue and Customs Prosecution Office; she introduced the International Criminal Court Bill which sought to ratify the jurisdiction of the International Criminal Court into UK law and eliminate presumption of innocence and any hope of Grand Jury remedies to government corruption; she established Pro Bono Lawyers Panel to release nationals imprisoned in foreign countries; she created an Overseas Territories Council for the Caribbean and reformed and restructured the Foreign and Commonwealth Office’s Consular Division to eliminate or thwart criminal investigations into the VideoGuard enabled September 11 attacks; she claims loneliness of priests leads to pedophilia and she thereby equates the crime of paedophilia with the social condition of the pedophile; she allegedly extorted Foreign Office through Matrix 5 lesbian and DOJ Pride community to arrange a plea bargain for the ‘NatWest Three’ under which they pleaded guilty to a single count of wire fraud in the United States.]”
71. Louise di Mambro “[Matrix 5 principal and Middle Templar associate of allegedly-extorted members of the Privy Council and The Supreme Court of the United Kingdom; she was called to the Middle Temple Bar in July 1976; she was appointed Registrar of the Privy Council by HM Queen Elizabeth II on 1 April 2011, having previously performed this duty in an acting capacity from May 2009; she allegedly procured public key infrastructure through PriceWaterhouseCoopers (‘PwC’) to make both Courts vulnerable to man-in-the middle propaganda attack on their Rules and Practice Directions and judicial and administrative functions; she allegedly procured VideoGuard pay-per-view encryption devices through PwC’s PKI so that members of the Courts could be monitored and entrapped when they bought and viewed snuff-film images of pedophilia and child abuse; she allegedly created MitM opportunities for VideoGuard content providers such as BSkyB or DirecTV in the United States to entrap and extort viewers with the threat of “group media busts,” where people are exposed as pedophiles by online organizations such as Perverted-Justice; the first such event was conducted in late 2003, in co-operation with investigative reporter John Mercure at Milwaukee’s WTMJ-TV – a VideoGuard-encrypted content provider – whom the site credits with initially conceiving the concept; VideoGuard use has enabled Perverted-Justice to claim 535 convictions in 39 states across the United States attributed to its sting operations with 33 of these taking place in 2005, 81 in 2006, and 141 in 2007, 42 in 2008, and 195 in 2009; convictions in the U.S. include disorderly conduct, indecently soliciting a child, attempting to entice a juvenile to travel with intent to engage in sexual act, transporting child pornography, and possession and dissemination of child pornography; she allegedly procured VideoGuard PKI for Rebekah Wade at the News of the World to “name and shame” convicted child sex offenders after the murder of Sarah Payne; she was Deputy Head of the Judicial Office of the House of Lords, supporting the Law Lords in their judicial functions from June 2008 until August 2009; she was a deputy master in the Court of Appeal, Civil Division, working in the Royal Courts of Justice from December 1997 to May 2008; as Registrar she allegedly uses VideoGuard PKI to ‘steer’ cases through the High Court of Justice, the Court of Appeal and the Crown Court; she allegedly uses VideoGuard PKI to steer all high value and high importance cases through the senior courts including the Senior Courts Costs Office, which deals with the quantification of legal costs pursuant to costs orders made by the courts; as Registrar she allegedly uses VideoGuard PKI to ‘steer’ cases through the Family Division which has jurisdiction to hear all cases relating to children’s welfare and interest, and exercises an exclusive jurisdiction in wardship cases; as Registrar she allegedly uses VideoGuard PKI to ‘steer’ cases through the Chancery Division which deals with business law, trusts law, probate law, and land law in relation to issues of equity; as Registrar she allegedly uses VideoGuard PKI to ‘steer’ cases through the Chancery Division’s specialist courts – the Patents Court and the Companies Court – which deal with intellectual property and company law matters respectively; as Registrar she allegedly uses VideoGuard PKI to ‘steer’ cases through the Chancery Division’s tax appeals; she held various posts as a member of the Government Legal Service in the Treasury Solicitor’s Department and the Lord Chancellor’s Department from September 1977 to December 1997; she allegedly helped the Lord Chancellor’s Department in the UK and Kristine Marcy’s DOJ Pride associates in Washington D.C. to integrate the VideoGuard pay-per-view snuff film service; she and Marcy allegedly procured the patent for use of the VideoGuard pay-per-view snuff-film service to finance the bombing of the Murrah Building in 1995 and the murder of JonBenet Ramsey on Christmas Day 1996; she and Marcy allegedly procured the patent for use of the VideoGuard pay-per-view snuff-film service to finance the 911 attacks where preparations began immediately after News Corporation bought a 49% stake in VideoGuard in 1992; she and Marcy have allegedly procured the patent for use of the VideoGuard pay-per-view snuff-film service to finance Matrix 5 propaganda attacks on Libya, mass murder and the confiscation of assets in the country’s supply chains to enrich Middle Templar clients amongst the City & Guilds’ Livery Companies.]”
 72. Lena E. Trudeau (nee SOS Children’s Villages breeding station?) “[Revised June 11, 2012. Matrix 5 principal and the apparent love child of the late, allegedly-extorted man-in-the-middle Pierre Elliott Trudeau, the former Canadian Prime Minister; her alleged bisexual mentor and possible biological father was the sponsor of serial acts of political corruption including abolition of Grand Jury rights in Canada in 1984 and extortion of Privy Councilors into adopting the creed of ‘Guild of Pig Farm Socialism’; she allegedly placed a mail order for a severed head with Luka Magnotta through Canada Post; she is allegedly engaged in a seditious conspiracy to silence prospective whistleblowers who threaten to expose her ‘Collaborators’ and the operation of a Virtual Global Taskforce as a crypto-pedophile ring; she allegedly identified the recipient of the Magnotta head as the individual who had recognized her Collaborators’ crypto-pedophile signature in the ‘electronic capture’ of FADEC (BAE) systems in the May 9 crash of a Sukhoi Superjet in Indonesia; she has allegedly modeled her career on the teaching of G.D.H. Cole and the M.O. of pedophile-entrapment, blackmail and murder-for-hire service operated out of Toynbee Hall and Hull House; she allegedly hired Russell Williams through the Canadian Privy Council to procure illegally-modified Bombardier aircraft and train Al-Qaeda Free Flight pilots for the decoy-and-drone maneuvers of 9/11; she allegedly planned to take control of American air space on 9/11, kill political leaders and transition the elected government of the United States to the unelected Senior Executive Service led by her same-sex NAPA partner, Kristine Marcy; she allegedly procured Entrust public keys for use by her alleged collaborators in the Pickton pig farm murders to bypass 9-1-1 first responders and launch a Matrix 5 man-in-the-middle propaganda attack to discredit the RCMP; she allegedly used the Ripper-Clipper M.O. to conceal the Pickton pig farm murders (1979-2002) and the JonBenét Ramsey torture killing in 1996; she was an alleged designer of the top-official oath taking ceremonies for B.C. pig farm modeled on techniques used in the `50s by Maurice Strong and Obama’s grandfather in the Mau Mau, Kenya; she allegedly hired a Guild of Pig Farm Socialists to film Canadian Privy Councilors at B.C. pig-farm cannibal feasts put on by the Piggy’s Palace Good Times Society; she allegedly used Ripper psychopaths equipped with Clipper hacking devices, in the Guild of Professional Home Services to spoliate evidence of Matrix 5 propaganda attacks on first responders at crime scenes; she allegedly extorted Privy Council authority for Macdonald Dettwiler and Associates to launch a Matrix 5 man-in-the-middle attack on the USS Cole through its Maritime Command Operational Information Network; she allegedly implemented Entrust public key infrastructure and Clipper Chip encryption to support the delegation of Privy Council authority to Bombardier EW pilot Russell Williams to produce a snuff film of the murder of JonBenet Ramsey in 1996; she allegedly served as an extortionist consultant to the Canadian Privy Councillors Prince Philip and the genocidal pedophile Maurice Strong who shook down Ted Turner, Jane Fonda’s ex-husband and boss of CNN.tv for $1 billion to UN depopulation projects; she is the Vice-President and co-leader of National Academy of Public Administration `NAPA’ in Washington, D.C. with President Kristine Marcy; she is the director of Collaboration Project; sponsor of web 2.0 to overthrow sovereign governments with Matrix 5 – a B.A.F.L.P matrix of community organizers under Obama Open Government Initiative; she hosted Web site on .tv to monitor public’s reaction to sabotage, assassinations and deception under Open Government Directive; she chose OGD as an anagram of GOD and designed the OGD model for all federal agencies; she built a VeriSign .tv backdoor into DoD Public Key Enablement (PKE) for cross-certificate chaining with Entrust (FBCA) Common Policy Root Certification Authority (CA); she allegedly used .tv to authorize snuff-film contract hits per Fort Hood, Gifford, Gunwalker and OBL; she allegedly led NAPA insider-trading conspiracies with employee savings options plan (`ESOP’) at U.S. Coast Guard, Federal Emergency Management Agency, Environmental Protection Agency, Department of State and the National Park Service; she allegedly used Entrust PKI to authorize sabotage of the BP/Deepwater Horizon project and trigger credit-default swaps and phony cat-bond claims through D2 Banking; she pioneered use of Entrust PKI, Clipper hacking and Onion Router patent devices in Privy Council snuff film .tv and murder for hire; she brings over 15 years of consulting and management experience to the National Academy; she is a former Vice President of Consulting Services for Ambit Group in federal marketplaces; she is a former insider of Touchstone Consulting (now SRA, Inc.); former Marketing Manager, Nokia Enterprise Solutions; she allegedly integrated Nokia PCD with Bombardier electronic warfare systems to support Matrix 5 attacks; she is an alleged racketeering alumna of Greek Life at the Richard Ivey School of Business at the University of Western Ontario and the Political Science and Philosophy faculty at the University of Ottawa.]”
72. Lena E. Trudeau (nee SOS Children’s Villages breeding station?) “[Revised June 11, 2012. Matrix 5 principal and the apparent love child of the late, allegedly-extorted man-in-the-middle Pierre Elliott Trudeau, the former Canadian Prime Minister; her alleged bisexual mentor and possible biological father was the sponsor of serial acts of political corruption including abolition of Grand Jury rights in Canada in 1984 and extortion of Privy Councilors into adopting the creed of ‘Guild of Pig Farm Socialism’; she allegedly placed a mail order for a severed head with Luka Magnotta through Canada Post; she is allegedly engaged in a seditious conspiracy to silence prospective whistleblowers who threaten to expose her ‘Collaborators’ and the operation of a Virtual Global Taskforce as a crypto-pedophile ring; she allegedly identified the recipient of the Magnotta head as the individual who had recognized her Collaborators’ crypto-pedophile signature in the ‘electronic capture’ of FADEC (BAE) systems in the May 9 crash of a Sukhoi Superjet in Indonesia; she has allegedly modeled her career on the teaching of G.D.H. Cole and the M.O. of pedophile-entrapment, blackmail and murder-for-hire service operated out of Toynbee Hall and Hull House; she allegedly hired Russell Williams through the Canadian Privy Council to procure illegally-modified Bombardier aircraft and train Al-Qaeda Free Flight pilots for the decoy-and-drone maneuvers of 9/11; she allegedly planned to take control of American air space on 9/11, kill political leaders and transition the elected government of the United States to the unelected Senior Executive Service led by her same-sex NAPA partner, Kristine Marcy; she allegedly procured Entrust public keys for use by her alleged collaborators in the Pickton pig farm murders to bypass 9-1-1 first responders and launch a Matrix 5 man-in-the-middle propaganda attack to discredit the RCMP; she allegedly used the Ripper-Clipper M.O. to conceal the Pickton pig farm murders (1979-2002) and the JonBenét Ramsey torture killing in 1996; she was an alleged designer of the top-official oath taking ceremonies for B.C. pig farm modeled on techniques used in the `50s by Maurice Strong and Obama’s grandfather in the Mau Mau, Kenya; she allegedly hired a Guild of Pig Farm Socialists to film Canadian Privy Councilors at B.C. pig-farm cannibal feasts put on by the Piggy’s Palace Good Times Society; she allegedly used Ripper psychopaths equipped with Clipper hacking devices, in the Guild of Professional Home Services to spoliate evidence of Matrix 5 propaganda attacks on first responders at crime scenes; she allegedly extorted Privy Council authority for Macdonald Dettwiler and Associates to launch a Matrix 5 man-in-the-middle attack on the USS Cole through its Maritime Command Operational Information Network; she allegedly implemented Entrust public key infrastructure and Clipper Chip encryption to support the delegation of Privy Council authority to Bombardier EW pilot Russell Williams to produce a snuff film of the murder of JonBenet Ramsey in 1996; she allegedly served as an extortionist consultant to the Canadian Privy Councillors Prince Philip and the genocidal pedophile Maurice Strong who shook down Ted Turner, Jane Fonda’s ex-husband and boss of CNN.tv for $1 billion to UN depopulation projects; she is the Vice-President and co-leader of National Academy of Public Administration `NAPA’ in Washington, D.C. with President Kristine Marcy; she is the director of Collaboration Project; sponsor of web 2.0 to overthrow sovereign governments with Matrix 5 – a B.A.F.L.P matrix of community organizers under Obama Open Government Initiative; she hosted Web site on .tv to monitor public’s reaction to sabotage, assassinations and deception under Open Government Directive; she chose OGD as an anagram of GOD and designed the OGD model for all federal agencies; she built a VeriSign .tv backdoor into DoD Public Key Enablement (PKE) for cross-certificate chaining with Entrust (FBCA) Common Policy Root Certification Authority (CA); she allegedly used .tv to authorize snuff-film contract hits per Fort Hood, Gifford, Gunwalker and OBL; she allegedly led NAPA insider-trading conspiracies with employee savings options plan (`ESOP’) at U.S. Coast Guard, Federal Emergency Management Agency, Environmental Protection Agency, Department of State and the National Park Service; she allegedly used Entrust PKI to authorize sabotage of the BP/Deepwater Horizon project and trigger credit-default swaps and phony cat-bond claims through D2 Banking; she pioneered use of Entrust PKI, Clipper hacking and Onion Router patent devices in Privy Council snuff film .tv and murder for hire; she brings over 15 years of consulting and management experience to the National Academy; she is a former Vice President of Consulting Services for Ambit Group in federal marketplaces; she is a former insider of Touchstone Consulting (now SRA, Inc.); former Marketing Manager, Nokia Enterprise Solutions; she allegedly integrated Nokia PCD with Bombardier electronic warfare systems to support Matrix 5 attacks; she is an alleged racketeering alumna of Greek Life at the Richard Ivey School of Business at the University of Western Ontario and the Political Science and Philosophy faculty at the University of Ottawa.]”
73. Gloria Cain (nee ) “[Revised October 8, 2011. Matrix 5 wife of allegedly extorted man-in-the-middle presidential candidate Herman Cain, a former civilian employee of the U.S. Navy, a former chairman and CEO of Godfather’s Pizza and a former deputy chairman (1992–94) and chairman (1995–96) of the board of directors to the Federal Reserve Bank of Kansas City; she allegedly used VideoGuard-encrypted images of Greek Life oath ceremonies to extort U.S. Navy support for Protégé Ballistics war game maneuvers on 9/11 synched to Fox News broadcast of Matrix 5 propaganda; she allegedly used her Black Greek Life associates to design the ballistic profiles flown in the decoy murder of Captain Chic Burlingame and the Matrix 5 VideoGuard attack on the Pentagon’s U.S. Navy Command Center on 9/11; she was allegedly recruited into Matrix 5 training program through oath-taking ceremonies set up by lesbian / pedophile cult in the Delta Sigma Theta Greek Life sorority at Morris Brown College from where she graduated in 1968; she allegedly conspired with a fellow Delta Sigma Theta soror, Allison Seymour at Fox News, to develop the script for a VideoGuard encrypted broadcast of Ballistics 9/11; she allegedly helped her husband as a principal or an accessory to a systemic fraud on black students at Morris Brown College which resulted in the de facto closure of the school in 2002 after decades of manipulation of the Pell Grant system by the Soror Identity boss of the Senior Executive Service; she allegedly helped her husband develop Pell Grants to fund U.S. college students, including prisoners, launch treasonous careers in the racketeering enforcement of the United Nations Convention on the Law of the Sea and United Nations Environment Programme; she allegedly forced her husband and Senator Pell – arrested during a raid on a New York gay bar in the early 1960s – to push for Roberta Achtenberg, a lesbian, to serve as Assistant Secretary for Fair Housing and Equal Opportunity in the Department of Housing and Urban Development and engineer the collapse of Fannie Mae; she was allegedly ordered to marry Herman Cain after he had graduated from Morehouse College in 1967 with a B.A. in mathematics and steer him through an M. Sc. in computer science from Purdue University in 1971 to backdoor ballistics weapons development in the U.S. Department of the Navy; she allegedly extorted her husband into running as a candidate for the Republican presidential nomination in 2012 ; she allegedly groomed her husband for the phony role of a right-wing presidential candidate by moving him through the Department of the Navy, The Coca-Cola Company as a business analyst, through Pillsbury where he rose (1977-early 1980s) to the position of Vice President, through Burger King – a Pillsbury subsidiary – where he managed 400 stores in the Philadelphia area, through President and CEO of Godfather’s Pizza, a Pillsbury subsidiary and through a leveraged buyout (1988) as CEO until 1996, when he was asked to resign by the board; she allegedly placed Cain as a member of the board of directors to the Federal Reserve Bank of Kansas City in 1992 and served as its chairman from January 1995 to August 1996 to prepare for the Matrix 5 bank-in-the-middle attack on the capital markets on 9/11; she moved him on to the board of directors of Aquila, Inc from 1992 to 2008 where he allegedly gave the Worshipful Company of Fuellers access to the Matrix 5 TSol business model used to destroy Enron; she has allegedly positioned him as a commentator for Fox Business to conceal her role in the planning of Ballistics 9/11; she allegedly placed him as 1996 Senior Advisor of Dole/Kemp Campaign and as a 2012 presidential candidate for more than 40 Tea Party rallies; she allegedly developed his VideoGuard YouTube profile with Murdoch and Fox insiders ; she allegedly set up his presidential exploratory committee on January 12, 2011 and prepared to place him on the Fox News Channel program Your World with Neil Cavuto; she allegedly triangulated his election profile to the right of Obama by having him state that he was “uncomfortable” when he found that the surgeon operating on his liver and colon cancer was Muslim; she arranged for him later to explain “based upon the little knowledge that I have of the Muslim religion, you know, they have an objective to convert all infidels or kill them”; she allegedly arranged a May 5, 2011 Fox News presidential campaign debate where he competed with Tim Pawlenty, Ron Paul, Gary Johnson and Rick Santorum to be declared the winner by Murdoch pollster Frank Luntz chosen by Fox to run the post-performance focus group; she allegedly arranged for his September 24, 2011 victory in a Republican presidential straw poll in Florida, with 37 percent of the vote to ensure the front-runner Rick Perry, who had been leading in the polls, came in second with a humiliating 15 percent; she allegedly selected his Presidential campaign staff to include Mark Block as Chief of Staff, Linda Hansen as Deputy Chief of Staff and Scott Bieniek as Vice President and General Counsel; she allegedly uses Cain’s position as associate minister at Antioch Baptist Church North in Atlanta to leverage support from the National Baptist Convention, USA; she allegedly had him play the race card by uploading a YouTube video for his campaign where he describes the experience of sitting behind the white / black demarcation on buses and talks about the experience of taking turns with his brother, standing watch as each took a drink from the “white” side of a segregated water fountain in a department store.]”
 74. Alison Lawton “[Alleged Matrix 5 principal and Treasury Solicitor’s ‘ownerless’ goods, born May 29, 1970 in Montréal, Québec, Canada; she is an alleged Greek Life extortionist of Bill Clinton and Frank Giustra – the man-in-the-middle founders of the $300 Million Clinton-Giustra Global Initiative; she is a Greek Life oath taker and alumnus of Communication Studies at Concordia University in 1995; she joined Investor First Financial before founding Winfield Venture Group, a private equity investment firm along with IdeaPark Ventures in 1997; she married Frank Giustra in 2000 and separated in 2008; she allegedly joint ventured Winfield with the CAI Private Equity Group to sell Greek Life investments in syndicated VideoGuard software for film and television, pig-farm real estate and various abusive KPMG tax-shelter offerings including American Psycho, Fahrenheit 9/11 and cannibal snuff-film content from the ‘Piggy’s Palace Good Times Society’; she allegedly used Lionsgate as a front for Greek Life production companies to procure VideoGuard-encrypted images of cannibal feasts at a B.C. pig farm; she allegedly extorted support from her pig farm dinner guests for the Matrix 5 man-in-the-middle propaganda attacks on America of Fahrenheit 9/11; she allegedly extorted Lloyd Axworthy, former Director of the University of British Columbia’s Liu Institute for Global Issues and former Canadian Foreign Affairs Minister – and suspected guest at Piggy’s Palace cannibal feast – into supporting forcible conscription of children in Uganda’s civil war; producer of the Matrix 5 propaganda documentary Uganda Rising; she allegedly helps Crown Agents to place Aids workers in Uganda’s SOS Children’s Villages to train orphans to serve as sextortionists, cannibal killers, sex slaves and breeding mothers; she has allegedly helped to create perception of a mercenary cult in Uganda – the Lord’s Resistance Army (LRA) – whose fighting force is made up in large part of abducted children led by the self-proclaimed prophet Joseph Kony, who says he wants Uganda to live by the laws of the Ten Commandments; she is allegedly extorting President Museveni and his SOS wife into attacking civilians to promote ethnic strife; she was allegedly awarded a Master of Arts in Applied Sciences by Simon Fraser University for her work with Greek Life media in the manipulation of financial markets; she is an alleged extortionist on the board of the Positive Women’s Network and Pacific AIDS Resource Centre (PARC); we alleged that she is accessory before or after the fact to the filmed contract killing of Wendy Ladner Beaudry who threatened to expose the Greek Life cannibal cult; she is the alleged extortionist Chair of the Unite for Children, Unite Against AIDS campaign for UNICEF Canada; she alleged extortionist appointee to the John F. Kennedy School of Government Women’s Leadership Board at Harvard University; she is an alleged extortionist member of the UBC Graduate School of Journalism Advisory Board]”
74. Alison Lawton “[Alleged Matrix 5 principal and Treasury Solicitor’s ‘ownerless’ goods, born May 29, 1970 in Montréal, Québec, Canada; she is an alleged Greek Life extortionist of Bill Clinton and Frank Giustra – the man-in-the-middle founders of the $300 Million Clinton-Giustra Global Initiative; she is a Greek Life oath taker and alumnus of Communication Studies at Concordia University in 1995; she joined Investor First Financial before founding Winfield Venture Group, a private equity investment firm along with IdeaPark Ventures in 1997; she married Frank Giustra in 2000 and separated in 2008; she allegedly joint ventured Winfield with the CAI Private Equity Group to sell Greek Life investments in syndicated VideoGuard software for film and television, pig-farm real estate and various abusive KPMG tax-shelter offerings including American Psycho, Fahrenheit 9/11 and cannibal snuff-film content from the ‘Piggy’s Palace Good Times Society’; she allegedly used Lionsgate as a front for Greek Life production companies to procure VideoGuard-encrypted images of cannibal feasts at a B.C. pig farm; she allegedly extorted support from her pig farm dinner guests for the Matrix 5 man-in-the-middle propaganda attacks on America of Fahrenheit 9/11; she allegedly extorted Lloyd Axworthy, former Director of the University of British Columbia’s Liu Institute for Global Issues and former Canadian Foreign Affairs Minister – and suspected guest at Piggy’s Palace cannibal feast – into supporting forcible conscription of children in Uganda’s civil war; producer of the Matrix 5 propaganda documentary Uganda Rising; she allegedly helps Crown Agents to place Aids workers in Uganda’s SOS Children’s Villages to train orphans to serve as sextortionists, cannibal killers, sex slaves and breeding mothers; she has allegedly helped to create perception of a mercenary cult in Uganda – the Lord’s Resistance Army (LRA) – whose fighting force is made up in large part of abducted children led by the self-proclaimed prophet Joseph Kony, who says he wants Uganda to live by the laws of the Ten Commandments; she is allegedly extorting President Museveni and his SOS wife into attacking civilians to promote ethnic strife; she was allegedly awarded a Master of Arts in Applied Sciences by Simon Fraser University for her work with Greek Life media in the manipulation of financial markets; she is an alleged extortionist on the board of the Positive Women’s Network and Pacific AIDS Resource Centre (PARC); we alleged that she is accessory before or after the fact to the filmed contract killing of Wendy Ladner Beaudry who threatened to expose the Greek Life cannibal cult; she is the alleged extortionist Chair of the Unite for Children, Unite Against AIDS campaign for UNICEF Canada; she alleged extortionist appointee to the John F. Kennedy School of Government Women’s Leadership Board at Harvard University; she is an alleged extortionist member of the UBC Graduate School of Journalism Advisory Board]”
 75. Jill Glazer (nee Henkin) “[Matrix 5 wife of allegedly extorted man-in-the-middle Avie Glazer who is a graduate of Washington University in St. Louis, a director/owner of the Manchester United Football Club and a sponsor of post-Katrina repairs (?) to the Tulane University campus; she pledged Sigma Delta Tau (SDT) sorority in 1981 at Newcomb College, Tulane; she majored in sociology and graduated in 1985 with a bachelor’s degree; she allegedly used her Nikon camera as the chapter’s unofficial photographer to record cannibal oath-taking ceremonies and extort orientation leaders and officers in SDT; in 1985 she moved to New York City where she met her future husband Avie Glazer; she now splits her time between Rochester, NY, New Orleans and Palm Beach, Fla.; she is a civic leader and alleged Greek Life extortionist of top officials in many religious and educational organizations; she is a former executive board member and vice president of the fundraising committee for the Hillel Community Day School in Rochester; she is a member of the development, auction and corporate sponsor committees for Palm Beach Day Academy, as well as a trustee of the school; she is a member of the Tulane Board of Administrators, to which she was appointed in 2009; she is a current member of the Tulane Parents Council; she is a past member of the Tulane President’s Council and former chair of the Alumni Admissions Committee; she allegedly extorted her husband into funding her alma mater’s post-Katrina campus beautification; she allegedly extorted the donation of trees for the Gibson and Monroe quads and Gibson Circle, the construction of the Newcomb Pottery Garden and the new garden and bocce court that bears the Glazer name across from the Alumni House on Willow Street; she was the co-chair for the 2009 Hullabaloo Homecoming Auction where she allegedly extorted close to $250,000, an almost-tenfold increase from the previous year, for Tulane’s student athletes; she allegedly extorted American banking giant AIG through a cannibal hedge fund pack to loan finance the Glazer’s takeover of Manchester United; she allegedly extorted AIG into a new shirt-sponsorship scheme in a record £56.5million deal; she allegedly worked with Elisabeth Murdoch to extort an increase in “battering ram” revenue from Video-Guard pay-per-view TV rights to each competition in which the club participates; she allegedly extorted a boost to the club’s profitability with a Nike apparel deal; she allegedly used a cannibal Greek hedge fund pack to set up a catastrophe bond fraud where the New Orleans levee system was sabotaged in events which triggered a class action suit against AIG by policyholders represented through the attorney, Ray Orrill; she allegedly used a cannibal Greek hedge fund managers to extort Obama administration officials to add language to a crony federal-stimulus bill which ensures AIG and hedge fund bonuses remained in place; she allegedly used a cannibal hedge fund pack to extort the departure of two top Old Trafford executives – Finance director Nick Humby and commercial boss Andy Anson – which left the Glazer family in complete charge of the club and isolated its chief executive, David Gill; she allegedly helped Elisabeth Murdoch to set up News of the World journalists and editors as decoys for the activities of cannibal Greek hedge fund managers and obtain the conviction of NOTW royal editor Clive Goodman and Glenn Mulcaire in 2007; she allegedly helped Elisabeth Murdoch to hack the mobile phone of Manchester United footballer Ryan Giggs; she allegedly used a cannibal Greek hedge-fund pack built by Sidley Austin alumni Bernardine ‘Torture: Paradigms and Practise’ Dohrn and Michelle and Barack Obama, to set up Directors and Officers (D&O) Liability and Insurance frauds on AIG directors and shareholders at a meeting on Friday, January 30, 2009 at the AXA Equitable Life headquarters 787 Seventh Avenue New York, New York; she allegedly knew that this was the address where AXA Equitable, AIG and Women @ Sidley paid blood and hush money to the victims of Matrix 5 man-in-the-middle attacks on NYC’s World Trade Center, allegedly staged and synchronized by the late Cannibal Greek General Alexander Haig in a snuff film tentatively en-titled ‘Triphibious 9/11’.]”
75. Jill Glazer (nee Henkin) “[Matrix 5 wife of allegedly extorted man-in-the-middle Avie Glazer who is a graduate of Washington University in St. Louis, a director/owner of the Manchester United Football Club and a sponsor of post-Katrina repairs (?) to the Tulane University campus; she pledged Sigma Delta Tau (SDT) sorority in 1981 at Newcomb College, Tulane; she majored in sociology and graduated in 1985 with a bachelor’s degree; she allegedly used her Nikon camera as the chapter’s unofficial photographer to record cannibal oath-taking ceremonies and extort orientation leaders and officers in SDT; in 1985 she moved to New York City where she met her future husband Avie Glazer; she now splits her time between Rochester, NY, New Orleans and Palm Beach, Fla.; she is a civic leader and alleged Greek Life extortionist of top officials in many religious and educational organizations; she is a former executive board member and vice president of the fundraising committee for the Hillel Community Day School in Rochester; she is a member of the development, auction and corporate sponsor committees for Palm Beach Day Academy, as well as a trustee of the school; she is a member of the Tulane Board of Administrators, to which she was appointed in 2009; she is a current member of the Tulane Parents Council; she is a past member of the Tulane President’s Council and former chair of the Alumni Admissions Committee; she allegedly extorted her husband into funding her alma mater’s post-Katrina campus beautification; she allegedly extorted the donation of trees for the Gibson and Monroe quads and Gibson Circle, the construction of the Newcomb Pottery Garden and the new garden and bocce court that bears the Glazer name across from the Alumni House on Willow Street; she was the co-chair for the 2009 Hullabaloo Homecoming Auction where she allegedly extorted close to $250,000, an almost-tenfold increase from the previous year, for Tulane’s student athletes; she allegedly extorted American banking giant AIG through a cannibal hedge fund pack to loan finance the Glazer’s takeover of Manchester United; she allegedly extorted AIG into a new shirt-sponsorship scheme in a record £56.5million deal; she allegedly worked with Elisabeth Murdoch to extort an increase in “battering ram” revenue from Video-Guard pay-per-view TV rights to each competition in which the club participates; she allegedly extorted a boost to the club’s profitability with a Nike apparel deal; she allegedly used a cannibal Greek hedge fund pack to set up a catastrophe bond fraud where the New Orleans levee system was sabotaged in events which triggered a class action suit against AIG by policyholders represented through the attorney, Ray Orrill; she allegedly used a cannibal Greek hedge fund managers to extort Obama administration officials to add language to a crony federal-stimulus bill which ensures AIG and hedge fund bonuses remained in place; she allegedly used a cannibal hedge fund pack to extort the departure of two top Old Trafford executives – Finance director Nick Humby and commercial boss Andy Anson – which left the Glazer family in complete charge of the club and isolated its chief executive, David Gill; she allegedly helped Elisabeth Murdoch to set up News of the World journalists and editors as decoys for the activities of cannibal Greek hedge fund managers and obtain the conviction of NOTW royal editor Clive Goodman and Glenn Mulcaire in 2007; she allegedly helped Elisabeth Murdoch to hack the mobile phone of Manchester United footballer Ryan Giggs; she allegedly used a cannibal Greek hedge-fund pack built by Sidley Austin alumni Bernardine ‘Torture: Paradigms and Practise’ Dohrn and Michelle and Barack Obama, to set up Directors and Officers (D&O) Liability and Insurance frauds on AIG directors and shareholders at a meeting on Friday, January 30, 2009 at the AXA Equitable Life headquarters 787 Seventh Avenue New York, New York; she allegedly knew that this was the address where AXA Equitable, AIG and Women @ Sidley paid blood and hush money to the victims of Matrix 5 man-in-the-middle attacks on NYC’s World Trade Center, allegedly staged and synchronized by the late Cannibal Greek General Alexander Haig in a snuff film tentatively en-titled ‘Triphibious 9/11’.]”
 76. Greta Van Susteren (born June 11, 1954) “[Revised October 25, 2011. Matrix 5 principal and wife (m. 1988) of allegedly extorted man-in-the-middle, John P. ‘Bhopal’ Coale; she allegedly conspired with Greek Life associates Lynne Cheney (Kappa Alpha Theta) and Condoleezza Rice (Alpha Chi Omega) to gave General Henry Shelton an alibi for 9/11; she is allegedly using CNN In-Flight Network to conceal the name of the root authority behind Pershing Rifles and the Queens’ Guard in the Matrix 5 propaganda attack of 9/11; she allegedly used Femme Comp Greeks to extort control of the Department of Defense’s Mentor/Protégé Program; she allegedly hired Femme Comp Greeks to prepare a pay-per-view production of the live-broadcast snuff film ‘Triphibious 9/11’; she allegedly uses Greeks to launch Matrix 5 propaganda attacks with Delta Phi Epsilon (a professional foreign service fraternity founded at Georgetown in 1920) and its sorority (founded in 1973); she and her Greek Life associates were allegedly tricked (?) into swearing Aleister Crowley-designed oaths near ‘Bullingdon toilet bowls’; she is allegedly aware that such toilet bowls were set up for Matrix 5 camera crews at Hull House in Chicago and Toynbee Hall in Whitechapel – the latter being cleaned by the late Bullingdon Dining Club alumnus John Profumo, before the murder of U.S. President John F. Kennedy in 1963; Abel Danger makes a spoliation inference from her use of VideoGuard pay-per-view encryption to spoliate evidence and testimony from oath-taker controlled crime scenes that Greta Van Susteren is guilty as an accessory – before or after the fact – of the crimes which she has allegedly spoliated; she allegedly launched Femme Comp Inc. in 1979 with fellow Georgetown alumna Kristine Marcy (see #1) to operate as women-owned SBA small business engaged in murder-for-hire for the former Treasury Solicitor Juliet Wheldon (see bookend); we infer that she and her husband operate a racketeering tort-law partnership at Femme Comp’s FC-KU (Ku band) crime scenes in which he serves as the self-described “ambulance chaser” who became known as “Bhopal Coale” in 1984 being the first lawyer to hop on a plane to India to sign up gas-leak victims who couldn’t even read their retainer documents; she graduated from Xavier High School in Appleton in 1972 and the University of Wisconsin in Madison in 1976, where she studied geography and economics; she earned a Juris Doctor from Georgetown Law in 1979 and a Master of Law from the school in 1982; she was the first Stuart Stiller Fellow at Georgetown Law Center; she was an adjunct professor at the Law Center from 1984 through 1999; she allegedly used Femme Comp Greeks to hire false witnesses to accuse the innocent and shelter those people guilty of the coordinated sabotage of Union Carbide’s insecticide plant in India; she allegedly procured IFN devices for Femme Comp Greeks to trigger dial-a-blast bombs and encrypt fake images during a Matrix 5 propaganda attack on New Orleans where false witnesses attributed failures in the levee system to a 20’ surge from a day-old Hurricane Katrina; she allegedly procured IFN pay-per-view and VideoGuard-encrypted snuff-film devices for Greek Life extortionists at Rockwell Collins; she allegedly moved Femme Comp’s Greek Life extortionists through ‘diversity’ backdoors built by Rockwell Collins to control the National Society of Black Engineers (NSBE), the Society of Women Engineers (SWE), the North Carolina Agricultural and Technical State University (where she recruited Khalid Sheikh Mohammed) and Tuskegee University; she allegedly extorted her husband to sue his tailor, on the grounds that the sub-par work on his shirts had subjected him to “public humiliation . . . severe emotional distress, and embarrassment; she allegedly used FC Greeks to extort the West Virginia Bar into dropping attempts to disbar both her husband and herself for soliciting the families of coal-mine accident victims; she allegedly transmitted death threats through FC Greeks and her husband – then serving as an adviser to Sarah Palin – to force the non-Greek candidate out of the running for the Republican presidential primary campaign; she allegedly deploys FC Greek extortionists to control the Church of Scientology; she is a former criminal defense and civil trial lawyer and joined CNN in 1991 as a legal analyst to become co-host of CNN’s Burden of Proof and The Point with Roger Cossack from 1994 to 2002, playing defense attorney to Cossack’s prosecutor; she joined Fox News Channel after a highly publicized and phony contract-bidding war; she now hosts On the Record w/ Greta Van Susteren on the Fox News Channel; she utilized cosmetic surgery to manipulate public perception of her untrustworthiness; her Fox News “On the Record” is the highest rated cable news program in the 10 p.m. timeslot; she is allegedly using Femme Comp’s Greek Life extortionists to spoliate crime scenes and smear expert witnesses in Daubert defense ploys designed to ensure that prosecutors, jurors and investigators can rarely if ever establish guilt or meet the burden of proof beyond a reasonable doubt; she allegdly used FC Greeks with Kristine Marcy to generate false witness at crimes scenes or trials associated with the Waco Massacre, the murder of Vince Foster, the Murrah Building Bomb, JonBenet Ramsey, O.J. Simpson, the Elian Gonzalez custody battle, the frauds associated with Election 2000, the bombing of the USS Cole, Caylee Marie Anthony, Scott Peterson, Michael Jackson, Anna Nicole Smith, the disappearance of Natalee Holloway from Aruba; the Virginia Tech massacre where a suicide note in suspect Cho’s dorm room indicates he was entrapped by Femme Comp Greeks into “rich kids”, “debauchery”, and “deceitful charlatans” and where he alleges “You forced me into a corner and gave me only one option…You just loved to crucify me. You loved inducing cancer in my head, terror in my heart and ripping my soul all this time”; she has represented various clients in civil and criminal cases during her career as a trial attorney; she is the author of a chapter on witness and client representation in “Federal Enforcement 1992: Defense Strategies for Winning White Collar Trial.”; she was awarded the first place 2002 National Headliners Award as part of an investigative team covering the “Attack on America.”; she allegedly continues to divert public perception of ongoing treasonous acts by her Greek Life associates at Femme Comp Inc and she is preparing to place Gloria Cain and her Ballistics 9/11 husband in the White House as loyal servants of the Treasury Solicitor, the Queens’ Guard and the Bullingdon Toilet Bowl”
76. Greta Van Susteren (born June 11, 1954) “[Revised October 25, 2011. Matrix 5 principal and wife (m. 1988) of allegedly extorted man-in-the-middle, John P. ‘Bhopal’ Coale; she allegedly conspired with Greek Life associates Lynne Cheney (Kappa Alpha Theta) and Condoleezza Rice (Alpha Chi Omega) to gave General Henry Shelton an alibi for 9/11; she is allegedly using CNN In-Flight Network to conceal the name of the root authority behind Pershing Rifles and the Queens’ Guard in the Matrix 5 propaganda attack of 9/11; she allegedly used Femme Comp Greeks to extort control of the Department of Defense’s Mentor/Protégé Program; she allegedly hired Femme Comp Greeks to prepare a pay-per-view production of the live-broadcast snuff film ‘Triphibious 9/11’; she allegedly uses Greeks to launch Matrix 5 propaganda attacks with Delta Phi Epsilon (a professional foreign service fraternity founded at Georgetown in 1920) and its sorority (founded in 1973); she and her Greek Life associates were allegedly tricked (?) into swearing Aleister Crowley-designed oaths near ‘Bullingdon toilet bowls’; she is allegedly aware that such toilet bowls were set up for Matrix 5 camera crews at Hull House in Chicago and Toynbee Hall in Whitechapel – the latter being cleaned by the late Bullingdon Dining Club alumnus John Profumo, before the murder of U.S. President John F. Kennedy in 1963; Abel Danger makes a spoliation inference from her use of VideoGuard pay-per-view encryption to spoliate evidence and testimony from oath-taker controlled crime scenes that Greta Van Susteren is guilty as an accessory – before or after the fact – of the crimes which she has allegedly spoliated; she allegedly launched Femme Comp Inc. in 1979 with fellow Georgetown alumna Kristine Marcy (see #1) to operate as women-owned SBA small business engaged in murder-for-hire for the former Treasury Solicitor Juliet Wheldon (see bookend); we infer that she and her husband operate a racketeering tort-law partnership at Femme Comp’s FC-KU (Ku band) crime scenes in which he serves as the self-described “ambulance chaser” who became known as “Bhopal Coale” in 1984 being the first lawyer to hop on a plane to India to sign up gas-leak victims who couldn’t even read their retainer documents; she graduated from Xavier High School in Appleton in 1972 and the University of Wisconsin in Madison in 1976, where she studied geography and economics; she earned a Juris Doctor from Georgetown Law in 1979 and a Master of Law from the school in 1982; she was the first Stuart Stiller Fellow at Georgetown Law Center; she was an adjunct professor at the Law Center from 1984 through 1999; she allegedly used Femme Comp Greeks to hire false witnesses to accuse the innocent and shelter those people guilty of the coordinated sabotage of Union Carbide’s insecticide plant in India; she allegedly procured IFN devices for Femme Comp Greeks to trigger dial-a-blast bombs and encrypt fake images during a Matrix 5 propaganda attack on New Orleans where false witnesses attributed failures in the levee system to a 20’ surge from a day-old Hurricane Katrina; she allegedly procured IFN pay-per-view and VideoGuard-encrypted snuff-film devices for Greek Life extortionists at Rockwell Collins; she allegedly moved Femme Comp’s Greek Life extortionists through ‘diversity’ backdoors built by Rockwell Collins to control the National Society of Black Engineers (NSBE), the Society of Women Engineers (SWE), the North Carolina Agricultural and Technical State University (where she recruited Khalid Sheikh Mohammed) and Tuskegee University; she allegedly extorted her husband to sue his tailor, on the grounds that the sub-par work on his shirts had subjected him to “public humiliation . . . severe emotional distress, and embarrassment; she allegedly used FC Greeks to extort the West Virginia Bar into dropping attempts to disbar both her husband and herself for soliciting the families of coal-mine accident victims; she allegedly transmitted death threats through FC Greeks and her husband – then serving as an adviser to Sarah Palin – to force the non-Greek candidate out of the running for the Republican presidential primary campaign; she allegedly deploys FC Greek extortionists to control the Church of Scientology; she is a former criminal defense and civil trial lawyer and joined CNN in 1991 as a legal analyst to become co-host of CNN’s Burden of Proof and The Point with Roger Cossack from 1994 to 2002, playing defense attorney to Cossack’s prosecutor; she joined Fox News Channel after a highly publicized and phony contract-bidding war; she now hosts On the Record w/ Greta Van Susteren on the Fox News Channel; she utilized cosmetic surgery to manipulate public perception of her untrustworthiness; her Fox News “On the Record” is the highest rated cable news program in the 10 p.m. timeslot; she is allegedly using Femme Comp’s Greek Life extortionists to spoliate crime scenes and smear expert witnesses in Daubert defense ploys designed to ensure that prosecutors, jurors and investigators can rarely if ever establish guilt or meet the burden of proof beyond a reasonable doubt; she allegdly used FC Greeks with Kristine Marcy to generate false witness at crimes scenes or trials associated with the Waco Massacre, the murder of Vince Foster, the Murrah Building Bomb, JonBenet Ramsey, O.J. Simpson, the Elian Gonzalez custody battle, the frauds associated with Election 2000, the bombing of the USS Cole, Caylee Marie Anthony, Scott Peterson, Michael Jackson, Anna Nicole Smith, the disappearance of Natalee Holloway from Aruba; the Virginia Tech massacre where a suicide note in suspect Cho’s dorm room indicates he was entrapped by Femme Comp Greeks into “rich kids”, “debauchery”, and “deceitful charlatans” and where he alleges “You forced me into a corner and gave me only one option…You just loved to crucify me. You loved inducing cancer in my head, terror in my heart and ripping my soul all this time”; she has represented various clients in civil and criminal cases during her career as a trial attorney; she is the author of a chapter on witness and client representation in “Federal Enforcement 1992: Defense Strategies for Winning White Collar Trial.”; she was awarded the first place 2002 National Headliners Award as part of an investigative team covering the “Attack on America.”; she allegedly continues to divert public perception of ongoing treasonous acts by her Greek Life associates at Femme Comp Inc and she is preparing to place Gloria Cain and her Ballistics 9/11 husband in the White House as loyal servants of the Treasury Solicitor, the Queens’ Guard and the Bullingdon Toilet Bowl”
 77. Jane Garvey (née Famiano) “[Matrix 5 principal and former boss of allegedly extorted man-in-the-middle top officials in the U.S. Federal Aviation Administration from 1997 to 2002; she has a B.A. from Mount Saint Mary College and an M.A. from Mount Holyoke College; she was appointed by President Bill Clinton on the orders of Hillary Clinton, as an FAA Administrator; Hillary Clinton chose her because she was the first Administrator who was not a licensed pilot and could therefore offer her plausible denial for the upcoming costume swap with the QRS11 missile gyroscopes which she believed would disguise the source of the planned attack on America; she passed off the management of U.S. air space to FAA Contract Towers saboteurs embedded in the Guild of Rippergate Serco companies controlled by John (Jack the Dipper) Profumo at Toynbee Hall with no security clearance; she was the former director of Logan International Airport where she allegedly re-arranged security clearances to permit Mohammed Atta to board the plane on 9/11; she sent key FAA staff to be out of Herndon on 9/11 so that alerts to NMCC and Rumsfeld in the Pentagon could be disrupted by General Henry Shelton using phony PKI authorities from the Speckled Trout; she sent Jack Kies, FAA’s manager of tactical operations, in Nashua, New Hampshire, to meet with Canadian air traffic controllers to coordinate decoy and drone attacks with software developed for the Speckled Trout by Macdonald Dettwiler and Associates of Richmond, B.C. – the BC OnLine data company which organized the mortgage on the pig farm used to host Greek Life cannibal oath ceremonies; she placed Linda Schuessler, as deputy director of system operations in the FAA Command Center in Herndon, Virginia; she set up an alibi with Mineta at a breakfast meeting at the Department of Transportation, in Washington, DC, and helped Shelton in the Speckled Trout to isolate President Bush in Sarasota, Florida, by jamming signals to the secure phone in his vehicle in the motorcade when the first WTC attack occured; she switched communication re the hijacking to the Speckled Trout’s I-FN links to the pay-per-view snuff film services of Murdoch’s Fox News; she arrived at her office at FAA headquarters in Washington, DC to find Monte Belger, her acting deputy, there; she headed across the hall to the Operations Center to set up a “hijacking net”—a teleconference that includes several agencies, including the Defense Department, and the General Shelton in the Speckled Trout; she intercepted info which should have been going to NMCC and Rumsfeld; she routed the Speckled Trout links live direct to Richard Clarke in the Secure Video Conferencing Center just off the main floor of the Situation Room in the West Wing of the White House; she and SES Clarke disrupted feeds to Cheney, Rumsfeld and Bush from the E4B over Washington in a costume swap with the Speckled Trout; she initiated a national ground stop, which forbids takeoffs and prevents military or law enforcement aircraft from checking who was attacking America; she allowed the Speckled Trout radome-controlled drones to look for more high value targets; she allowed Kristine Marcy’s Con Air to continue flying to create al-Qaeda decoys; she used Speckled Trout to authorize Linda Schuessler, the manager of tactical operations at the FAA Command Center, and various treasonous members of the Senior Executive Service to land about 500 planes in 20 minutes; she instructed SES Stephen Browning, the director of military and technical services for the Army Corps of Engineers, to clean up evidence of use of costume swap to conceal role of Speckled Trout in hijacking decoy and drone maneuvers at Ground Zero; she messaged through to the Office of Personnel Management Director Kay Coles James to tell senior executives to keep their mouths shut or risk exposure of Rippergate oath-taking info in their files; she set up FAA National Operations Manager Ben Sliney as a patsy for the order to shut down the entire nationwide air traffic system; she set up Leo Mullin, the CEO of Delta Air Lines, by jamming transponders on four Delta aircraft; she used the Speckled Trout to divert all international flights with US destinations to Canada to strip out Speckled Trout network-centric warfare devices developed by MDA in Richmond, B.C.; she continued to feed bogus information to POTUS 43 with claim that a plane had disappeared from radar and might have crashed in Kentucky; she concealed murder for hire use of Speckled Trout with a Rippergate costume swap for the crew of an E-4B which had participated in Amalgam Virgo exercise on June 1-2, 2001; she is an alleged principal in a Jane the Ripper conspiracy with Kristine Marcy’s SBA mentor-protégée teams which used General Shelton’s Speckled Trout as a costume-swapping command post to overthrow the U.S. government by force on 9/11.]”
77. Jane Garvey (née Famiano) “[Matrix 5 principal and former boss of allegedly extorted man-in-the-middle top officials in the U.S. Federal Aviation Administration from 1997 to 2002; she has a B.A. from Mount Saint Mary College and an M.A. from Mount Holyoke College; she was appointed by President Bill Clinton on the orders of Hillary Clinton, as an FAA Administrator; Hillary Clinton chose her because she was the first Administrator who was not a licensed pilot and could therefore offer her plausible denial for the upcoming costume swap with the QRS11 missile gyroscopes which she believed would disguise the source of the planned attack on America; she passed off the management of U.S. air space to FAA Contract Towers saboteurs embedded in the Guild of Rippergate Serco companies controlled by John (Jack the Dipper) Profumo at Toynbee Hall with no security clearance; she was the former director of Logan International Airport where she allegedly re-arranged security clearances to permit Mohammed Atta to board the plane on 9/11; she sent key FAA staff to be out of Herndon on 9/11 so that alerts to NMCC and Rumsfeld in the Pentagon could be disrupted by General Henry Shelton using phony PKI authorities from the Speckled Trout; she sent Jack Kies, FAA’s manager of tactical operations, in Nashua, New Hampshire, to meet with Canadian air traffic controllers to coordinate decoy and drone attacks with software developed for the Speckled Trout by Macdonald Dettwiler and Associates of Richmond, B.C. – the BC OnLine data company which organized the mortgage on the pig farm used to host Greek Life cannibal oath ceremonies; she placed Linda Schuessler, as deputy director of system operations in the FAA Command Center in Herndon, Virginia; she set up an alibi with Mineta at a breakfast meeting at the Department of Transportation, in Washington, DC, and helped Shelton in the Speckled Trout to isolate President Bush in Sarasota, Florida, by jamming signals to the secure phone in his vehicle in the motorcade when the first WTC attack occured; she switched communication re the hijacking to the Speckled Trout’s I-FN links to the pay-per-view snuff film services of Murdoch’s Fox News; she arrived at her office at FAA headquarters in Washington, DC to find Monte Belger, her acting deputy, there; she headed across the hall to the Operations Center to set up a “hijacking net”—a teleconference that includes several agencies, including the Defense Department, and the General Shelton in the Speckled Trout; she intercepted info which should have been going to NMCC and Rumsfeld; she routed the Speckled Trout links live direct to Richard Clarke in the Secure Video Conferencing Center just off the main floor of the Situation Room in the West Wing of the White House; she and SES Clarke disrupted feeds to Cheney, Rumsfeld and Bush from the E4B over Washington in a costume swap with the Speckled Trout; she initiated a national ground stop, which forbids takeoffs and prevents military or law enforcement aircraft from checking who was attacking America; she allowed the Speckled Trout radome-controlled drones to look for more high value targets; she allowed Kristine Marcy’s Con Air to continue flying to create al-Qaeda decoys; she used Speckled Trout to authorize Linda Schuessler, the manager of tactical operations at the FAA Command Center, and various treasonous members of the Senior Executive Service to land about 500 planes in 20 minutes; she instructed SES Stephen Browning, the director of military and technical services for the Army Corps of Engineers, to clean up evidence of use of costume swap to conceal role of Speckled Trout in hijacking decoy and drone maneuvers at Ground Zero; she messaged through to the Office of Personnel Management Director Kay Coles James to tell senior executives to keep their mouths shut or risk exposure of Rippergate oath-taking info in their files; she set up FAA National Operations Manager Ben Sliney as a patsy for the order to shut down the entire nationwide air traffic system; she set up Leo Mullin, the CEO of Delta Air Lines, by jamming transponders on four Delta aircraft; she used the Speckled Trout to divert all international flights with US destinations to Canada to strip out Speckled Trout network-centric warfare devices developed by MDA in Richmond, B.C.; she continued to feed bogus information to POTUS 43 with claim that a plane had disappeared from radar and might have crashed in Kentucky; she concealed murder for hire use of Speckled Trout with a Rippergate costume swap for the crew of an E-4B which had participated in Amalgam Virgo exercise on June 1-2, 2001; she is an alleged principal in a Jane the Ripper conspiracy with Kristine Marcy’s SBA mentor-protégée teams which used General Shelton’s Speckled Trout as a costume-swapping command post to overthrow the U.S. government by force on 9/11.]”
 78. Virginia Fortune Ogilvy, Countess of Airlie “[Matrix 5 principal and Lady of the Bedchamber since 1973 to an allegedly-extorted woman-in-the-middle, Queen Elizabeth II whom she attends on major occasions and overseas tours; on 23 October 1952, she married an allegedly-extorted David Ogilvy, who in 1968 became Earl of Airlie; he is the 8th (or 13th) Earl of Airlie and the eldest son of David Ogilvy, 7th (or 12th) Earl of Airlie and Lady Alexandra Coke; David Ogilvy was born in London, educated at Eton, and served in the Scots Guards during the Second World War; he remained in the army until 1950, when he attended the Royal Agricultural College in Cirencester, in order to learn more about estate management; she maintains two homes on the family’s 69, 000 acre (280 km²) estate in Angus: Cortachy Castle and Airlie Castle and a home in Chelsea, London; she was a presumed associate of the late Jack Profumo, the former Bullingdon Club Secretary for War who allegedly developed a Star Chamber strategy with Airlie for the MitM attack on America of 9/11; she is the daughter of John Barry Ryan, an American multi-millionaire, and Margaret, daughter of financier Otto Kahn; David Ogilvy took up merchant banking, joining J. Henry Schroder in 1953 where he was appointed a director of the company in 1961 and chairman in 1973; she allegedly forced her husband to resign from Schroders and engineered his appointment as Lord Chamberlain in 1984 where he allegedly tricked Queen Elizabeth II into handing over an ultra vires ‘Star Chamber’ authority to run HMG as his wife’s and her Crown Agents Sisters’ personal fiefdom; David Ogilvy’s late father was appointed Lord Chamberlain to Queen Elizabeth, the Queen Mother, in 1937 where he allegedly provided backdoor intelligence to Nazi sympathizers in the court of the former Bullingdon Club alumnus, the late King Edward VIII; she allegedly arranged for David Ogilvy to remain in his Lord Chamberlain’s post until 1997 to authorize the infiltration of LGBT agents into GCHQ, the adoption of Clipper PKI for MitM propaganda and the privatization of Crown Agents to support the Star Chamber attacks on the USS Cole in Aden Harbour and the American government on 9/11; in 1997 she arranged for the appointment of Richard Luce as Lord Chamberlain; she allegedly placed Luce in the unlawful Star Chamber and forced him to adopt Clipper encryption technologies needed to conceal the staging of the ‘first live broadcast mass snuff film in human history’ on 9/11 and the demolition of WYC#7; in May 2007, she accompanied Queen Elizabeth II on her trip to the United States to commemorate the 400th anniversary of England’s first American settlement at Jamestown, Virginia and attended a state dinner at the White House, hosted by President George W. Bush and Mrs. Bush.]”
78. Virginia Fortune Ogilvy, Countess of Airlie “[Matrix 5 principal and Lady of the Bedchamber since 1973 to an allegedly-extorted woman-in-the-middle, Queen Elizabeth II whom she attends on major occasions and overseas tours; on 23 October 1952, she married an allegedly-extorted David Ogilvy, who in 1968 became Earl of Airlie; he is the 8th (or 13th) Earl of Airlie and the eldest son of David Ogilvy, 7th (or 12th) Earl of Airlie and Lady Alexandra Coke; David Ogilvy was born in London, educated at Eton, and served in the Scots Guards during the Second World War; he remained in the army until 1950, when he attended the Royal Agricultural College in Cirencester, in order to learn more about estate management; she maintains two homes on the family’s 69, 000 acre (280 km²) estate in Angus: Cortachy Castle and Airlie Castle and a home in Chelsea, London; she was a presumed associate of the late Jack Profumo, the former Bullingdon Club Secretary for War who allegedly developed a Star Chamber strategy with Airlie for the MitM attack on America of 9/11; she is the daughter of John Barry Ryan, an American multi-millionaire, and Margaret, daughter of financier Otto Kahn; David Ogilvy took up merchant banking, joining J. Henry Schroder in 1953 where he was appointed a director of the company in 1961 and chairman in 1973; she allegedly forced her husband to resign from Schroders and engineered his appointment as Lord Chamberlain in 1984 where he allegedly tricked Queen Elizabeth II into handing over an ultra vires ‘Star Chamber’ authority to run HMG as his wife’s and her Crown Agents Sisters’ personal fiefdom; David Ogilvy’s late father was appointed Lord Chamberlain to Queen Elizabeth, the Queen Mother, in 1937 where he allegedly provided backdoor intelligence to Nazi sympathizers in the court of the former Bullingdon Club alumnus, the late King Edward VIII; she allegedly arranged for David Ogilvy to remain in his Lord Chamberlain’s post until 1997 to authorize the infiltration of LGBT agents into GCHQ, the adoption of Clipper PKI for MitM propaganda and the privatization of Crown Agents to support the Star Chamber attacks on the USS Cole in Aden Harbour and the American government on 9/11; in 1997 she arranged for the appointment of Richard Luce as Lord Chamberlain; she allegedly placed Luce in the unlawful Star Chamber and forced him to adopt Clipper encryption technologies needed to conceal the staging of the ‘first live broadcast mass snuff film in human history’ on 9/11 and the demolition of WYC#7; in May 2007, she accompanied Queen Elizabeth II on her trip to the United States to commemorate the 400th anniversary of England’s first American settlement at Jamestown, Virginia and attended a state dinner at the White House, hosted by President George W. Bush and Mrs. Bush.]”
_tracy-mcvicar_(cai-capital-management).jpg) 79. Tracey McVicar “[Matrix 5 principal and manager of 50+ allegedly-extorted man-in-the-middle Special Investors in, or consultants to, the CAI Private Equity Group who held erstwhile equity positions in MacDonald, Dettwiler and Associates Ltd. (“MDA”); she hired David Emerson in November 2008 as CAI “senior advisor” at the equity firm’s Vancouver office when she knew or ought to have known that he was a longstanding investor in CAI and the alleged cestui que murder-for-hire services of MDA; in her early twenties, in 1990, McVicar earned a bachelor’s degree in finance from UBC where she allegedly swore a cannibal oath of lifetime loyalty and obedience to Greek Life sororities corruptly associated with the Vancouver Settlement Movement; she appears to have placed Emerson, then CEO at Bentley’s Canfor, on the board of MacDonald Dettwiler in August 2001 in an alleged attempt to compromise him through MDA’s alleged use of Clipper in MitM propaganda communications on 9/11; In 1999, CAI bought a position in MacDonald Dettwiler and Associates and placed Brooklyn-based Peter Restler, a founding CAI partner on the MDA board; CAI was founded in 1989 by seven investors, including a couple of ex-Salomon Brothers partners in New York who would allegedly go on to equip the Schroders Salomon Smith Barney offices in WTC#7 with Clipper encryption devices to support insider and outsider trading, churning and pump-and-dump frauds; in 1999, CAI bought a position in MacDonald Dettwiler and Associates and placed Brooklyn-based Peter Restler, a founding CAI partner on the MDA board; she allegedly placed Emerson in July 2010 on the board of Postmedia Network Inc. – owner of many B.C. dailies – to ‘manage’ pig farm stories appearing in the Vancouver Sun, The Province and the Times Colonist; she traveled in the summer of 2001 to work for a couple of months with disadvantaged children in Mott Haven, said to be the poorest neighborhood in New York’s South Bronx; during those two months, she allegedly procured Clipper encryption devices through MDA’s PKI program to equip saboteurs and assassins embedded in New York’s Settlement Movement with the secure PCDs (Nokia?) needed to synchronize spin and spoliation of evidence at the 9/11 crime scenes; she joined investment banking division at RBC Dominion Securities where Larry Blain was her allegedly-extorted boss; she left to join a Vancouver-based brokerage, Goepel, Shields and Partners; by 1997, she had become a partner at the firm and a member of its board of directors; in 2003, she left to head up the Vancouver office of CAI Capital Management Ltd.; she allegedly used CAI Clipper encryption devices to allow insiders to mount MitM attacks on targets such as Nortel; she allegedly extorted a gig with the board of directors at BC Hydro in December 2007; she allegedly extorted Larry Blain and fellow directors of BC Hydro into awarding the $73 million BC Hydro smart-grid contract to Corix Utilities, part of the Corix Group of Companies in which one of the biggest shareholders is CAI Capital Management where she is the managing director!]”
79. Tracey McVicar “[Matrix 5 principal and manager of 50+ allegedly-extorted man-in-the-middle Special Investors in, or consultants to, the CAI Private Equity Group who held erstwhile equity positions in MacDonald, Dettwiler and Associates Ltd. (“MDA”); she hired David Emerson in November 2008 as CAI “senior advisor” at the equity firm’s Vancouver office when she knew or ought to have known that he was a longstanding investor in CAI and the alleged cestui que murder-for-hire services of MDA; in her early twenties, in 1990, McVicar earned a bachelor’s degree in finance from UBC where she allegedly swore a cannibal oath of lifetime loyalty and obedience to Greek Life sororities corruptly associated with the Vancouver Settlement Movement; she appears to have placed Emerson, then CEO at Bentley’s Canfor, on the board of MacDonald Dettwiler in August 2001 in an alleged attempt to compromise him through MDA’s alleged use of Clipper in MitM propaganda communications on 9/11; In 1999, CAI bought a position in MacDonald Dettwiler and Associates and placed Brooklyn-based Peter Restler, a founding CAI partner on the MDA board; CAI was founded in 1989 by seven investors, including a couple of ex-Salomon Brothers partners in New York who would allegedly go on to equip the Schroders Salomon Smith Barney offices in WTC#7 with Clipper encryption devices to support insider and outsider trading, churning and pump-and-dump frauds; in 1999, CAI bought a position in MacDonald Dettwiler and Associates and placed Brooklyn-based Peter Restler, a founding CAI partner on the MDA board; she allegedly placed Emerson in July 2010 on the board of Postmedia Network Inc. – owner of many B.C. dailies – to ‘manage’ pig farm stories appearing in the Vancouver Sun, The Province and the Times Colonist; she traveled in the summer of 2001 to work for a couple of months with disadvantaged children in Mott Haven, said to be the poorest neighborhood in New York’s South Bronx; during those two months, she allegedly procured Clipper encryption devices through MDA’s PKI program to equip saboteurs and assassins embedded in New York’s Settlement Movement with the secure PCDs (Nokia?) needed to synchronize spin and spoliation of evidence at the 9/11 crime scenes; she joined investment banking division at RBC Dominion Securities where Larry Blain was her allegedly-extorted boss; she left to join a Vancouver-based brokerage, Goepel, Shields and Partners; by 1997, she had become a partner at the firm and a member of its board of directors; in 2003, she left to head up the Vancouver office of CAI Capital Management Ltd.; she allegedly used CAI Clipper encryption devices to allow insiders to mount MitM attacks on targets such as Nortel; she allegedly extorted a gig with the board of directors at BC Hydro in December 2007; she allegedly extorted Larry Blain and fellow directors of BC Hydro into awarding the $73 million BC Hydro smart-grid contract to Corix Utilities, part of the Corix Group of Companies in which one of the biggest shareholders is CAI Capital Management where she is the managing director!]”
 80. Ann Romney (nee Davies) “[Revised June 27, 2012. Alleged Matrix 5 principal and Mormon wife of the allegedly-extorted man-in-the-middle Mormon, Mitt Romney; she allegedly secured a crony position as governor’s liaison to dirty money laundered by Kristine Marcy through the White House Office of Faith-Based and Community Initiatives; she allegedly used the money to build the Federal Bridge Certification Authority and pimp for the Fundamentalist Church of Jesus Christ of Latter-day Saints (FLDS) and the United Effort Plan (UEP) – both being Mormon pedophile sects linked to Bountiful, British Columbia, and SOS Children’s Villages in Canada; she allegedly used the money to fund Fast and Furious contract hits by Femme Comp Inc (FCI) assassins; she allegedly used the money to pay Mormon and Femme Comp hit teams for the murder of law enforcement officers and subversion of Mexican and United States governments; she allegedly used the Federal Bridges (cf. Entrust Ottawa and Sidley Austin, Chicago) to move pedophiles through B.C.’s Bountiful community and extort silence from terrified trustees of the Utah Retirement System re various naked short positions during 9/11 and the subprime panic of 2007; she allegedly extorted her husband’s partners and clients at Bain & Company through VideoGuard pay-per-view encryption devices which concealed conditional access to insider-trading information for the 9/11 panic of the capital markets; she allegedly extorted her husband’s partners and clients at Bain & Company through VideoGuard pay-per-view encryption devices of snuff-film images procured by pedophile pimps through the Bountiful community in British Columbia; she allegedly converted to The Church of Jesus Christ of Latter-day Saints in 1966 to take control of her future husband’s career; she allegedly conspired with Mitt’s father, George Romney, then Governor of Michigan, to move Mitt into a Mormon Mission Home mansion in Paris to learn the basic techniques of pedophile entrapment and man-in-the-middle propaganda; she allegedly used her future husband to help her lesbian friends to coordinate MitM attacks on the U.S. government and White House insiders in respect of their role in the Vietnam War; she allegedly used her future husband to help her lesbian friends to coordinate MitM attacks on French government leaders in respect of their role in the May 1968 general strike and student uprisings [cf. Jane ‘The Ripper’ Addams’ similar role in the University Settlement Movement through WWI]; she began attending Brigham Young University and then married Mitt Romney in 1969; she was First Lady of Massachusetts from 2003 to 2007; Ann Davies knew of Mitt Romney since elementary school; she began dating him in March 1965; she spent a semester at the University of Grenoble in France during her freshman year; after Mitt’s return from France in December 1968, the pair reconnected and agreed to get married as soon as possible; they were married by a church elder in a civil ceremony on March 21, 1969, at her Bloomfield Hills home, with a reception afterward at a local country club; the following day the couple flew to Utah for a wedding ceremony inside the Salt Lake Temple; her family could not attend since they were non-Mormons, but were present at a subsequent wedding breakfast held for them across the street; after Mitt graduated, the couple moved to Boston so that he could attend Harvard Business School and Harvard Law School; she later finished her undergraduate work by gaining a semester and half’s worth of credits via taking night courses at Harvard University Extension School, from which she graduated in 1975 with a Bachelor of Arts degree with a concentration in French language; she has been involved in a number of children’s charities, including being director of the inner city-oriented Best Friends; she worked extensively with the Ten Point Coalition in Boston and with other groups that promoted better safety and opportunities for urban youths; she has served as a board member for the United Way of America and helped found United Way Faith and Action; she was given the 2006 Lifetime Achievement Award from Salt Lake City-based Operation Kids. [Abel Danger alleges that Romney used pedophile federal bridge to mingle their wealth derived from naked short selling with fraudulently converted assets of the Utah Retirement System in Cayman Islands tax havens]”
80. Ann Romney (nee Davies) “[Revised June 27, 2012. Alleged Matrix 5 principal and Mormon wife of the allegedly-extorted man-in-the-middle Mormon, Mitt Romney; she allegedly secured a crony position as governor’s liaison to dirty money laundered by Kristine Marcy through the White House Office of Faith-Based and Community Initiatives; she allegedly used the money to build the Federal Bridge Certification Authority and pimp for the Fundamentalist Church of Jesus Christ of Latter-day Saints (FLDS) and the United Effort Plan (UEP) – both being Mormon pedophile sects linked to Bountiful, British Columbia, and SOS Children’s Villages in Canada; she allegedly used the money to fund Fast and Furious contract hits by Femme Comp Inc (FCI) assassins; she allegedly used the money to pay Mormon and Femme Comp hit teams for the murder of law enforcement officers and subversion of Mexican and United States governments; she allegedly used the Federal Bridges (cf. Entrust Ottawa and Sidley Austin, Chicago) to move pedophiles through B.C.’s Bountiful community and extort silence from terrified trustees of the Utah Retirement System re various naked short positions during 9/11 and the subprime panic of 2007; she allegedly extorted her husband’s partners and clients at Bain & Company through VideoGuard pay-per-view encryption devices which concealed conditional access to insider-trading information for the 9/11 panic of the capital markets; she allegedly extorted her husband’s partners and clients at Bain & Company through VideoGuard pay-per-view encryption devices of snuff-film images procured by pedophile pimps through the Bountiful community in British Columbia; she allegedly converted to The Church of Jesus Christ of Latter-day Saints in 1966 to take control of her future husband’s career; she allegedly conspired with Mitt’s father, George Romney, then Governor of Michigan, to move Mitt into a Mormon Mission Home mansion in Paris to learn the basic techniques of pedophile entrapment and man-in-the-middle propaganda; she allegedly used her future husband to help her lesbian friends to coordinate MitM attacks on the U.S. government and White House insiders in respect of their role in the Vietnam War; she allegedly used her future husband to help her lesbian friends to coordinate MitM attacks on French government leaders in respect of their role in the May 1968 general strike and student uprisings [cf. Jane ‘The Ripper’ Addams’ similar role in the University Settlement Movement through WWI]; she began attending Brigham Young University and then married Mitt Romney in 1969; she was First Lady of Massachusetts from 2003 to 2007; Ann Davies knew of Mitt Romney since elementary school; she began dating him in March 1965; she spent a semester at the University of Grenoble in France during her freshman year; after Mitt’s return from France in December 1968, the pair reconnected and agreed to get married as soon as possible; they were married by a church elder in a civil ceremony on March 21, 1969, at her Bloomfield Hills home, with a reception afterward at a local country club; the following day the couple flew to Utah for a wedding ceremony inside the Salt Lake Temple; her family could not attend since they were non-Mormons, but were present at a subsequent wedding breakfast held for them across the street; after Mitt graduated, the couple moved to Boston so that he could attend Harvard Business School and Harvard Law School; she later finished her undergraduate work by gaining a semester and half’s worth of credits via taking night courses at Harvard University Extension School, from which she graduated in 1975 with a Bachelor of Arts degree with a concentration in French language; she has been involved in a number of children’s charities, including being director of the inner city-oriented Best Friends; she worked extensively with the Ten Point Coalition in Boston and with other groups that promoted better safety and opportunities for urban youths; she has served as a board member for the United Way of America and helped found United Way Faith and Action; she was given the 2006 Lifetime Achievement Award from Salt Lake City-based Operation Kids. [Abel Danger alleges that Romney used pedophile federal bridge to mingle their wealth derived from naked short selling with fraudulently converted assets of the Utah Retirement System in Cayman Islands tax havens]”
 81. Sheila M. O’Grady “[Matrix 5 principal and former Chief of Staff of the allegedly extorted former man-in-the-middle Mayor of Chicago, Richard M. Daley, with whom she shared responsibility for the City’s $5 billion dollar annual budget and the management of nearly 40,000 employees spread over more than 40 city departments; she currently serves as the President of the Board of Directors of SOS Children’s Villages of Illinois, a charitable organization, allegedly set up by Canadian Privy Councilor Maurice Strong to help pedophile pimps entrap and extort city, state and federal government leaders during fraudulent election campaigns such as the one which put the Obamas into the White House; she allegedly oversaw the development of a former mattress factory in Chicago into an SOS Children’s Village for pedophiles; she allegedly hired tradesmen through the ‘Pickton’ Guild of Professional Home Services to install Entrust public key infrastructure (‘PKI’) bugging devices in the SOS Villages to record encounters between child and adult victims of a global pedophile entrapment and extortion matrix; she allegedly used Entrust public key infrastructure to contact pedophile members of Kristine Marcy’s Senior Executive Service and procure personnel records on Herman Cain; she allegedly ‘doctored’ these records and transferred them to the National Restaurant Association (NRA) to serve as a decoy front and support allegations that Cain was a ‘black’ sexual predator and knock him out of contention for the 2012 presidential elections and secure a second term for the less black Barack Hussein Obama; she is the President of the Illinois Restaurant Association, a non-profit trade association, allegedly controlled by City and ‘Rippergate’ Guilds of London Livery Companies including the Worshipful Company of Cooks; she has held various responsible positions with the City of Chicago including that of First Deputy Commissioner of the Department of Planning and Development and Director of Code Enforcement for the City’s Zoning Department; she holds an undergraduate degree from St. Mary’s College in Notre Dame, Indiana, where she majored in humanistic studies; a graduate degree from the London School of Economics [where she was allegedly recruited into a pedophile matrix, embedded in University Settlements and City and Guilds], where she concentrated her studies in urban planning; and a law degree from the University of Notre Dame]”
81. Sheila M. O’Grady “[Matrix 5 principal and former Chief of Staff of the allegedly extorted former man-in-the-middle Mayor of Chicago, Richard M. Daley, with whom she shared responsibility for the City’s $5 billion dollar annual budget and the management of nearly 40,000 employees spread over more than 40 city departments; she currently serves as the President of the Board of Directors of SOS Children’s Villages of Illinois, a charitable organization, allegedly set up by Canadian Privy Councilor Maurice Strong to help pedophile pimps entrap and extort city, state and federal government leaders during fraudulent election campaigns such as the one which put the Obamas into the White House; she allegedly oversaw the development of a former mattress factory in Chicago into an SOS Children’s Village for pedophiles; she allegedly hired tradesmen through the ‘Pickton’ Guild of Professional Home Services to install Entrust public key infrastructure (‘PKI’) bugging devices in the SOS Villages to record encounters between child and adult victims of a global pedophile entrapment and extortion matrix; she allegedly used Entrust public key infrastructure to contact pedophile members of Kristine Marcy’s Senior Executive Service and procure personnel records on Herman Cain; she allegedly ‘doctored’ these records and transferred them to the National Restaurant Association (NRA) to serve as a decoy front and support allegations that Cain was a ‘black’ sexual predator and knock him out of contention for the 2012 presidential elections and secure a second term for the less black Barack Hussein Obama; she is the President of the Illinois Restaurant Association, a non-profit trade association, allegedly controlled by City and ‘Rippergate’ Guilds of London Livery Companies including the Worshipful Company of Cooks; she has held various responsible positions with the City of Chicago including that of First Deputy Commissioner of the Department of Planning and Development and Director of Code Enforcement for the City’s Zoning Department; she holds an undergraduate degree from St. Mary’s College in Notre Dame, Indiana, where she majored in humanistic studies; a graduate degree from the London School of Economics [where she was allegedly recruited into a pedophile matrix, embedded in University Settlements and City and Guilds], where she concentrated her studies in urban planning; and a law degree from the University of Notre Dame]”
 82. Callista Louise Gingrich (née Bisek) “[Revised January 22, 2012. She is the wife of allegedly extorted man-in-the-middle former Speaker of the United States House of Representatives, Newt Gingrich; she married Gingrich on August 18, 2000 and, in 1999, testified that the couple began an affair in 1993, while he was still married; she allegedly procured VideoGuard pay-per-view encryption devices to conceal images of pedophile entrapment of her husband’s House associates and the extortion of actors who participated in a Wag the Dog propaganda broadcast during continuity of government exercises on 9/11; she allegedly extorted him to convert to Catholicism as a cover for his godless philandering; and the President of Gingrich Productions, a multimedia production company based in Washington, D.C.; she graduated cum laude from Luther College – an alleged sponsor of SOS Children’s Villages’ pedophile entrapment centers – in Decorah, Iowa, in 1988; she and her husband host and produce historical and public policy documentaries, editorials and advocacy films, allegedly for the purposes of man-in-the-middle attacks on faith-based and community initiatives; their alleged propaganda films include A City Upon a Hill, America at Risk, Nine Days that Changed the World, Ronald Reagan: Rendezvous with Destiny, Rediscovering God in America, Rediscovering God in America II: Our Heritage, and We Have the Power; she has voiced several audio books, allegedly including the man-in-the-middle propaganda titles To Save America, Valley Forge, 5 Principles for a Successful Life, Drill Here, Drill Now, Pay Less, The Art of Transformation, Real Change, Contract with the Earth, and Rediscovering God in America; she wrote Sweet Land of Liberty, an alleged children’s propaganda book about American exceptionalism featuring Ellis the Elephant; she is the president of the Gingrich Foundation, a charitable nonprofit corporation which established the Newt L. and Callista L. Gingrich Scholarship at Luther College, an alleged sponsor with the Hong Kong and Shanghai Banking Corporation of SOS Pedophile Villages; she is the former Washington, D.C.-based staffer of the allegedly-extorted gay man-in-the-middle President and CEO of the Council on Foundations, Steven Craig “Steve” Gunderson, a former Republican congressman from Wisconsin; she allegedly extorted Gunderson and his LGBTQ colleagues in the Council of Foundations into funding developments in DOJ Pride public key infrastructure which conceal the sale of the Fast and Furious weapon used to kill DEA agent Brian Terry]”
82. Callista Louise Gingrich (née Bisek) “[Revised January 22, 2012. She is the wife of allegedly extorted man-in-the-middle former Speaker of the United States House of Representatives, Newt Gingrich; she married Gingrich on August 18, 2000 and, in 1999, testified that the couple began an affair in 1993, while he was still married; she allegedly procured VideoGuard pay-per-view encryption devices to conceal images of pedophile entrapment of her husband’s House associates and the extortion of actors who participated in a Wag the Dog propaganda broadcast during continuity of government exercises on 9/11; she allegedly extorted him to convert to Catholicism as a cover for his godless philandering; and the President of Gingrich Productions, a multimedia production company based in Washington, D.C.; she graduated cum laude from Luther College – an alleged sponsor of SOS Children’s Villages’ pedophile entrapment centers – in Decorah, Iowa, in 1988; she and her husband host and produce historical and public policy documentaries, editorials and advocacy films, allegedly for the purposes of man-in-the-middle attacks on faith-based and community initiatives; their alleged propaganda films include A City Upon a Hill, America at Risk, Nine Days that Changed the World, Ronald Reagan: Rendezvous with Destiny, Rediscovering God in America, Rediscovering God in America II: Our Heritage, and We Have the Power; she has voiced several audio books, allegedly including the man-in-the-middle propaganda titles To Save America, Valley Forge, 5 Principles for a Successful Life, Drill Here, Drill Now, Pay Less, The Art of Transformation, Real Change, Contract with the Earth, and Rediscovering God in America; she wrote Sweet Land of Liberty, an alleged children’s propaganda book about American exceptionalism featuring Ellis the Elephant; she is the president of the Gingrich Foundation, a charitable nonprofit corporation which established the Newt L. and Callista L. Gingrich Scholarship at Luther College, an alleged sponsor with the Hong Kong and Shanghai Banking Corporation of SOS Pedophile Villages; she is the former Washington, D.C.-based staffer of the allegedly-extorted gay man-in-the-middle President and CEO of the Council on Foundations, Steven Craig “Steve” Gunderson, a former Republican congressman from Wisconsin; she allegedly extorted Gunderson and his LGBTQ colleagues in the Council of Foundations into funding developments in DOJ Pride public key infrastructure which conceal the sale of the Fast and Furious weapon used to kill DEA agent Brian Terry]”
83. Juliet Wheldon “[Revised January 2, 2012. Matrix 5 principal and Chief Legal Adviser to the allegedly extorted man-in-the-middle Governor of the Bank of England; she is a former HM Procurator General, Treasury Solicitor (‘TSol’) and Head of the Government Legal Service (2000–06) with root authority for contract killing by HMG Dope Inc. (Crown Agents); she allegedly served as Entrust root authority for cross-certification frauds by a matrix of Trusted Traders whose insurers, reinsurers, brokers and SWAT teams allegedly helped each other to trigger a Twin Towers catastrophe bond on 9/11; she and Yeuk-Si Tang (David Emerson’s Femme Comp wife – see #8), allegedly used TSol’s pig farm pension fund to buy the ‘Trusted Trader’ services of David Emerson, a “son-in-law of China”, a former Canadian foreign minister and the former director of Macdonald Dettwiler and Associates; she allegedly advised Kristine Marcy – see #1 – how to set up a revolving fund (DOJ # 15X4275) with ownerless goods donated by the drug trade in an MitM joint venture with the Treasury Solicitor to modify Con Air JPATS for VideoGuard-encrypted attacks on 9/11; she allegedly used VideoGuard encryption to synchronize TSol’s ownerless crime-scene images with Matrix 5 propaganda attacks triggered by the 7/7 bombings in London; she allegedly gave Matrix 5 insiders conditional access to TSol cat bonds triggered during pay-per-view VideoGuard snuff films on 7/7 and 9/11; she has allegedly set up a $73 trillion bona vacantia (ownerless) credit pool in the custody of the Treasury Solicitor and City Livery Companies to serve as a Carbon Disclosure Project to punish rebels and a Pig Farm Pension fund to enrich insiders; she is allegedly using VideoGuard-encryption devices to conceal the snuff-film pedophile trade in ownerless assets of SOS Children’s allegedly funded by Matrix 5 insiders in a racketeering joint venture with HSBC, the Bank of England and the Treasury Solicitor; she is allegedly using VideoGuard-encrypted snuff-film images in the Treasury Solicitor’s custody to extort the Bank of England Governor and Matrix 5 insiders into cat-bond pump and dump frauds during the ‘Global Financial Crisis’; she has allegedly deployed 1,400 lawyers to entrap and extort officials in 25 government departments, agencies and other organisations – ranging from the Home Office and the Ministry of Defence to the Competition Commission and the Office of Gas and Electricity Markets; she has allegedly extorted lawyers at MI5 and MI6 into silence in re the “Case of the Folded Spook”; she has allegedly arranged coercive injunctions to gag whistleblowers in the security and intelligence services when they threaten to break their duty of confidence; she has allegedly used VideoGuard encryption to adopt and adapt the Treasury Solicitor’s racketeering man-in-the-middle propaganda services to the Home Office which date back 160 years; she has years of expertise in setting up entrapment in phony divorce cases to enrich insiders as in bugging of Princess Diana up to the time of the contract hit or Sofitel in New York to entrap the former World Bank president Dominic Strauss; she was a former Legal Adviser to allegedly-extorted men-in-the middle officials in the Home Office (1997–2000); Former Legal Secretary to the allegedly-extorted Law Officers’ Department (1989–97) where she helped force the integration of U.K. foreign policy, military, criminal justice and judicial cooperation into the Maastricht Treaty and spoliated evidence of Crown Sister Hillary Clinton’s role in the Export of Defence Equipment and Dual-Use Goods to Iraq; Former Legal Adviser to allegedly-extorted Department of the Treasury Solicitor (1987–89) where she allegedly helped to spoliate evidence from the Pan Am 103 crime scene; Former staffer to Law Officers’ Department (1986–87); Former Assistant Legal Secretary to Department of the Treasury Solicitor (1984–86); Former staffer to Law Officers’ Department (1983–84); Former Advisory Division in Department of the Treasury Solicitor (1976–83); she matriculated at LMH Oxford University in 1968 where she read Modern History; her former Treasury Solicitor’s post dates at least as far back as 1661 and gave her access to a well proven M.O. for Matrix 5 extortion of top government officials through pedophile oath-taking ceremonies allegedly introduced into America in 1776 by founders of a Greek Life community at William and Mary College and introduced into the United Kingdom in the same year by founders of the Bullingdon Club at Oxford University.”
84. Dame Elish Frances Angiolini (née McPhilomy) “[Dame Angiolini is a Matrix 5 principal who allegedly directs the pedophile entrapment and extortion of man-in-the-middle officials in the offices of the Lord Advocate, the Solicitor General and the Procurator Fiscal (Public Prosector) of Scotland; she grew up in Govan, Glasgow in a working class family; she studied at the School of Law of the University of Strathclyde where she obtained an LLB in 1982 and a Diploma in Legal Practice in 1983; she allegedly began radicalizing and intimidating witnesses and victims while training at the Crown Office and Procurator Fiscal Service as a Procurator Fiscal (public prosecutor); after her training, she spent 8 years as a Deputy Procurator Fiscal in Airdrie, prosecuting in Airdrie Sheriff Court; in 1992, she began working for Crown Agents when was seconded to the Crown Office where she worked in the Lord Advocate’s Secretariat; in this role, she allegedly adopted a stolen copy of PROMIS to track and intimidate adult and child victims and witnesses; she was then appointed Senior Depute Procurator Fiscal at Glasgow, taking operational responsibility for Sheriff and Jury prosecutions; she was promoted to Assistant Procurator Fiscal at Glasgow in 1995; she allegedly began worked on the illegal transfer of PROMIS to the International Association of Prosecutors – the only global non-governmental organisation of prosecutors, established by the United Nations in 1995, Vienna; she allegedly helped the United Nations insider to track and protect the principals of transnational crime including drug trafficking, money laundering and the pedophile trade through SOS Children’s Villages sponsored by lessors and lessees based at Canada Square, Canay Wharf; she returned to the Crown Office as Head of Policy in 1997 and began to integrate PROMIS with the U.K. MoD’s Federal Bridge to track the guilty track the innocent through databases associated with Interpol phony crime scene investigations; she was appointed Regional Procurator Fiscal for Grampian, Highland and Islands (based at Aberdeen) on 27 July 2000; in this role she allegedly piloted a victim tracking schems with PROMIS and the Federal Bridge which has subsequently been extended across the country; in 2001, shortly after the MoD’s Federal Bridge was used to conceal perpetrators of the 9/11 man-in-the-middle attacks on America, she was appointed Solicitor General for Scotland by Field McConnell’s namesake, First Minister Jack McConnell; she was the first solicitor, as opposed to advocate, to be appointed Solicitor General to the objections of amongst all members of the extorted (?) legal profession; she was nominated for the post of Lord Advocate and her nomination was passed by Parliament on 5 October 2006, with 99 in favour, 0 against and 15 abstentions; she was sworn in at the Court of Session on 12 October 2006 and one month later she was made a member of the Privy Council thereby joining a ‘Star Chamber’ group which had allegedly extorted control over the UK MoD’s PKI root authority over the stolen copy of PROMIS and its use in the Federal Bridge in murder-for-hire; she allegedly extorted leaders of the SNP administration and Alex Salmond, the First Minister to let her keep her post of Lord Advocate albeit depriving her of her seat in Cabinet; she had her reappointment agreed by Parliament on 24 May 2007 making her the first Lord Advocate to serve two different governments; she clashed later in 2007 with the head of Scotland’s judiciary, Lord President Hamilton, over the collapse of the World’s End murders trial where the trial judge, Lord Clarke, had ruled there was insufficient evidence for the jury to convict and threw the case out; she made a statement to the Scottish Parliament, saying she was “disappointed” at the decision, a move Hamilton said undermined the independence of the judiciary; she announced in October 2010 that she would step down from the role of Lord Advocate after the Scottish Parliament elections in May 2011 but Abel Danger believes that she is still defrauding innocent victims through the use of PROMIS and the Federal Bridge to sabotage prosecutions and shelter the guilty.]”
 85. Courtney Banks (nee?) “[Revised May 29, 2012. Courtney Banks is the Matrix 5 principal of a Missing Children PYSYOPS program financed by the DOJ’s Asset Forfeiture Fund and the 2007 founder and Chief Executive Officer of Nat’l Security Associates WorldWide (NSAWW); she allegedly procured the North Face sports bag used to transport the body of GCHQ-code breaker Gareth Williams to his home in Pimlico, through a supply chain which moves ‘sedated assets’ under the PSYOPS program which she set up as an intern with the Clinton White House; she is the alleged director of an extorted man-in-the-middle senior leadership team at NSAWW with a combined eighteen decades of public service and business experience working in intelligence, defense, transportation and border security, preparedness and response, and law enforcement; Banks allegedly worked with Kristine Marcy on the use of Clipper chips and Nortel’s Joint Automated Booking Station (JABS) to spoliate evidence of a home break-in and torture murder of JonBenet Ramsey on Christmas Day, 1996 in Boulder, Colorado; she allegedly used images of the murder to extort concessions from the directors of Lockheed Martin, Siemens, Serco, Keane and many other Fortune 500 corporations; prior to founding NSAWW, she worked across the public and private homeland/national security sectors – from the White House and Department of Justice, to the world’s largest defense contractors; she served as Vice President of Homeland Security for Raytheon Company where she allegedly developed Missing Children PSYOPS programs for the company’s homeland security business in North America, the Middle East, Eastern and Western Europe, and Asia; prior to Raytheon, she served as Director of Homeland Systems Solutions for Lockheed Martin and used the Missing Children PSYOPS to subvert the company’s homeland security/homeland defense business; prior to joining Lockheed Martin, she served as an independent national security consultant to the federal government and private corporations; in 2000, she allegedly extorted President Clinton to place her in the Office of the Assistant Secretary of Defense for Special Operations /Low Intensity Conflict as Assistant in Charge of Global Terrorism Issues in the anti-terrorism directorate and prepare the 9/11 attacks; prior to this appointment, she served as the program manager for the Inter Agency Response Awareness Program for the Office of the Assistant Secretary of Defense for Special Operations /Low Intensity Conflict in the counter-terrorism directorate and drew up the continuity of governmet protocols tested in Amalgam Virgo on June 1-2, 2001; prior to this she acted as the Director of Force Health Protection for the Gulf War Illness Task Force in the Department of Defense, in which capacity she also served as a subject matter expert on PSYOPS to undermine procedures for combat stress management; she developed the principles of Missing Child PSYOPS while working with Kristine Marcy and Hillary Clinton in the Department of Justice in the Antitrust Criminal Division and for the Office of Chief Counsel in the White House; she appears regularly in national and trade media – Business Week, the Washington Business Journal, Town and Country magazine, CBS news, etc. – as a sought after(?) speaker on national security and business issues; she serves on the ASIS Council for Combating Terrorism, Violence and Political Instability; she was the Chair of the 2010 Hope for the Warriors “Got Heart Give Hope” annual black tie gala; she served on the 2010 Host Committee for the National Center for Missing and Exploited Children (NCMEC) Annual Golf Tournament; she was a Finalist for the 2010 Ernst & Young Entrepreneurial Winning Women award and was the 2010 winner of the “Heroines in Technology” AFCEA/March of Dimes Award; she has guest lectured at many colleges and universities and is published on the subject of Agro-Terrorism where she allegedly coordinated the anthrax letter attack on Congress; she holds a MA in National Security Studies from Georgetown University where she allegedly attended or directed Delta Phi Epsilon pedophile oath-taking rituals associated with Ordo Templi Orientis (O.T.O.) – a secret society headed at one time by Aleister Crowley – which inducted Madeleine Albright; she holds a BA, with honors, in Military History from the University of Pennsylvania. She resides with her family in the metro Washington, D.C. area.]”
85. Courtney Banks (nee?) “[Revised May 29, 2012. Courtney Banks is the Matrix 5 principal of a Missing Children PYSYOPS program financed by the DOJ’s Asset Forfeiture Fund and the 2007 founder and Chief Executive Officer of Nat’l Security Associates WorldWide (NSAWW); she allegedly procured the North Face sports bag used to transport the body of GCHQ-code breaker Gareth Williams to his home in Pimlico, through a supply chain which moves ‘sedated assets’ under the PSYOPS program which she set up as an intern with the Clinton White House; she is the alleged director of an extorted man-in-the-middle senior leadership team at NSAWW with a combined eighteen decades of public service and business experience working in intelligence, defense, transportation and border security, preparedness and response, and law enforcement; Banks allegedly worked with Kristine Marcy on the use of Clipper chips and Nortel’s Joint Automated Booking Station (JABS) to spoliate evidence of a home break-in and torture murder of JonBenet Ramsey on Christmas Day, 1996 in Boulder, Colorado; she allegedly used images of the murder to extort concessions from the directors of Lockheed Martin, Siemens, Serco, Keane and many other Fortune 500 corporations; prior to founding NSAWW, she worked across the public and private homeland/national security sectors – from the White House and Department of Justice, to the world’s largest defense contractors; she served as Vice President of Homeland Security for Raytheon Company where she allegedly developed Missing Children PSYOPS programs for the company’s homeland security business in North America, the Middle East, Eastern and Western Europe, and Asia; prior to Raytheon, she served as Director of Homeland Systems Solutions for Lockheed Martin and used the Missing Children PSYOPS to subvert the company’s homeland security/homeland defense business; prior to joining Lockheed Martin, she served as an independent national security consultant to the federal government and private corporations; in 2000, she allegedly extorted President Clinton to place her in the Office of the Assistant Secretary of Defense for Special Operations /Low Intensity Conflict as Assistant in Charge of Global Terrorism Issues in the anti-terrorism directorate and prepare the 9/11 attacks; prior to this appointment, she served as the program manager for the Inter Agency Response Awareness Program for the Office of the Assistant Secretary of Defense for Special Operations /Low Intensity Conflict in the counter-terrorism directorate and drew up the continuity of governmet protocols tested in Amalgam Virgo on June 1-2, 2001; prior to this she acted as the Director of Force Health Protection for the Gulf War Illness Task Force in the Department of Defense, in which capacity she also served as a subject matter expert on PSYOPS to undermine procedures for combat stress management; she developed the principles of Missing Child PSYOPS while working with Kristine Marcy and Hillary Clinton in the Department of Justice in the Antitrust Criminal Division and for the Office of Chief Counsel in the White House; she appears regularly in national and trade media – Business Week, the Washington Business Journal, Town and Country magazine, CBS news, etc. – as a sought after(?) speaker on national security and business issues; she serves on the ASIS Council for Combating Terrorism, Violence and Political Instability; she was the Chair of the 2010 Hope for the Warriors “Got Heart Give Hope” annual black tie gala; she served on the 2010 Host Committee for the National Center for Missing and Exploited Children (NCMEC) Annual Golf Tournament; she was a Finalist for the 2010 Ernst & Young Entrepreneurial Winning Women award and was the 2010 winner of the “Heroines in Technology” AFCEA/March of Dimes Award; she has guest lectured at many colleges and universities and is published on the subject of Agro-Terrorism where she allegedly coordinated the anthrax letter attack on Congress; she holds a MA in National Security Studies from Georgetown University where she allegedly attended or directed Delta Phi Epsilon pedophile oath-taking rituals associated with Ordo Templi Orientis (O.T.O.) – a secret society headed at one time by Aleister Crowley – which inducted Madeleine Albright; she holds a BA, with honors, in Military History from the University of Pennsylvania. She resides with her family in the metro Washington, D.C. area.]”
86. Baroness Noakes DBE “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of leaders of churches, government and industry; she was appointed a Reuters Trustee in 1998; she is a non-executive director of Carpetright plc (since 2001), Severn Trust plc (since 2008) and the Royal Bank of Scotland Group plc (since 2011); she was an elected member of the Council of the Institute of Chartered Accountants in England and Wales from 1987 to 2002 and its first woman President in 1999/2000. Baroness Noakes was awarded a DBE in 1996 and made a life peer in 2000. Past appointments include: non-executive director of Imperial Chemical Industries PLC (2004–2008), non-executive director of the Court of the Bank of England (1994–2001 including senior non-executive 1998–2001); she was an allegedly corrupt member of Advisory Council of the Institute of Business Ethics (1998 – 2003); she was an allegedly corrupt Commissioner of the Public Works Loan Board (1995–2001); she was an allegedly corrupt Governor of the London Business School (1998–2001) and Eastbourne College (2000–5); Board member of Social Market Foundation (2002–4); she was an allegedly corrupt non-executive member of the Inland Revenue’s Management Board (1992–99); she was an allegedly corrupt non-executive member of the NHS Policy Board (1992–95), the Chancellor of the Exchequer’s Private Finance Panel (1993–97) and the government’s Public Services Productivity Panel (1998–2000); she joined Peat, Marwick, Mitchell & Co. (now KPMG) in 1970 as an articled clerk and qualified as a Chartered Accountant in 1973; she was a partner in KPMG from 1983 to 2000 and allegedly conspired with Vicky Huhne in developing a Thomson Reuters Wag the Dog story for the massive attacks of 9/11; she was educated at the University of Bristol (Bachelor of Laws).]”
 87. Mary Cirillo “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of Thomson Reuters and its Libor banking cartel; she was Chair and Chief Executive Officer of Opcenter, LLC, an Internet consulting firm, from 2000 to 2003; prior to that, she was a senior banking executive at Bankers Trust and Citibank for over 20 years and engineered Citibanks racketeering role in Libor and its position on the UK MoD’s Federal Bridge Certification Authority prior to 9/11; she is a member of the Advisory Board of Hudson Venture Partners, L.P., a venture capital firm, and serves on the boards of several cultural and educational organizations; she has a BA from Hunter College; she is a director of DealerTrack Holdings, Inc., ACE Ltd., the re-insurance company which allegedly set up pass-through certificate with Citi/Travelers for the Twin Towers double-occurrence demolition on 9/11]”
87. Mary Cirillo “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of Thomson Reuters and its Libor banking cartel; she was Chair and Chief Executive Officer of Opcenter, LLC, an Internet consulting firm, from 2000 to 2003; prior to that, she was a senior banking executive at Bankers Trust and Citibank for over 20 years and engineered Citibanks racketeering role in Libor and its position on the UK MoD’s Federal Bridge Certification Authority prior to 9/11; she is a member of the Advisory Board of Hudson Venture Partners, L.P., a venture capital firm, and serves on the boards of several cultural and educational organizations; she has a BA from Hunter College; she is a director of DealerTrack Holdings, Inc., ACE Ltd., the re-insurance company which allegedly set up pass-through certificate with Citi/Travelers for the Twin Towers double-occurrence demolition on 9/11]”
88. Lawton Fitt “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of Thomson Reuters and its Libor banking cartel and associated private equity groups; she joined the board of Reuters in 2004; she served as Secretary (CEO) of the Royal Academy of Arts London from 2002 to 2005; she was an investment banker with Goldman Sachs & Co., where she became a partner in 1994 and a managing director in 1996; she is a trustee or director of several not-for-profit organizations; she has a bachelor’s degree from Brown University and an MBA from the University of Virginia; she is a board member of CIENA Corporation and The Progressive Corporation; she is a board member of The Carlyle Group, which, in an alleged conspiracy with Reuters trustee, John McArthur, and his fellow special investors in the CAI Private Equity Group, organized the Wag the Dog attack of 9/11 with the Worshipful Livery Companies]”
 89. Dame Helen Alexander “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of Thomson Reuters and its Libor banking cartel and associated private equity groups; she was appointed a Reuters Trustee in 2011; she is chairman of UBM plc, the Port of London Authority (PLA) and Incisive Media; she is deputy chairman of esure Group Holdings; she is a non-executive director of Rolls-Royce Group plc; she is a senior adviser to Bain Capital and allegedly arranged for Mitt Romney’s profits to be hidden in tax shelters set up by Sidley Austin in the Cayman Islands; she was president of the Confederation of British Industry (CBI) until June 2011; she is Chancellor of the University of Southampton; she is associated with MitM attacks through the WorldWide Web Foundation, the Grand Palais in Paris, the Said Business School in Oxford and St Paul’s Girls’ School; she was Chief Executive of the Economist Group till 2008, having joined the company in 1985 when she allegedly began working with Barack Obama’s Rainbow Coalition in Chicago on the development of a leveraged Libor lease to finance the demolition of the Twin Towers on 9/11; she was managing director of the Economist Intelligence Unit from 1993 to 1997.]”
89. Dame Helen Alexander “[Matrix 5 principal and alleged sponsor of lesbian and/or pedophile man-in-the-middle extortionists of Thomson Reuters and its Libor banking cartel and associated private equity groups; she was appointed a Reuters Trustee in 2011; she is chairman of UBM plc, the Port of London Authority (PLA) and Incisive Media; she is deputy chairman of esure Group Holdings; she is a non-executive director of Rolls-Royce Group plc; she is a senior adviser to Bain Capital and allegedly arranged for Mitt Romney’s profits to be hidden in tax shelters set up by Sidley Austin in the Cayman Islands; she was president of the Confederation of British Industry (CBI) until June 2011; she is Chancellor of the University of Southampton; she is associated with MitM attacks through the WorldWide Web Foundation, the Grand Palais in Paris, the Said Business School in Oxford and St Paul’s Girls’ School; she was Chief Executive of the Economist Group till 2008, having joined the company in 1985 when she allegedly began working with Barack Obama’s Rainbow Coalition in Chicago on the development of a leveraged Libor lease to finance the demolition of the Twin Towers on 9/11; she was managing director of the Economist Intelligence Unit from 1993 to 1997.]”
 90. Monique Villa “[Matrix 5 principal and alleged extortionist behind Thomson Reuters’ man-in-the-middle attacks on Libor banks, including Barclays (LGBT Gareth Williams), HSBC (Fast and Furious) and Bank of America (WTC#7); she was formerly managing director of Reuters Media; she is chairman of Action Images, a specialist sports photography agency acquired by Reuters in September 2005; she joined Reuters in 2000 to manage the picture and text news business for the Reuters News Agency where she was allegedly responsible for snuff-film feeds associated with al-Qaeda 9/11; she allegedly negotiated deals for Media and Editorial to get Libor man-in-the-middle propaganda inserted into the International Herald Tribune print and online business pages; she allegedly used her senior journalistic and management positions in Agence France Presse (AFP) as a cover to stage IRA/Al-Qaeda snuff-film bombing campaigns in Paris, Rome, London and Ireland; she allegedly used her 1996 position as director of strategy and business development at the AFP headquarters in Paris to build an ‘al-Qaeda’ partnership with Thomson Reuters and its Libor panel banks vested in DoJ Asset Forfeiture Fund and the presidential candidacies of Barack Obama and Mitt Romney; she studied Law and Political Science and has a Diploma from the Paris Centre de Formation Des Journalistes]”
90. Monique Villa “[Matrix 5 principal and alleged extortionist behind Thomson Reuters’ man-in-the-middle attacks on Libor banks, including Barclays (LGBT Gareth Williams), HSBC (Fast and Furious) and Bank of America (WTC#7); she was formerly managing director of Reuters Media; she is chairman of Action Images, a specialist sports photography agency acquired by Reuters in September 2005; she joined Reuters in 2000 to manage the picture and text news business for the Reuters News Agency where she was allegedly responsible for snuff-film feeds associated with al-Qaeda 9/11; she allegedly negotiated deals for Media and Editorial to get Libor man-in-the-middle propaganda inserted into the International Herald Tribune print and online business pages; she allegedly used her senior journalistic and management positions in Agence France Presse (AFP) as a cover to stage IRA/Al-Qaeda snuff-film bombing campaigns in Paris, Rome, London and Ireland; she allegedly used her 1996 position as director of strategy and business development at the AFP headquarters in Paris to build an ‘al-Qaeda’ partnership with Thomson Reuters and its Libor panel banks vested in DoJ Asset Forfeiture Fund and the presidential candidacies of Barack Obama and Mitt Romney; she studied Law and Political Science and has a Diploma from the Paris Centre de Formation Des Journalistes]”
91. Sally Shelton-Colby “[Matrix 5 principal and alleged man-in-the-middle extortionist of leaders of America’s intelligence services; she was a Vice President of Bankers Trust Co. in New York City; she allegedly served BT as a co-sponsor of the Libor project in the City of London to manage the bank’s political risk in developing countries during the third world debt crisis of the 1980s; she allegedly arranged the 1996 contract hit of her husband William Colby, a former director of the Central Intelligence Agency; she allegedly had him killed to protect a conspiracy she was developing with then-CIA director, John Deutsch, for the British Bankers Association’s Libor Project 9/11; she is allegedly running a Fast and Furious cover-up project for USAID and the Government of Mexico in Mexico City; she has been Deputy Secretary-General of the Organization for Economic Cooperation and Development (OECD) in Paris, France; she has been Assistant Administrator of the Bureau for Global Programs at the U.S. Agency for International Development; she has been U.S. Ambassador to Grenada, Barbados and several other Eastern Caribbean nations; she has been Deputy Assistant Secretary of State for Latin America and the Caribbean; and Legislative Assistant for Foreign Policy to then-Senator (later Secretary of the Treasury) Lloyd Bentsen; she is a member of the Council on Foreign Relations and the American Academy of Diplomacy; she has served on the Boards of Directors of Valero Energy Corporation, a Fortune 500 company and the world’s largest oil and gas pipeline company, and the Baring Puma Fund, a closed-ended fund traded on the London Stock exchange and engaged in acquiring emerging market equities; she has served on a number of non-profit Boards of Directors, including Helen Keller International, Helen Keller International Europe (where she was also president), the National Endowment for Democracy, the International Planned Parenthood Federation, the National Democratic Institute for International Affairs, the Atlantic Council of the U.S., the Center for International Environmental Law, the American Committee for Aid to Poland, the American Hospital of Paris, and the Pan American Health and Education Foundation, among others; she was one of the founders and first Chairman of the Board of Directors of UNAIDS, a U.N. entity which coordinates the HIV-AIDS prevention programs of the World Bank, the WHO, UNICEF, UNDP, and UNFPA; she served on two White House Commissions: the Gore-Chernomyrdin Commission (Russia), where she was Vice Chair of the Committee on Health and the Committee on Agriculture, and the Gore-Mubarak (Egypt) Commission where she was Co-Chair of the Committee on Education]”
 92. Book-end: Theresa Mary May (née Brasier) [Revised June 30, 2012. An alleged Matrix 5 principal who allegedly uses pedophile surveillance, entrapment and extortion to control man-in-the-middle officials in the police, religious, military and civilian organizations in the United Kingdom; she allegedly sponsored same sex agents to infiltrate City and Guilds Livery Companies and create a de facto Worshipful Company of Blackmailers; she allegedly authorized the Blackmailers to hire Anna Chapman – a same-sex pedophile pimp – to entrap Barclays and Thomson Reuters staff in LIBOR insider trading frauds which recently generated £290 million in fines to enrich FSA and DOJ Forfeiture funds; she is a British Conservative politician who is Home Secretary in the Conservative – Liberal Democrat Coalition; she was elected to Parliament in 1997 as the Member of Parliament for Maidenhead; she served as the Chairman of the Conservative Party, 2003–04; she was appointed to the Privy Council in 2003; she became Shadow Secretary of State for Work and Pensions and Shadow Minister for Women before being appointed Home Secretary and the Minister for Women and Equality in David Cameron’s Cabinet on 11 May 2010; she attended the University of Oxford where she read Geography at St Hugh’s College, taking a BA (Hons) in 1977; she worked from 1977 to 1983 at the Bank of England; she worked as a financial consultant and senior advisor in International Affairs at the Association for Payment Clearing Services; she allegedly conspired with Juliet Wheldon to undermine the Treasury Solicitor’s office with leveraged leases financed by ‘bona vacantia’ credit; she stood (and lost) in the safe Labour seat of North West Durham in the 1992 general election; she stood and lost in the 1994 Barking by-election; she was elected the Conservative MP for Maidenhead in 1997 general election; she was Shadow Spokesman for Schools, Disabled People and Women (1998 – June 1999) in William Hague’s front-bench Opposition team; she became the first of the 1997 MPs to enter the Shadow Cabinet when in 1999 she was appointed Shadow Education and Employment Secretary; after the 2001 election, the new Conservative leader Iain Duncan Smith retained her services in the Shadow Cabinet, moving her to the Transport portfolio; she allegedly knew of the City and Guilds plans to trigger the double-occurrence for the Wells Fargo Twin Towers pass through certificates; she became first female chairman of the Conservative Party in July 2002; she stated at the 2002 Conservative Party Conference that the party must change because it was perceived as the “Nasty Party”; she was sworn of the Privy Council in 2003; she was appointed Home Secretary and Minister for Women and Equality by the Prime Minister of the United Kingdom, David Cameron as part of his first cabinet; she is tireless sponsor of gender equality; she pretends to oppose the European Union (Eurosceptic); she plans to scrap the UK Human Rights Act; she received the Freedom of the City of London; she has joined the Livery of the Worshipful Company of Marketors which allegedly conspired with Bain and Company’s London Office in structuring the leveraged lease triggers to the Global Financial Crisis of 2008
92. Book-end: Theresa Mary May (née Brasier) [Revised June 30, 2012. An alleged Matrix 5 principal who allegedly uses pedophile surveillance, entrapment and extortion to control man-in-the-middle officials in the police, religious, military and civilian organizations in the United Kingdom; she allegedly sponsored same sex agents to infiltrate City and Guilds Livery Companies and create a de facto Worshipful Company of Blackmailers; she allegedly authorized the Blackmailers to hire Anna Chapman – a same-sex pedophile pimp – to entrap Barclays and Thomson Reuters staff in LIBOR insider trading frauds which recently generated £290 million in fines to enrich FSA and DOJ Forfeiture funds; she is a British Conservative politician who is Home Secretary in the Conservative – Liberal Democrat Coalition; she was elected to Parliament in 1997 as the Member of Parliament for Maidenhead; she served as the Chairman of the Conservative Party, 2003–04; she was appointed to the Privy Council in 2003; she became Shadow Secretary of State for Work and Pensions and Shadow Minister for Women before being appointed Home Secretary and the Minister for Women and Equality in David Cameron’s Cabinet on 11 May 2010; she attended the University of Oxford where she read Geography at St Hugh’s College, taking a BA (Hons) in 1977; she worked from 1977 to 1983 at the Bank of England; she worked as a financial consultant and senior advisor in International Affairs at the Association for Payment Clearing Services; she allegedly conspired with Juliet Wheldon to undermine the Treasury Solicitor’s office with leveraged leases financed by ‘bona vacantia’ credit; she stood (and lost) in the safe Labour seat of North West Durham in the 1992 general election; she stood and lost in the 1994 Barking by-election; she was elected the Conservative MP for Maidenhead in 1997 general election; she was Shadow Spokesman for Schools, Disabled People and Women (1998 – June 1999) in William Hague’s front-bench Opposition team; she became the first of the 1997 MPs to enter the Shadow Cabinet when in 1999 she was appointed Shadow Education and Employment Secretary; after the 2001 election, the new Conservative leader Iain Duncan Smith retained her services in the Shadow Cabinet, moving her to the Transport portfolio; she allegedly knew of the City and Guilds plans to trigger the double-occurrence for the Wells Fargo Twin Towers pass through certificates; she became first female chairman of the Conservative Party in July 2002; she stated at the 2002 Conservative Party Conference that the party must change because it was perceived as the “Nasty Party”; she was sworn of the Privy Council in 2003; she was appointed Home Secretary and Minister for Women and Equality by the Prime Minister of the United Kingdom, David Cameron as part of his first cabinet; she is tireless sponsor of gender equality; she pretends to oppose the European Union (Eurosceptic); she plans to scrap the UK Human Rights Act; she received the Freedom of the City of London; she has joined the Livery of the Worshipful Company of Marketors which allegedly conspired with Bain and Company’s London Office in structuring the leveraged lease triggers to the Global Financial Crisis of 2008